UIUCTF-wp
MISC
Sanity Check
- 题目描述如下:加入Discord,在Discord上找flag
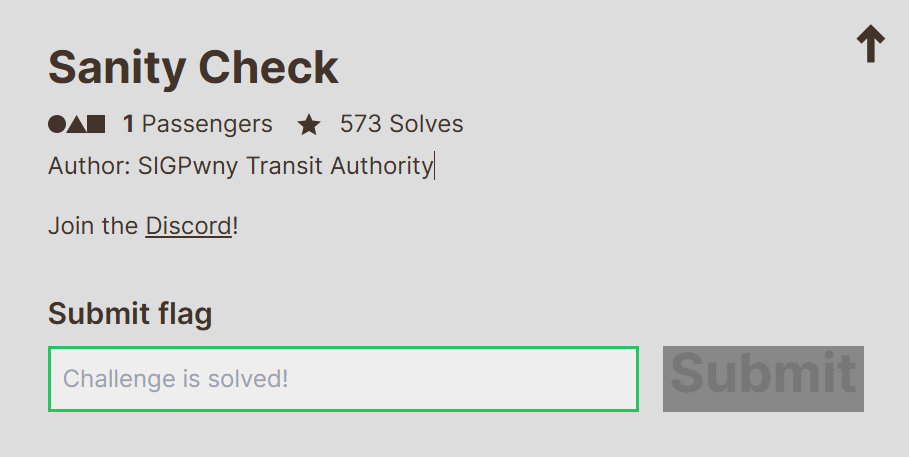
- 加入后在此处找到flag:
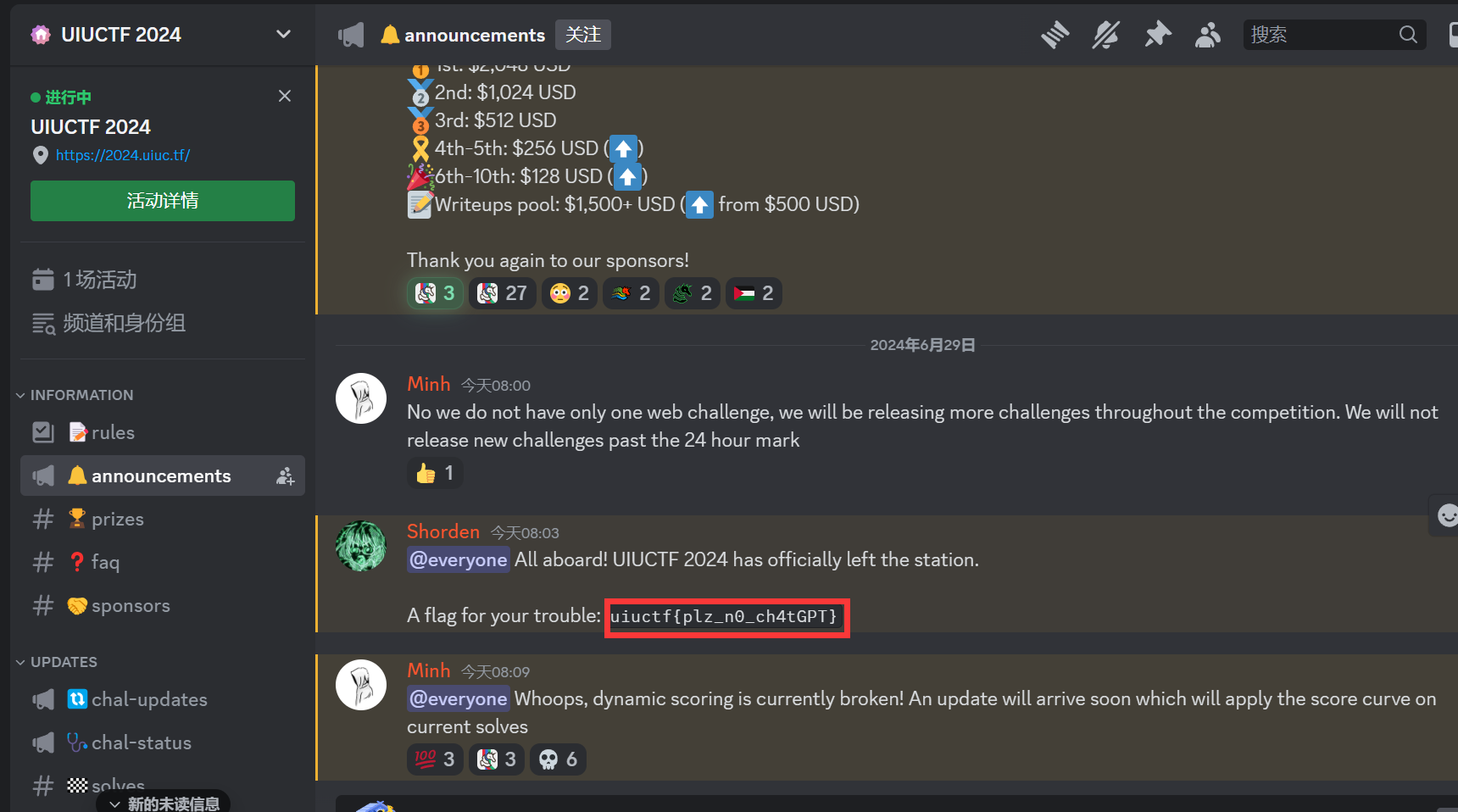
uiuctf{plz_n0_ch4tGPT}
CRYPTO
X Marked the Spot
- 题目:给了个python代码和异或生成的密文(二进制文件)
- python代码如下:
1 | from itertools import cycle |
-
思路:由flag的格式可以知道flag的前7位字符串
uiuctf{这时可以将密文的前7个字节提取出来,按顺序与uiuctf{异或操作,然后后之间可以得到key的前7为,然后最后一位采取爆破。在爆破的密文找到最后一位是}的字符串即可得到flag -
exp:
1 | # 以二进制读取模式打开文件ct |
Without a Trace
-
题目是关于一个矩阵的,而且是靶机题,需要nacat到靶机上
-
题目附件给了关于矩阵的一些运算,让用户输入一个对角矩阵。flag被分成5份,第n份被放在第n行第n列,也构成一个对角矩阵
-
将这两个对角矩阵相乘,然后最后将输出相乘后对角矩阵的迹(矩阵对角元素的和)
-
原理后就是简单的解方程题目了,直接就系数
1 1 1 1 1和2 1 1 1 1和1 2 1 1 1和1 1 2 1 1和1 1 1 2 1和1 1 1 1 2解出每块flag的数值即可
1 | import numpy as np |
- 下面是nc输入的过程
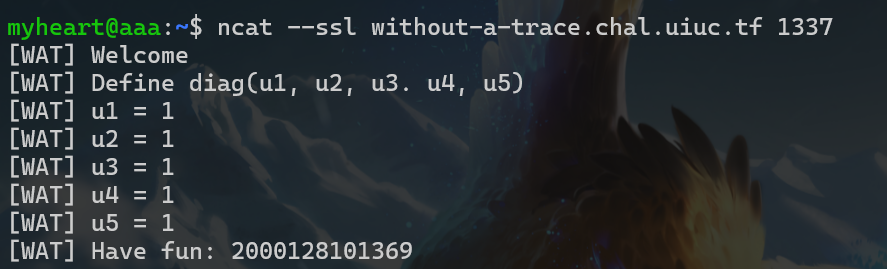
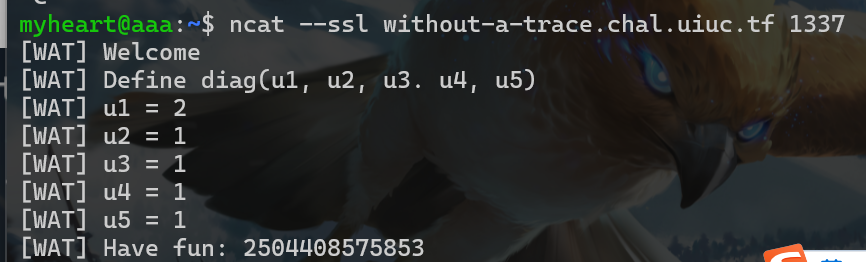
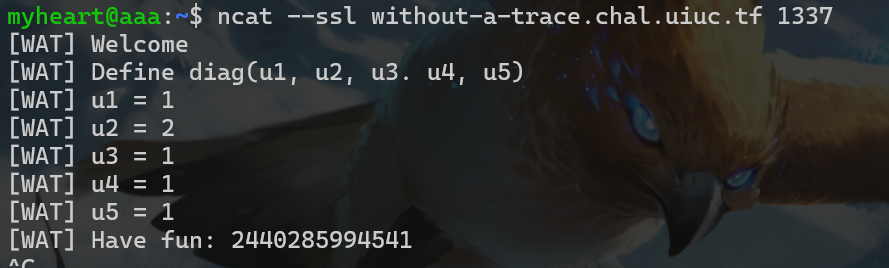
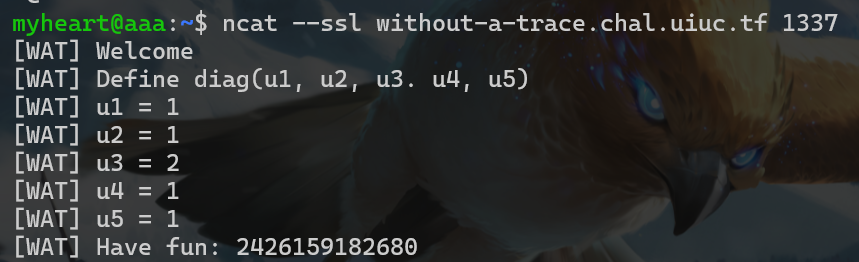
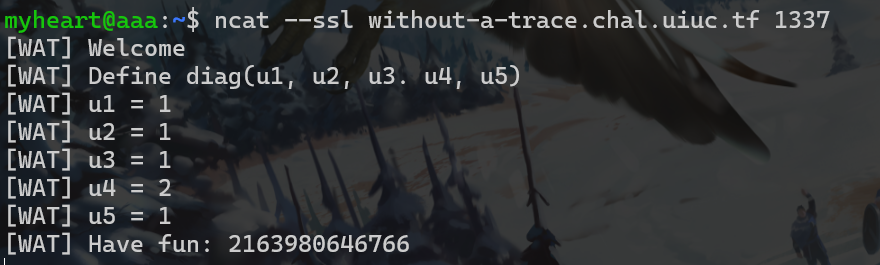
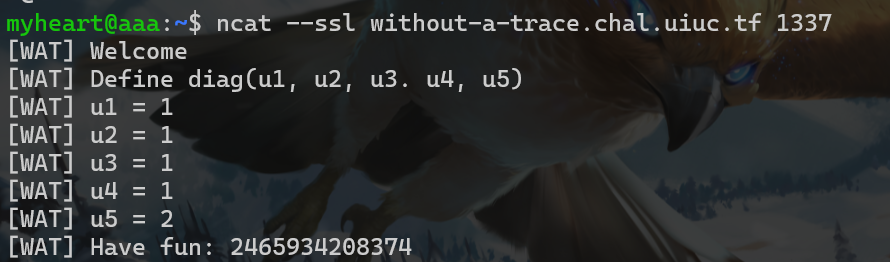
- 得到这些值后,直接写python解出flag
1 | import libnum |
Determined
- 还是一个靶机题目,nc过去获取数据,本质考点还是具有公共素数,求两数的最大公因数。
- 题目描述
- 题目给了三个附件
- server附件:将rsa加密的p、q还有另外的一个r放在矩阵里面,然后让用户输入矩阵中某些地方的值,计算出5阶方阵的行列式
1 | from Crypto.Util.number import bytes_to_long, long_to_bytes |
- gen附件:一眼rsa加密
1 | n = 158794636700752922781275926476194117856757725604680390949164778150869764326023702391967976086363365534718230514141547968577753309521188288428236024251993839560087229636799779157903650823700424848036276986652311165197569877428810358366358203174595667453056843209344115949077094799081260298678936223331932826351 |
- gen.py附件
1 | from SECRET import FLAG, p, q, r |
- 根据提示用户输入的地方可以输入0和1构造行列式的值为
p*r(或-p*r)和p*q(或-p*q)’
| p | 0 | 0 | 0 | 0 |
|---|---|---|---|---|
| 0 | 1 | 0 | 0 | 0 |
| 0 | 0 | 0 | 0 | 1 |
| 0 | q | 0 | r | 0 |
| 0 | 0 | 1 | 0 | 0 |
(泄露pr或-pr)
| p | 0 | 0 | 0 | 0 |
|---|---|---|---|---|
| 0 | 0 | 0 | 1 | 0 |
| 0 | 0 | 0 | 0 | 1 |
| 0 | q | 0 | r | 0 |
| 0 | 0 | 1 | 0 | 0 |
- 然后得到下图结果
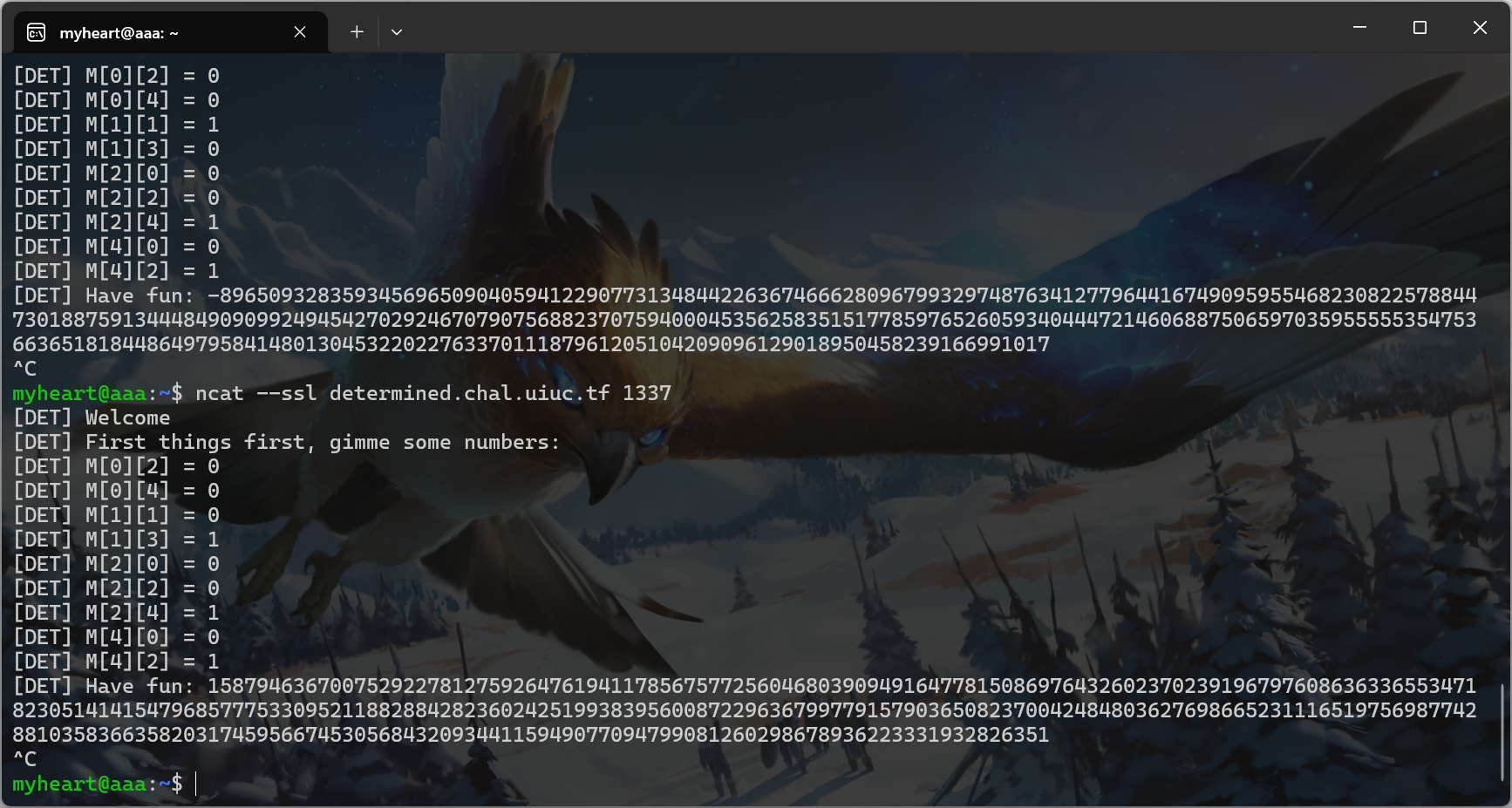
- 之后之间正常rsa解密即可
1 | import libnum |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 iyheart的博客!
评论

