moeCTF--wp
MISC
signin
- misc果然是脑洞题,我不是很做的来
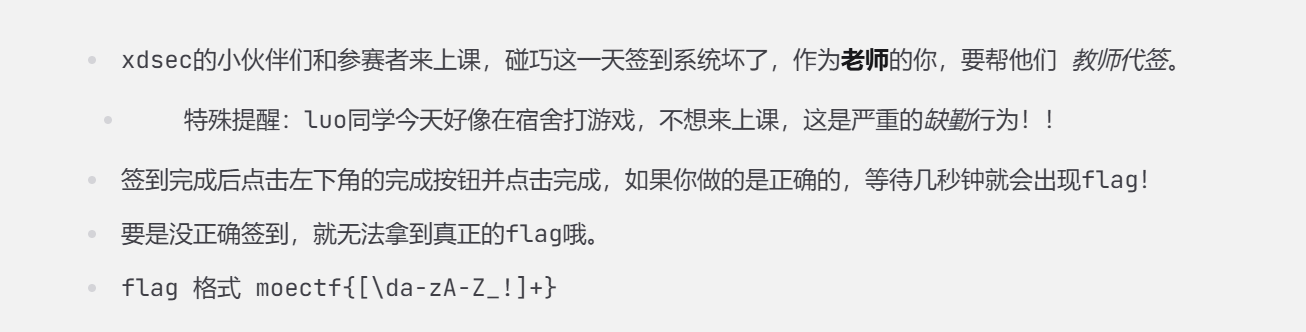
- 已签和未签的如下
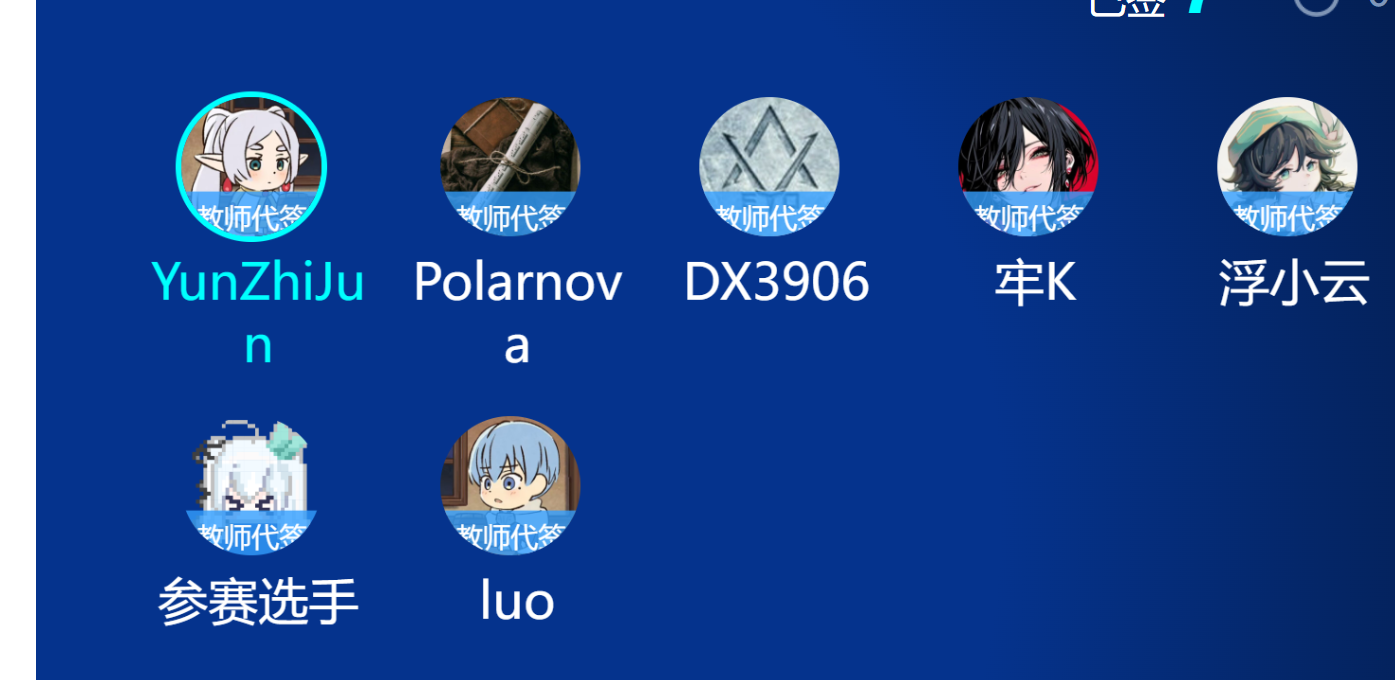
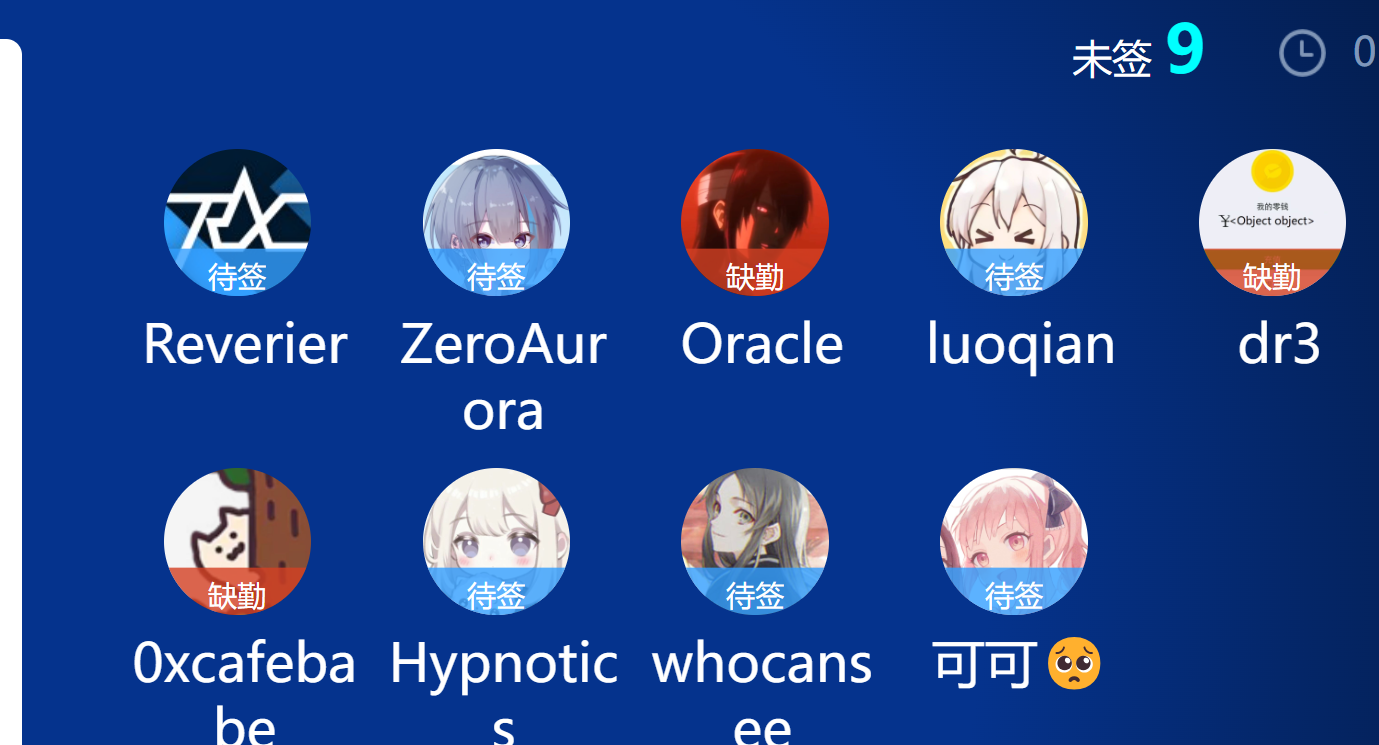
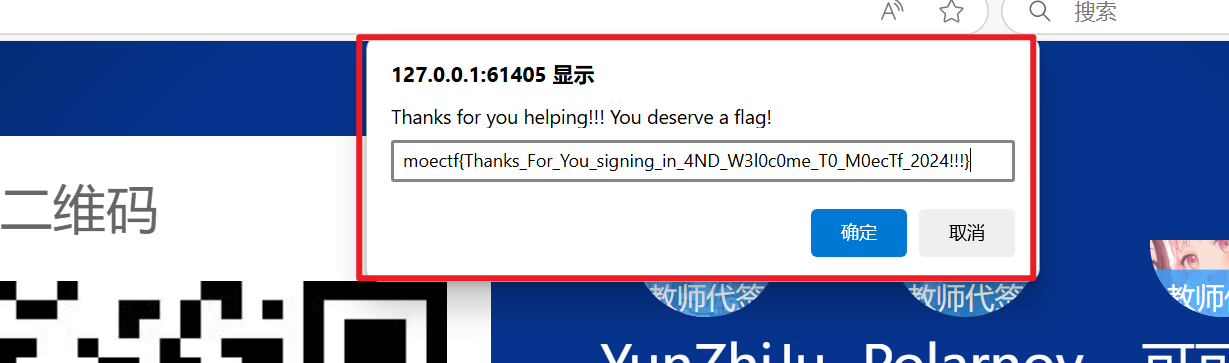
- 按照题目要求,直接就把luo记为缺勤,把其他人都签到了,即可得到flag,
moectf{Thanks_For_You_signing_in_4ND_W3l0c0me_T0_M0ecTf_2024!!!}
ez_Forensics
-
下载附件,看到是一个
.raw文件,题目也说了是内存取证,所以我决定使用Linux下的volatility进行取证 -
题目描述中给了提示,在关闭
cmd之前ubw保存了电脑的内存镜像
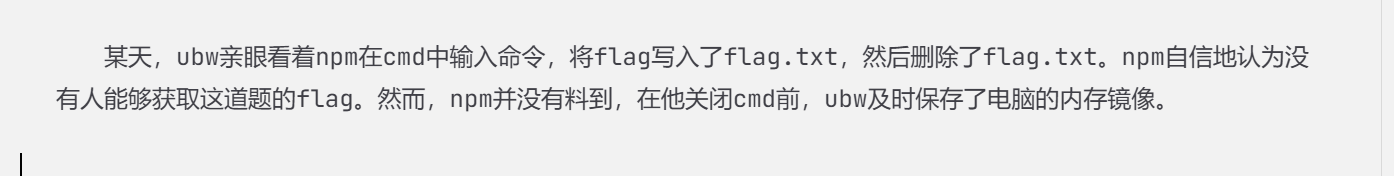
- 题目给出了
cmd是Windows下的终端,现在我要先使用volatility -f ./flag.raw imageinfo命令查看一下该.raw文件的信息 - 发现是可能是这些操作系统
Win7SP1x64, Win7SP0x64, Win2008R2SP0x64, Win2008R2SP1x64_24000, Win2008R2SP1x64_23418, Win2008R2SP1x64, Win7SP1x64_24000, Win7SP1x64_23418 - 经过筛查是
Win7SP1x64
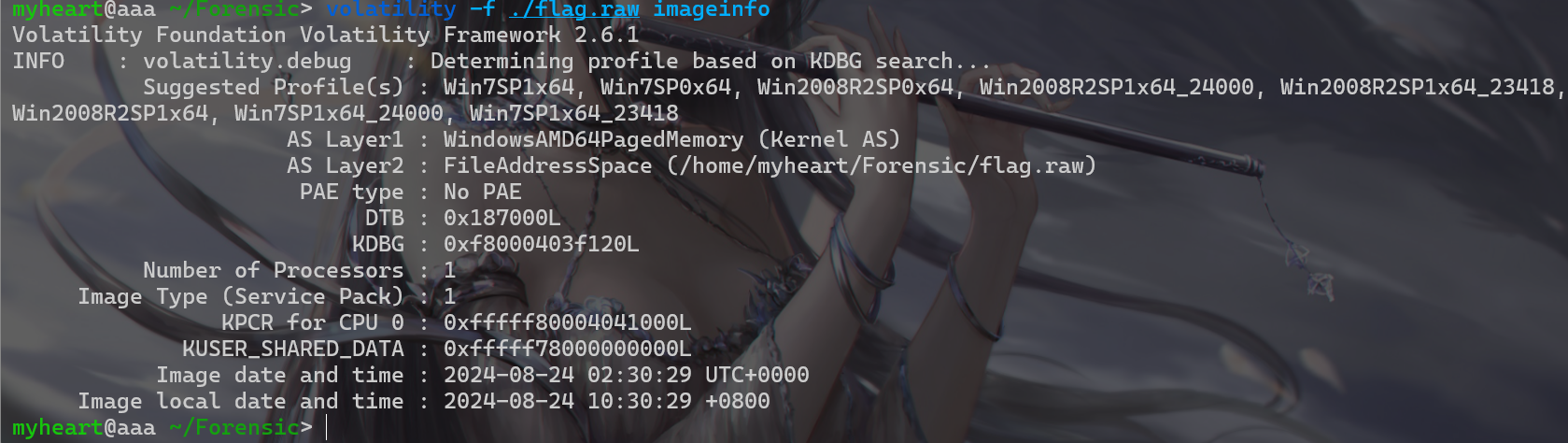
- 然后再使用
volatility -f /home/myheart/Forensic/flag.raw --profile=Win7SP1x64 pslist命令提取进程 - 发现
cmd.exe为PID 344 PPID 2148 Thds 1 Hnds20 Sess 1 - 从而确认了
cmd.exe有在进程中运行
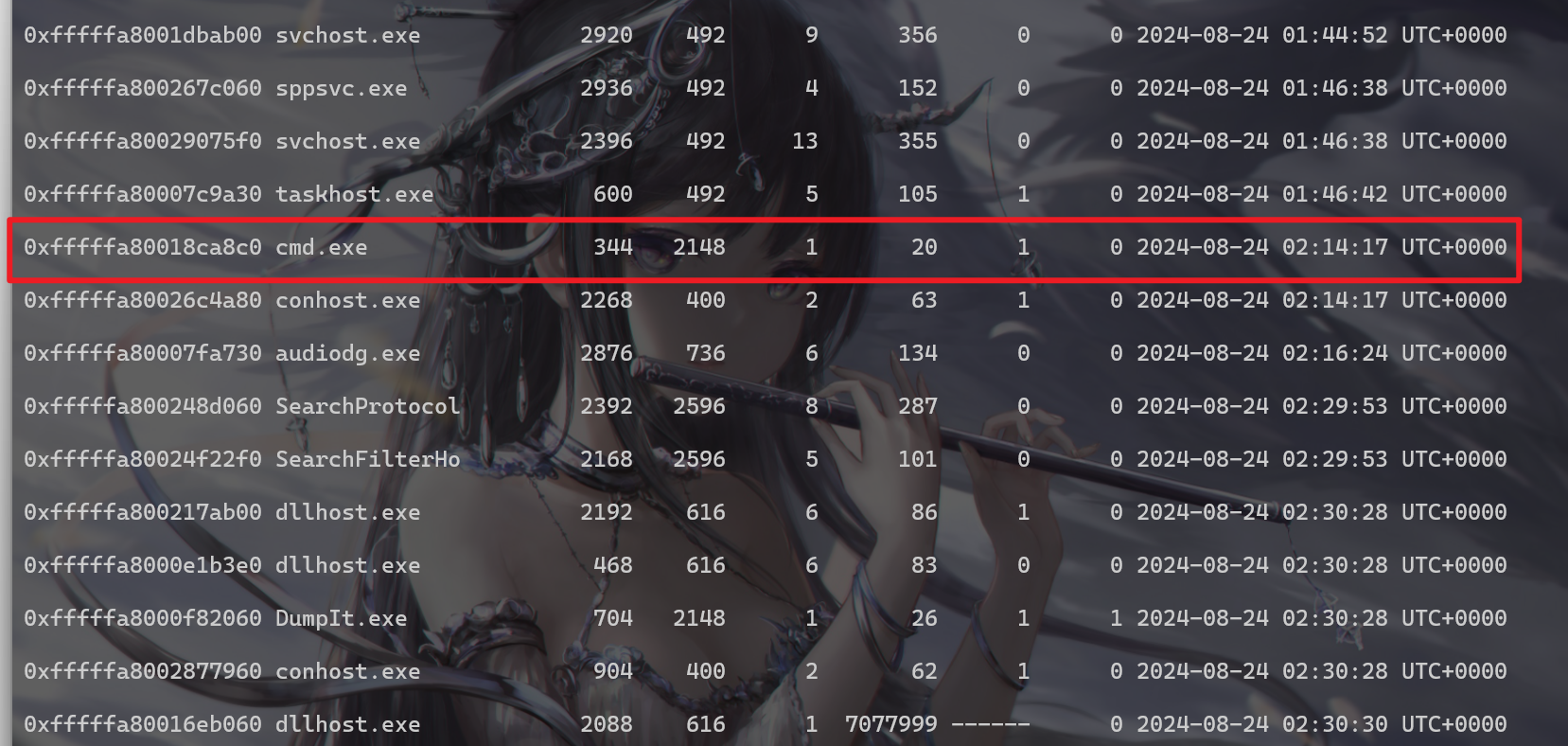
- 然后再使用
volatility -f /home/myheart/Forensic/flag.raw --profile=Win7SP1x64 cmdscan cmdscan是一个插件,用于查找cmd.exe(命令提示符)相关的命令历史记录。它会扫描内存中的数据,以寻找用户在命令提示符中输入的命令。然后发现有npm将flag写入flag.txt文件的历史记录,并且还可以看到flag的具体内容
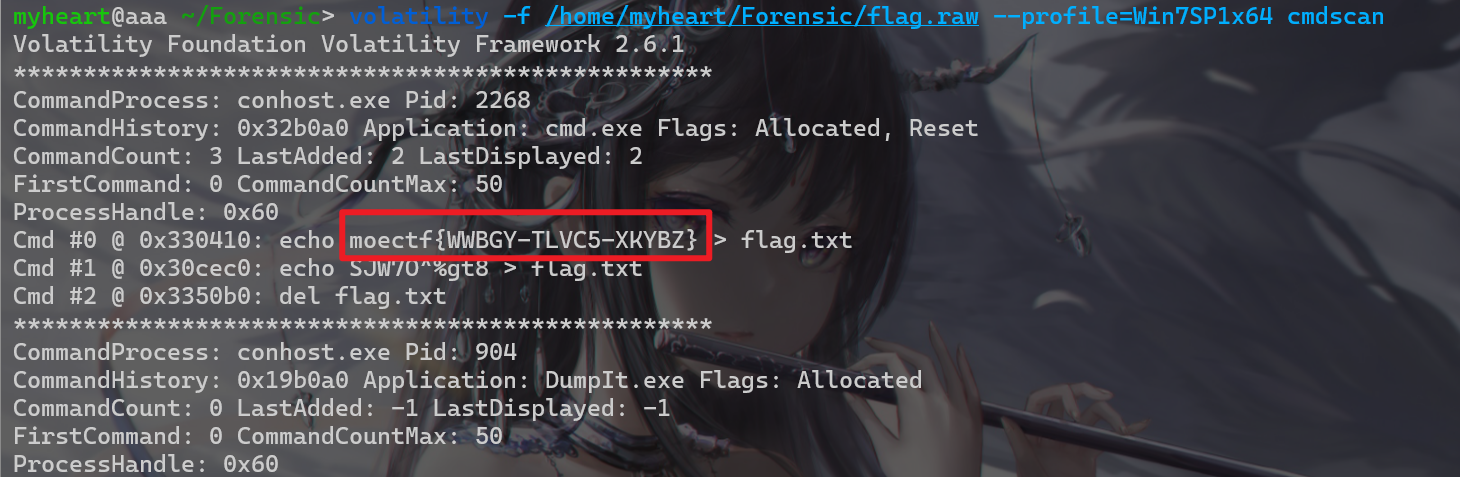
- 所以得到flag为
moectf{WWBGY-TLVC5-XKYBZ}
WEB
Web渗透测试与审计入门指北
- 下载pdf,浏览一遍pdf,在最后会看到一个附件,搭建网站就有flag
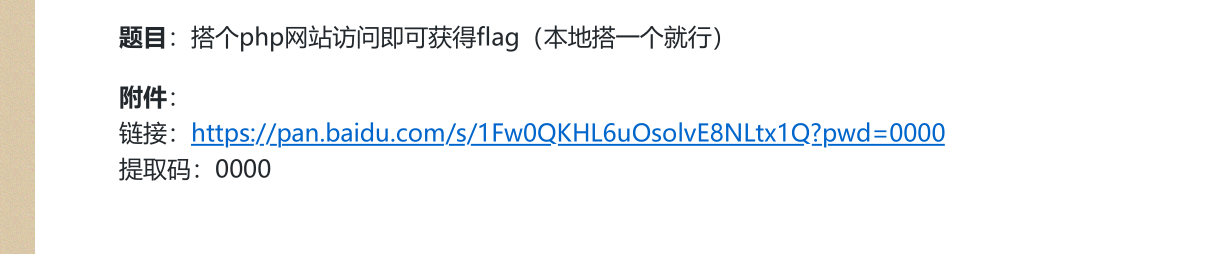
- 下载好phpstudy,然后启动一些服务
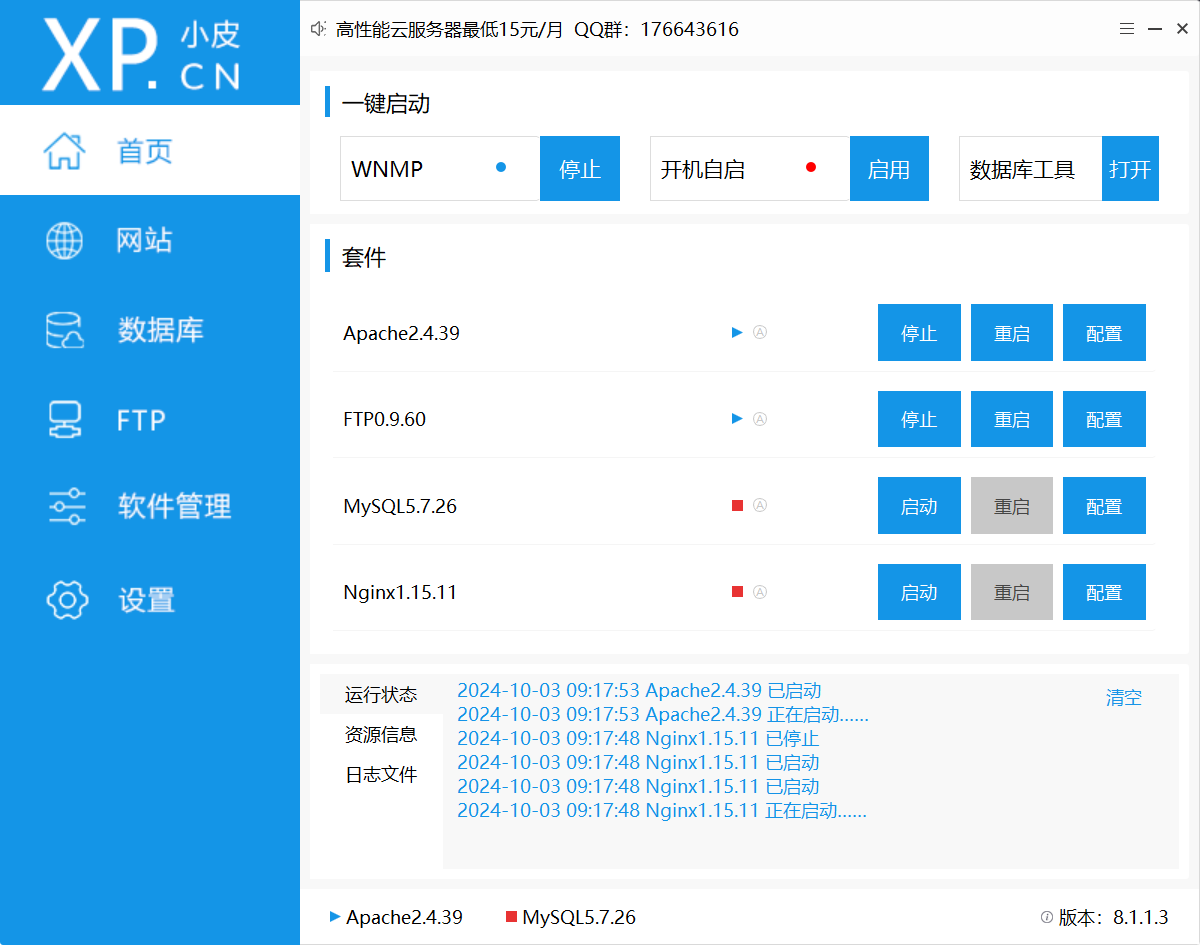
- 点击网站,再点击管理,打开根目录,将附件给的东西复制粘贴过去
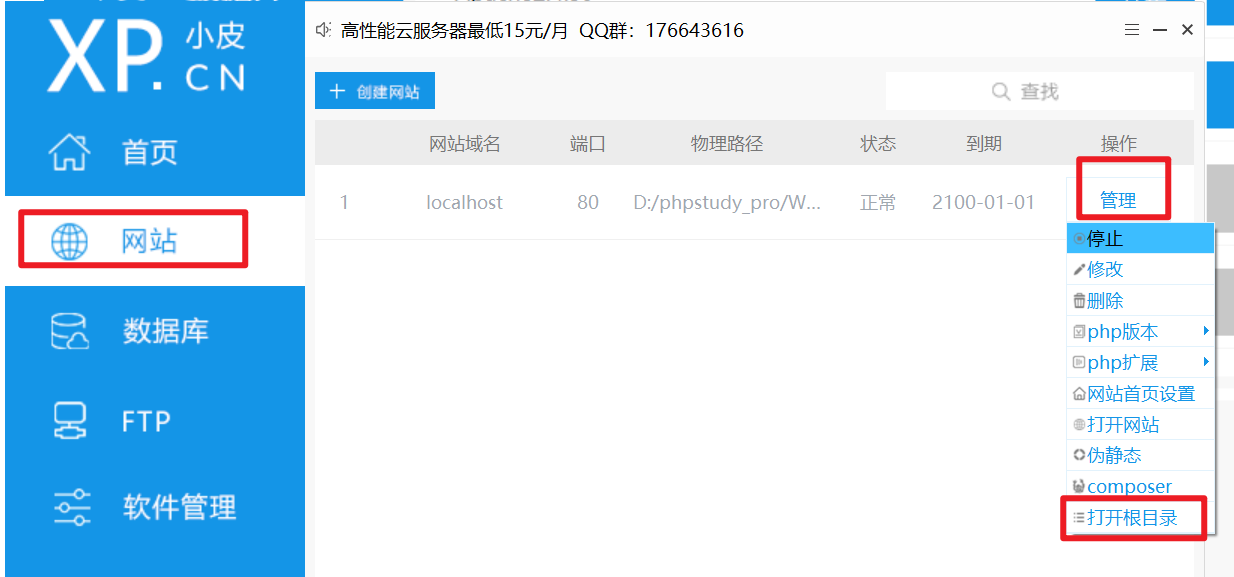
- 这样再选择打开网站,就会得到flag
- 网站如下,flag:
moectf{H3r3'5_@_flYinG_kIss_f0r_yoU!}
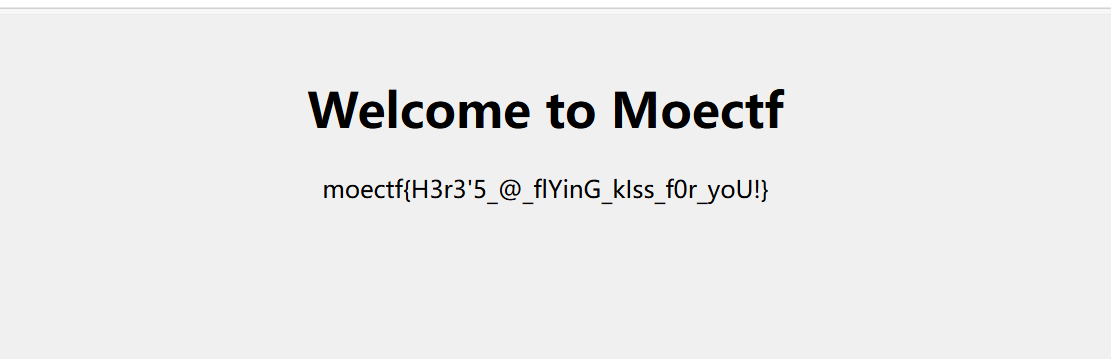
弗拉格之地的入口
- 打开环境,进入环境对应的网站,会出现如下的提示

- 看到有爬虫字样,我想到了Python课讲到爬虫时会有一个爬虫协议,一般都是在网站的
robots.txt这个网页下
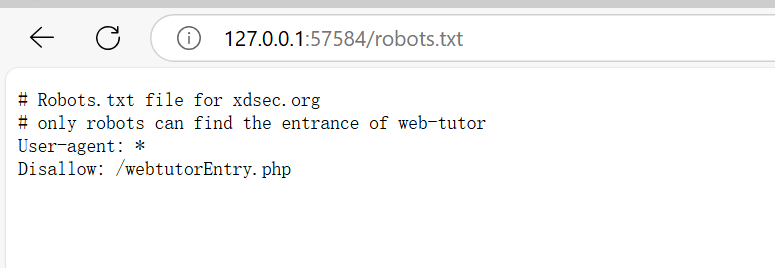
- 进入网页果然看到了一些信息,发现这里面给出了一个
/webtutorEntry.php,进入这个文件对应的网页 - 进入后就会看到flag了
moectf{cONGraTU1atioN_foR_Kn0w1ng_RoboTS-txT250f2}
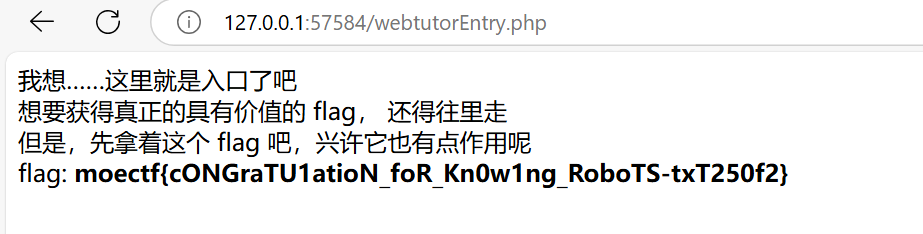
弗拉格之地的挑战
垫刀之路01: MoeCTF?启动!
- 打开题目可以看到,这里已经是
getshell了,并且可以输出执行命令的结果
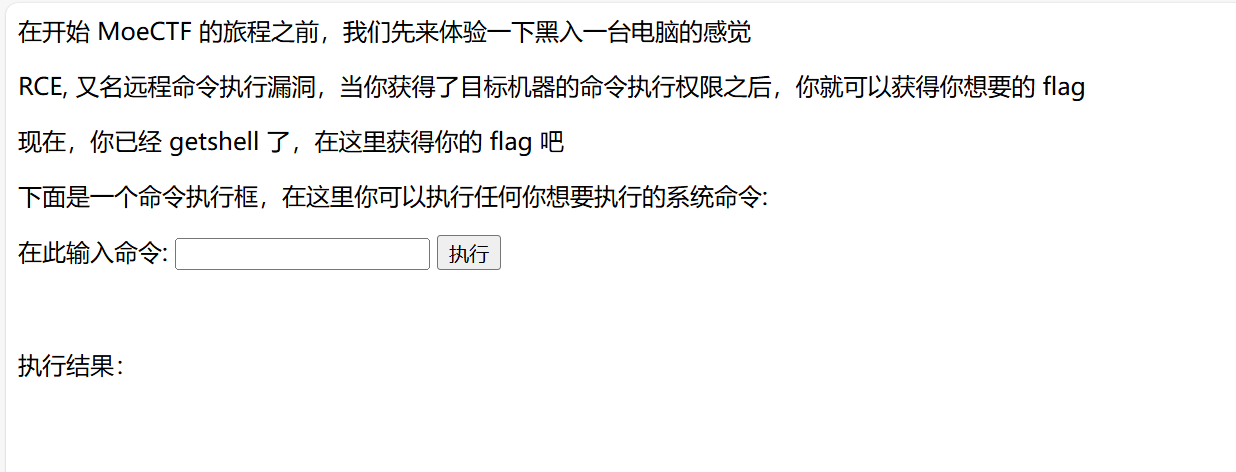
- 然后先
ls,查看一下该目录,发现是web网页的后端代码,这里应该是在web目录下
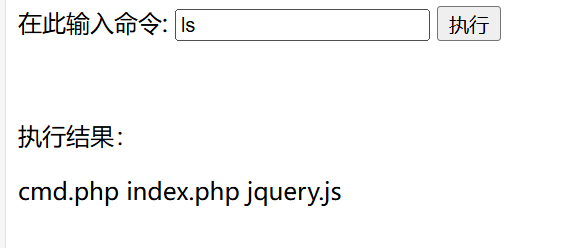
- 我这边直接
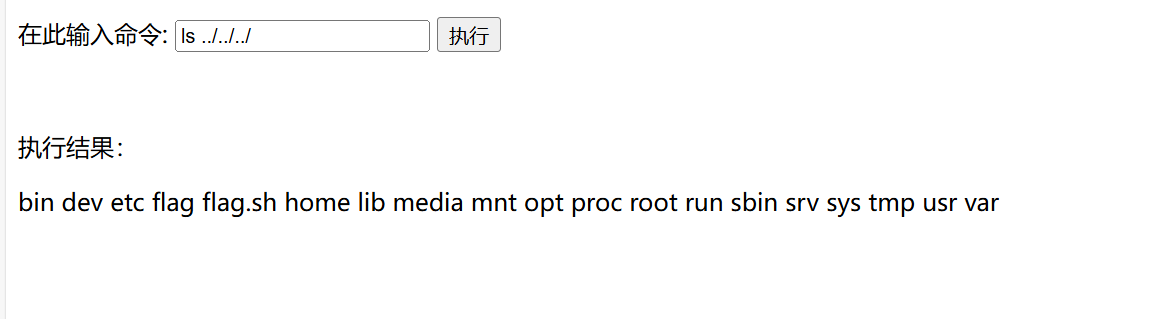
ls ../../../,查看到了根目录下有flag,cat flag后却发现flag不再这里面,在环境变量里面
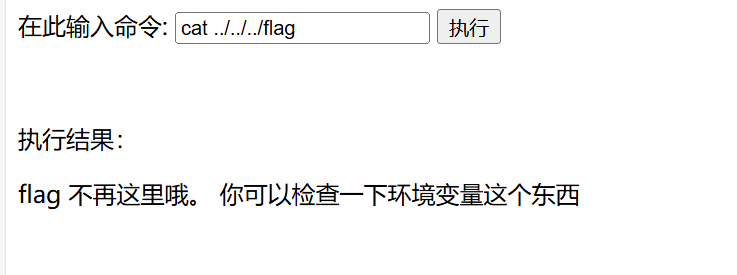
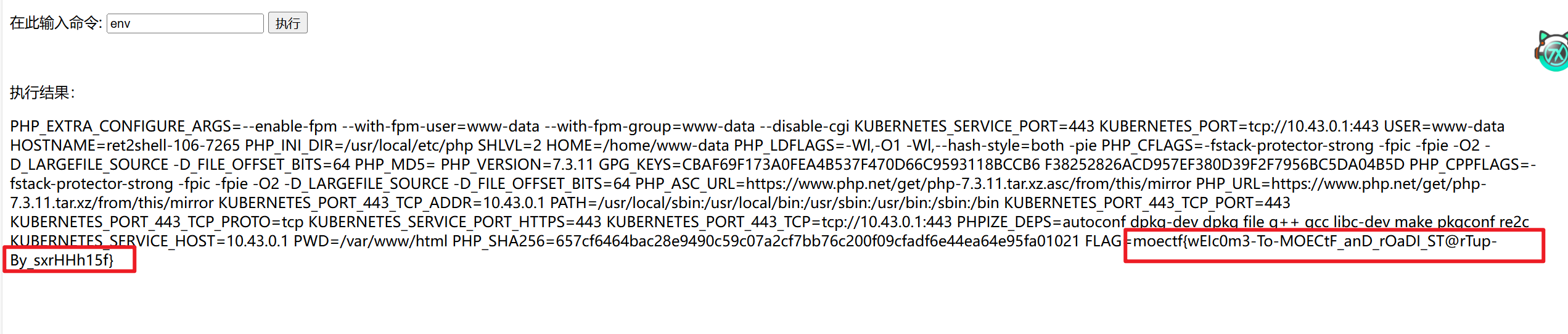
- 所以我又执行了
env发现环境变量里面有flag,这样flag就找到了,flagmoectf{wEIc0m3-To-MOECtF_anD_rOaDI_ST@rTup-By_sxrHHh15f}
ez_http
- 打开环境,环境这边显示着要使用
post方法,这么一看就需要burp进行抓包了

- 抓包到后的http包是这样的
1 | GET / |
- 使用post参数
1 | POST / |
- 又看到提示,要求
POST参数要imoau=sb

- 上网搜了下,
POST参数要放在Priority: u=0, i需要空一行,即post头结束后要空一行,然后Content-Length: 8这一行内容burp在发送时会自动补全,这边遇到问题,怎么发包都发不过去(问题是第二次做(复现)的时候遇到的,第一次做没遇到这个问题)。问题出来我没有使用burp的右键修改方法,而是直接手动修改POST参数导致发包出现问题。
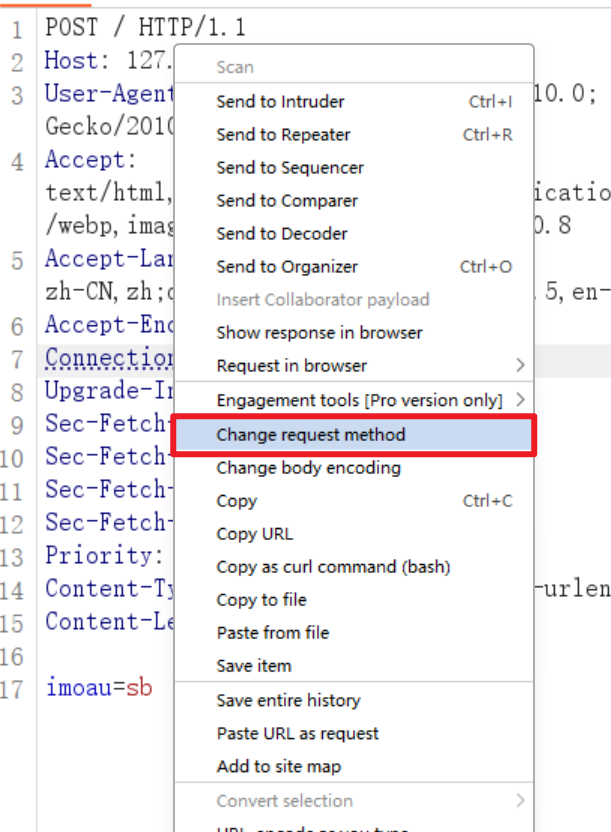
1 | POST / |
- 之后收到提示,才get头这边添加参数,但是方法还是post,由于发包不支持中文,所以就将
大帅转换成十六进制
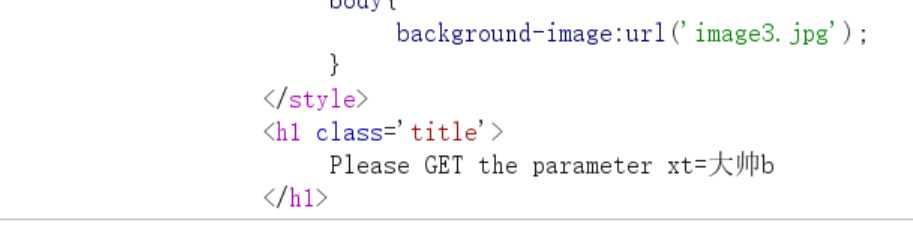
1 | POST /?xt=%E5%A4%A7%E5%B8%85b |
- 之后要求,即添加
Referer: https://www.xidian.edu.cn/
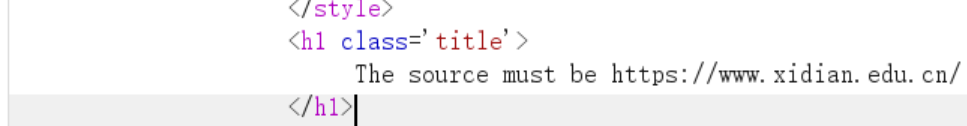
- 又要求
cookie参数
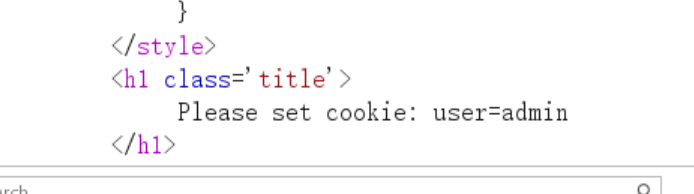
1 | POST /?xt=%E5%A4%A7%E5%B8%85b |
- 要求使用指定浏览器源
1 | POST /?xt=%E5%A4%A7%E5%B8%85b |
- 然后只要求本地通过
1 | POST /?xt=%E5%A4%A7%E5%B8%85b |
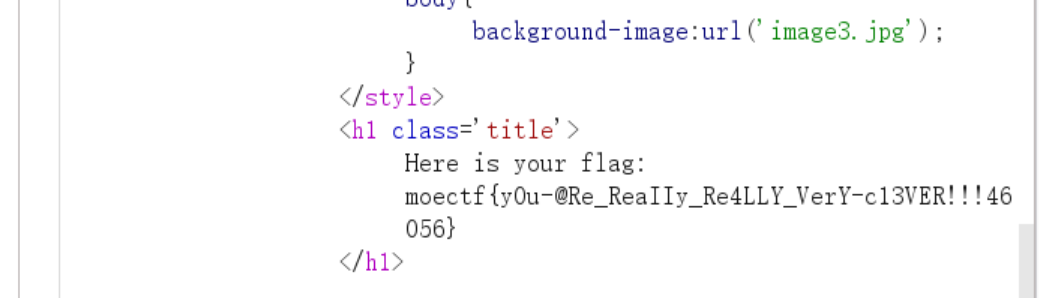
- 最后得到flag
moectf{y0u-@Re_ReaIIy_Re4LLY_VerY-c13VER!!!46056}
CRYPTO
现代密码学入门指北
- 下载入门指北并阅读到末尾的时候,给出了题目,简单的rsa加密
1 | from Crypto.Util.number import bytes_to_long, getPrime |
- 解密脚本如下:
1 | import libnum |
Signin
- 题目给了一个简单的rsa加密,正常解密即可
1 | from Crypto.Util.number import* |
- 先根据方程,利用sage解出方程
1 | p = var('p') |
- 得到p、q后直接rsa解密即可
1 | import libnum |
ez_hash
- 该题是hash爆破,这题原本暑假的时候就尝试做了,但是使用Python爆破不出来,然后去在线md5查询,查询出来了,但是看结果要钱,就没查看了
- 到了开学知道了有hashcat这个工具,可以使用显卡爆破,就爆破出来了
- 题目附件
1 | from hashlib import sha256 |
- 使用hashcat爆破,在Linux下安装好hash,然后输入指令
- SHA256:
-m 1400 -a 3指定使用掩码攻击(暴力破解)2100固定为前 4 位,?d?d?d?d?d?d表示 6 个未知的数字
- SHA256:
1 | hashcat -m 1400 -a 3 3a5137149f705e4da1bf6742e62c018e3f7a1784ceebcb0030656a2b42f50b6a 2100?d?d?d?d?d?d |
- 爆破得到的结果为
1 | 2100360168 |
- flag:
moectf{2100360168}
Big and small
- 还是一个rsa加密,但是e很小,直接开方即可
- 题目:
1 | from secret import flag |
- exp:
1 | import libnum |
baby_equation
-
这题开了俩个提示,还是没思路,最后和某个已经做出来的师傅对了下思路,发现思路问题,之后思路正确了就做下去了
-
其中题目中的俩个提示也还是有用的
-
题目附件如下,主要聚焦到
assert的这个式子中
1 | from Crypto.Util.number import * |
- 题目提示用yafu分解,我这边是将
4k分解,得到,很明显,k能分解出这么多式子,甚至都是俩个或偶数个的素数,这就要想到,4k可以因式分解成与a和b相关的因式而且还是代平方的那种
1 | P1 = 2 |
- 所以接下来就对
assert的那个式子进行因式分解,结果分解半天分解错了QAQ。 - 最后得到的结果还是AI跑出来的

- 接下来用上第二个提示,由于我并不知道
a+1可以分解成那些素数的乘积,但我知道flag中有moectf(这也就是第二个提示),所以我就考虑使用随机数的办法进行爆破,结果当然是爆破出来了
1 | c = [64889106213996537255229963986303510188999911,25866088332911027256931479223,26798471753993,339386329,370523737,5404604441993,4151351,281317,4013,223,61,31,2,2,2,2,3,3] |
- 得到
a+1的值就可以利用因式分解的值可以算出b的值,从而知道flag的后半部分了
1 | a_plus_1 = 2950365559902224963252311699604518749050102395042841254385700637274676 |
RE
逆向工程入门指北
- 下载pdf附件翻到第二页
1 |
|
- 这个就是本题
flag了
1 | a = [ 123, 121, 115, 117, 98, 112, 109, 100, 37, 96, 37, 100, 101, 37, 73, 39, |
异或
- 使用IDA反编译附件,然后查看反编译的代码,发现就是简单的异或
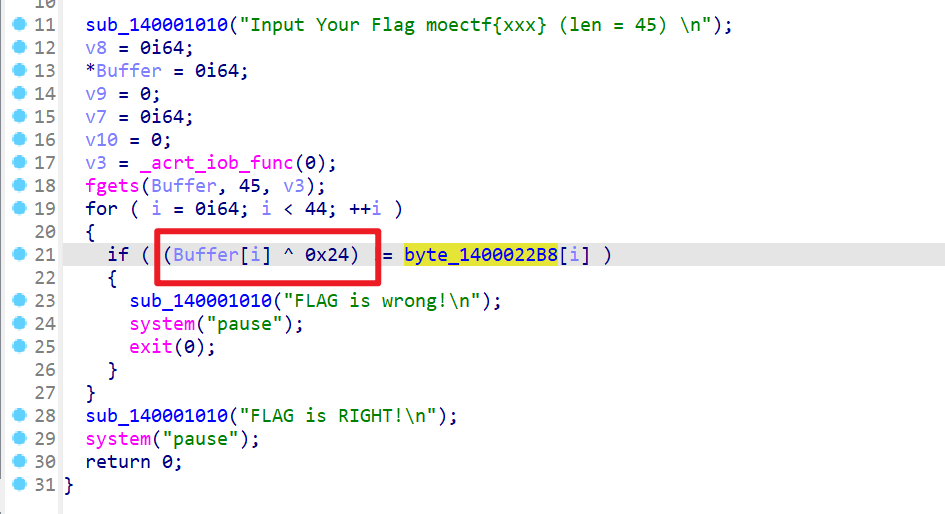
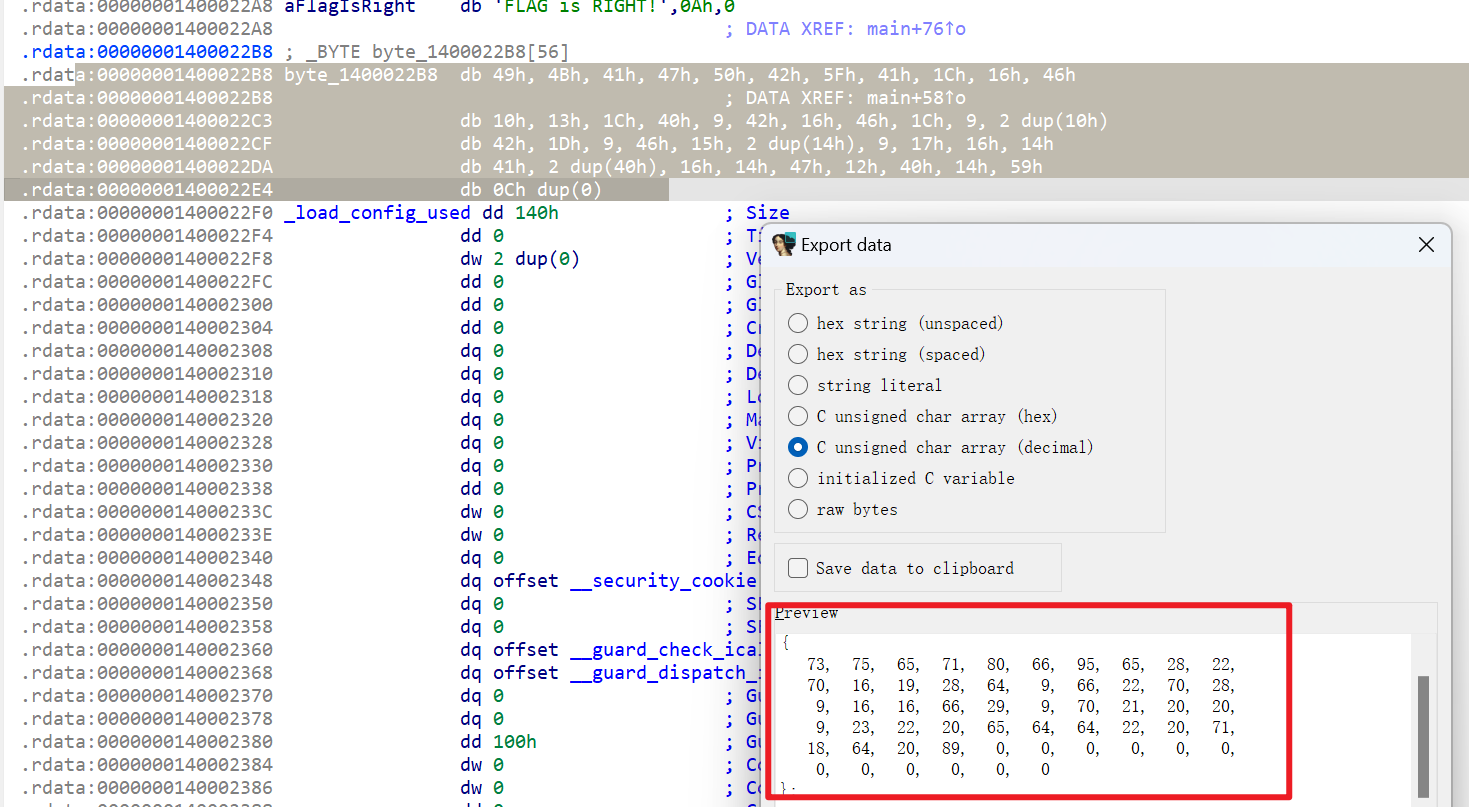
- 加密后的数据保存在
byte_1400022B8数据段中,使用shift+E提取数组
- 编写解密脚本
1 | a = [ 73, 75, 65, 71, 80, 66, 95, 65, 28, 22, |
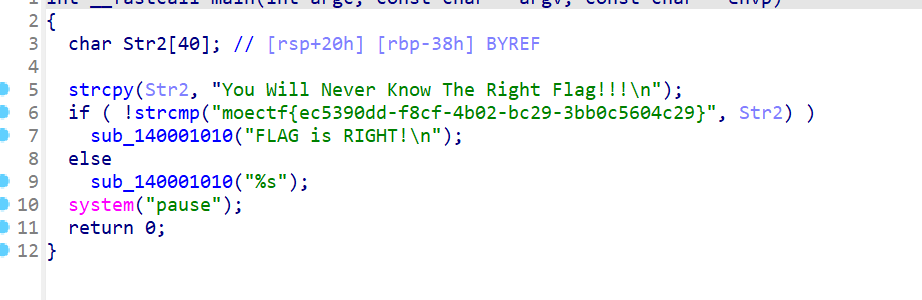
UPX
- 简单的upx脱壳,直接下载
upx脱壳工具,使用指令upx-d脱壳,这里就不演示了 - 脱壳后使用IDA反编译,反编译完即可看到flag
moectf{ec5390dd-f8cf-4b02-bc29-3bb0c5604c29}
upx-revenge
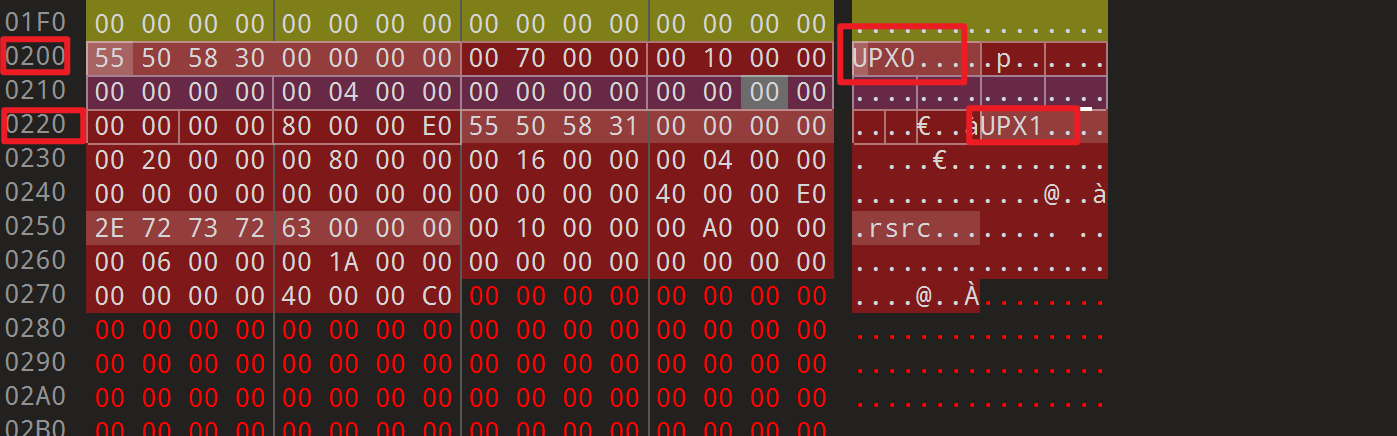
-
魔改的upx脱壳,下载附件后使用010Editor打开,然后将这两个地方分别改为
UPX0和UPX1 -
然后就可以使用upx脱壳软件
upx -d进行自动脱壳了
- 脱壳完之后再使用IDA打开,即可看到flag
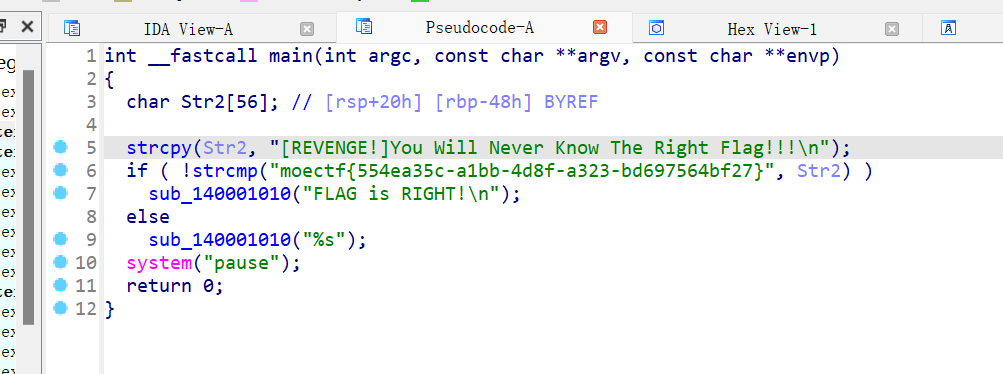
- flag文件
moectf{554ea35c-a1bb-4d8f-a323-bd697564bf27}
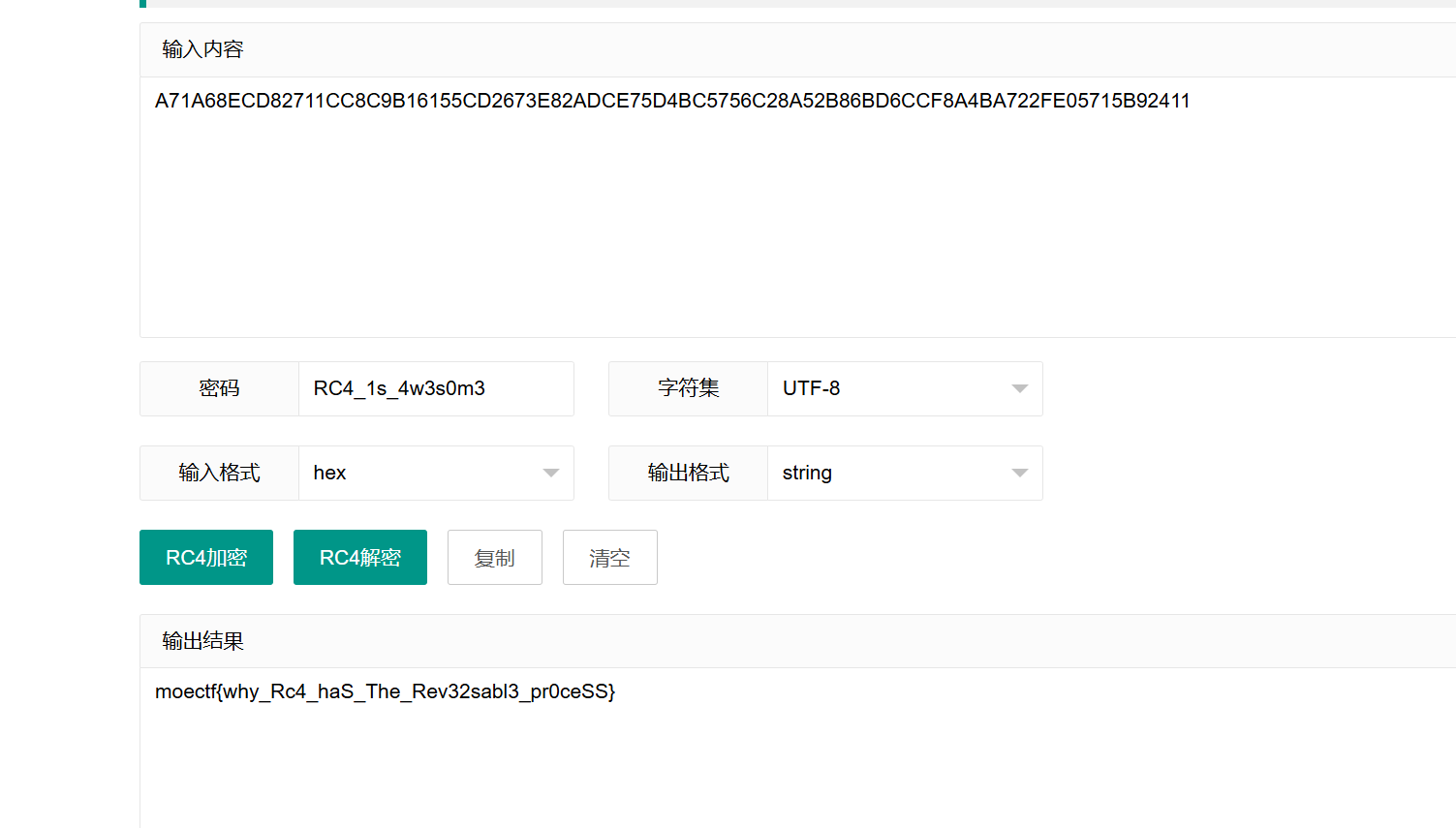
RC4
- 下载附件后使用IDA打开,然后快速定位到
main函数中 - 发现
A71A68ECD82711CC8C9B16155CD2673E82ADCE75D4BC5756C28A52B86BD6CCF8A4BA722FE05715B92411是密文 - 密钥是
RC4_1s_4w3s0m3
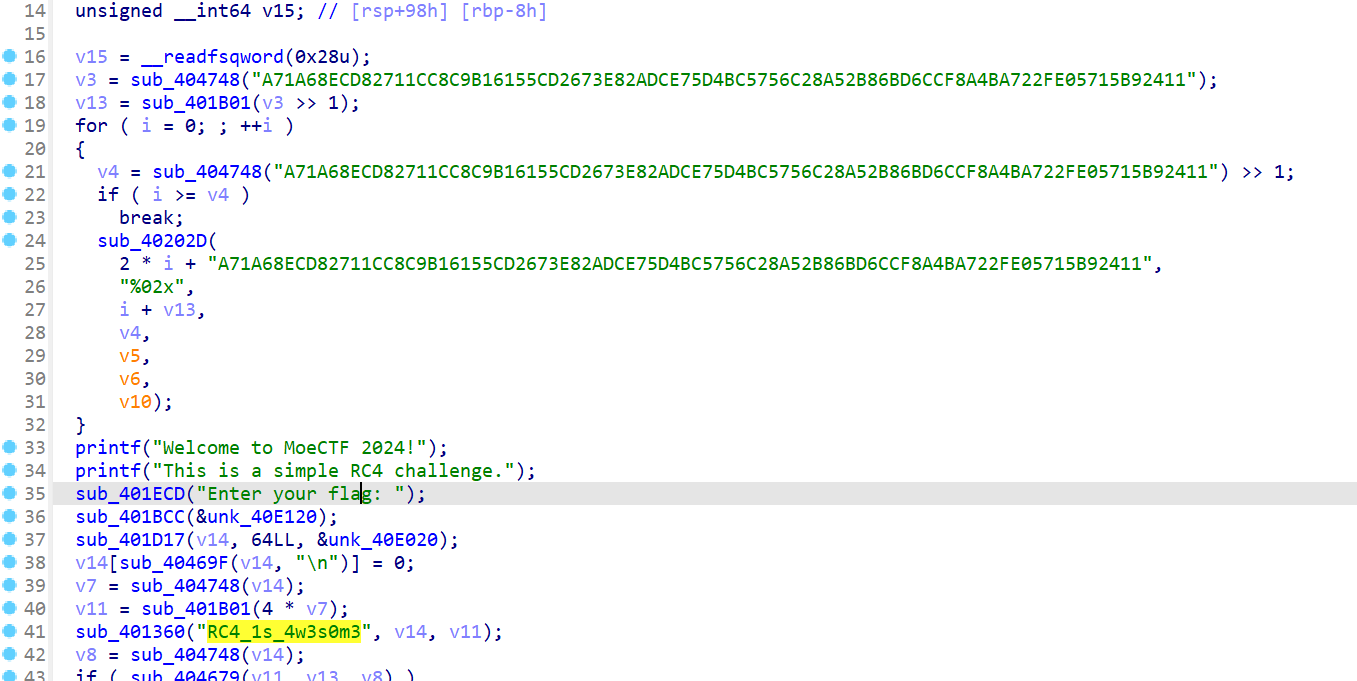
- 然后直接在线rc4解密即可,如果是为了学习而做题的话建议使用Python手搓rc4解密脚本,得到flag
1 | moectf{why_Rc4_haS_The_Rev32sabl3_pr0ceSS} |
Tea
-
在另一篇文章中写过了,这里直接复制粘贴
-
题目附件就只给一个
.exe的可执行程序

- 先运行一下这个点exe文件。发现程序已经给出后面一部分的flag。然后前面的flag使用未知数表示。该程序让用户输入前三段的flag
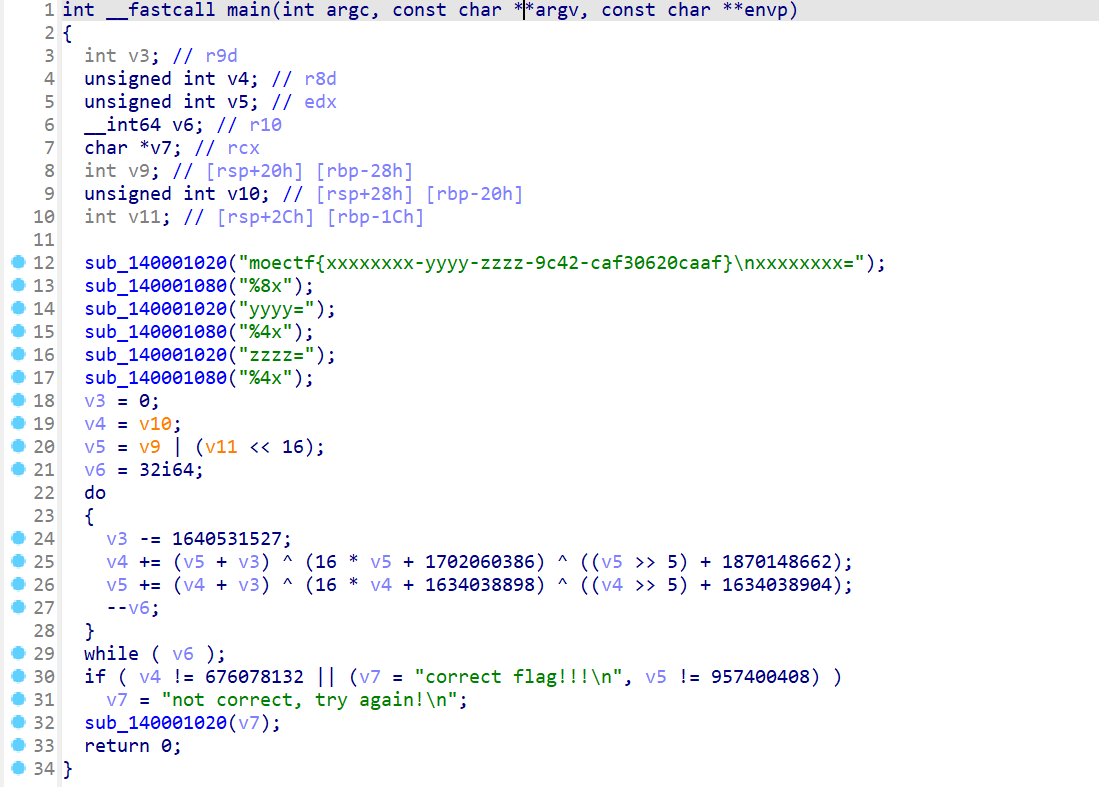
- 然后使用IDA反编译一下,主要加密函数如下
- 由于该题将库函数的符号表给去掉了,所以先推出一些函数,更方便看代码
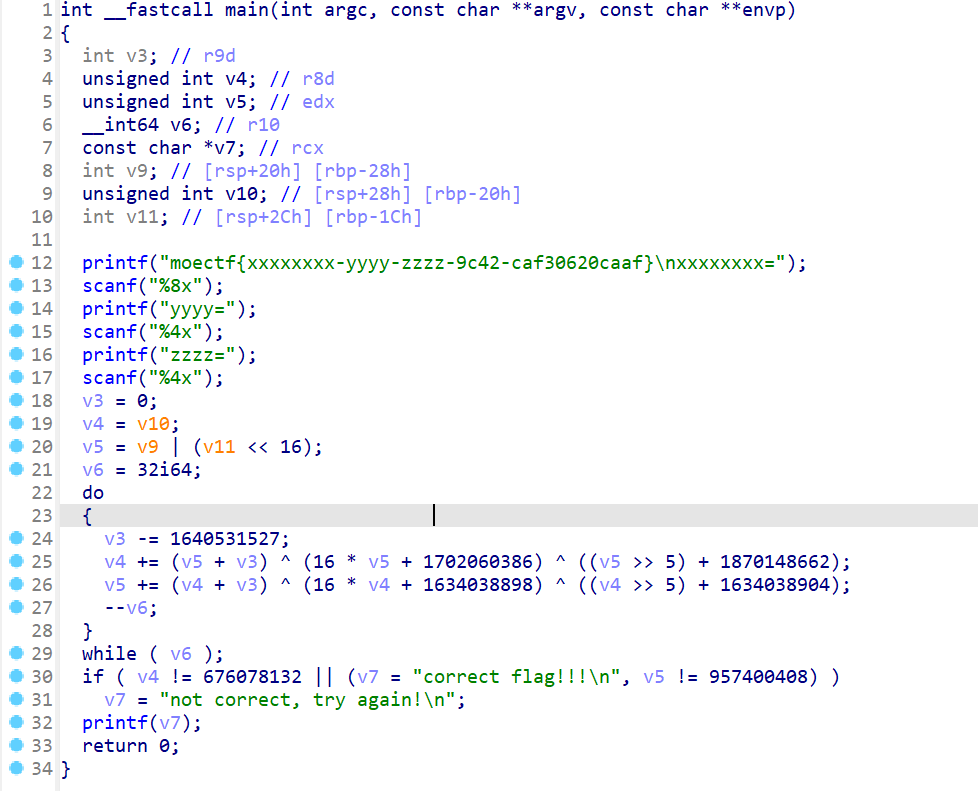
- 对于这一步就是要用户输入正确的部分flag
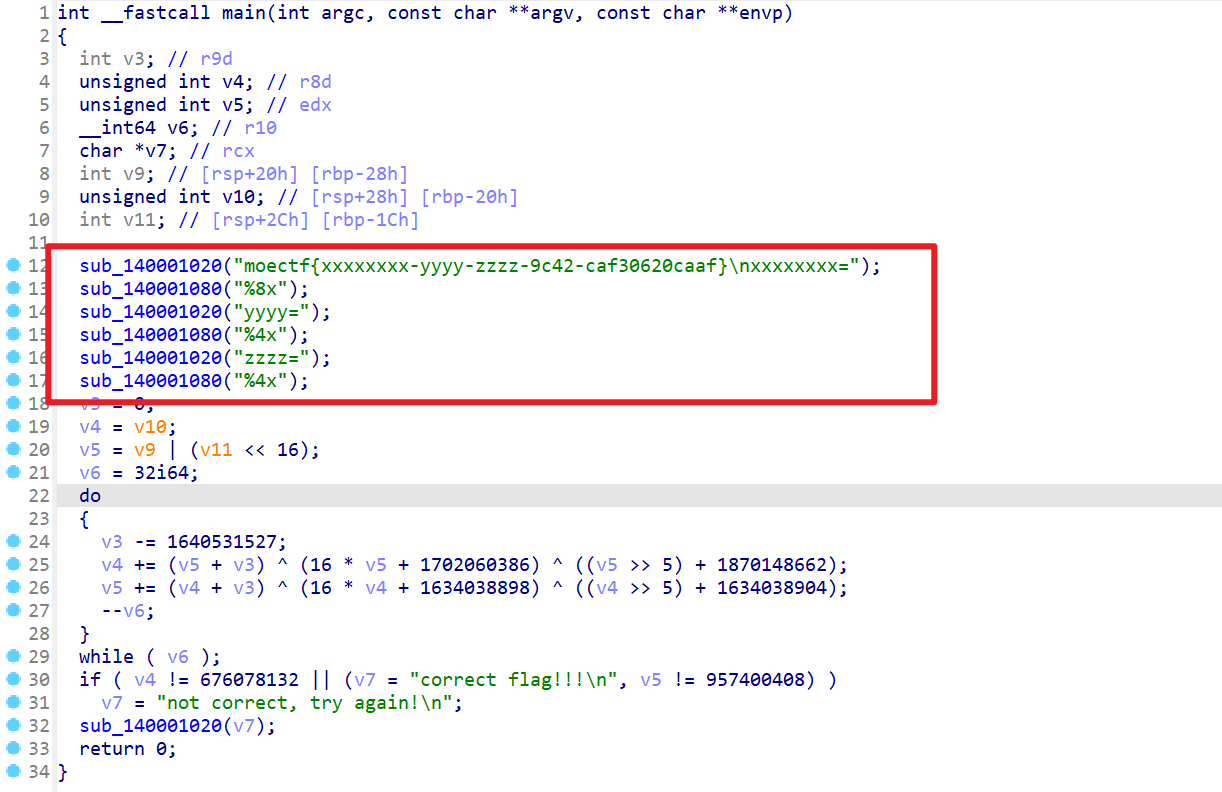
- 接下来对下面进行分析,发现有几个变量
- 但是由于scanf后面需要跟一个变量,但是可能由于反编译的问题。
- 这样v10、v9、v11三个变量可能就是要求输入的明文
- 所以变量v4、v5是明文
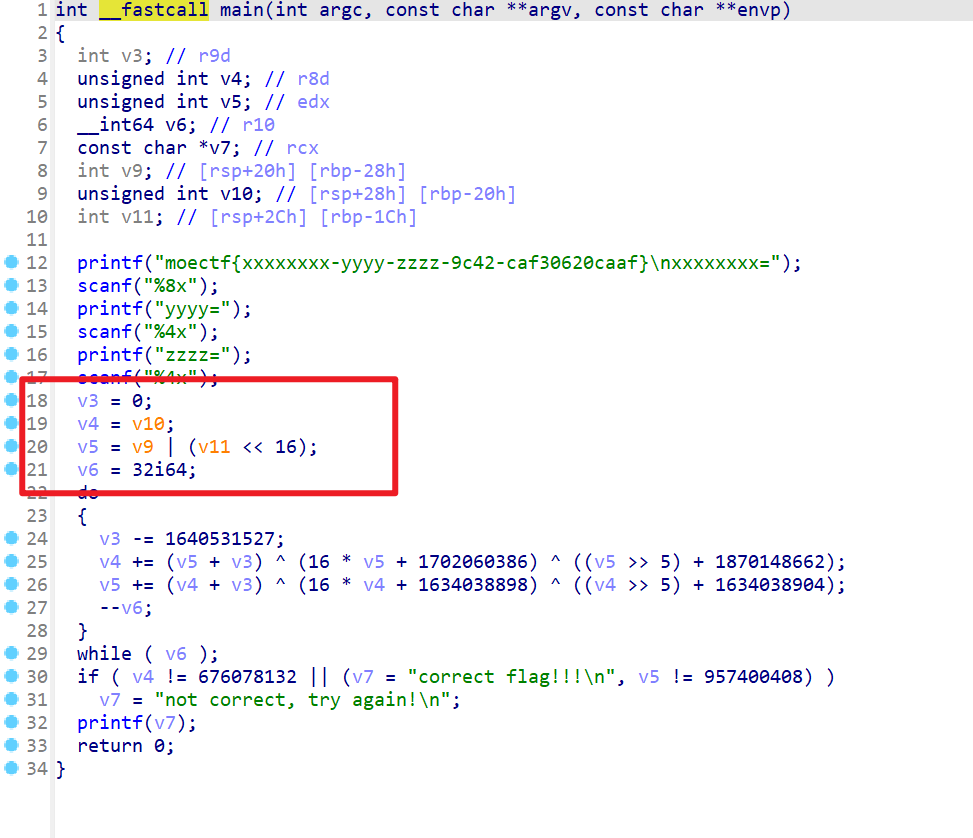
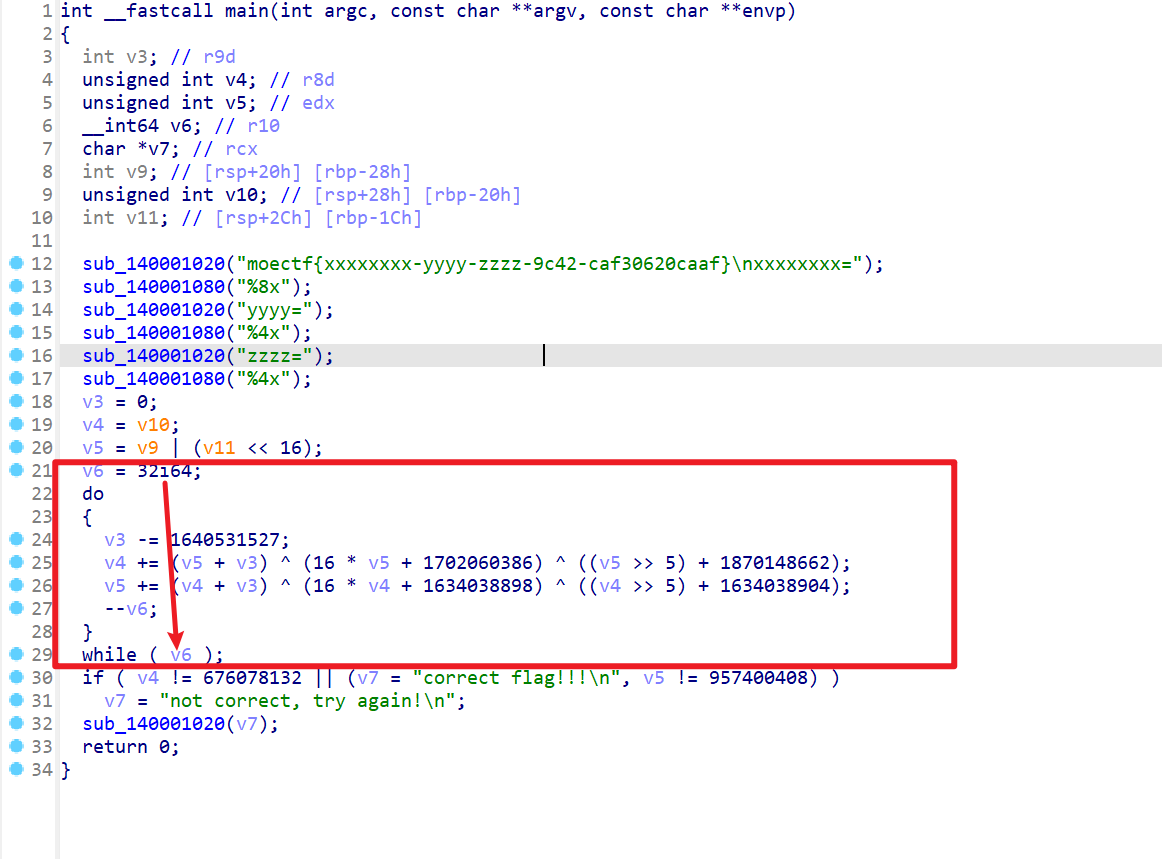
- 然后查看循环和循环里面的式子
- 可以初步判断v6是循环次数,也就是TEA加密的轮数
- 而循环内部就是加密的算法
- 然后最后的是判断flag是否正确
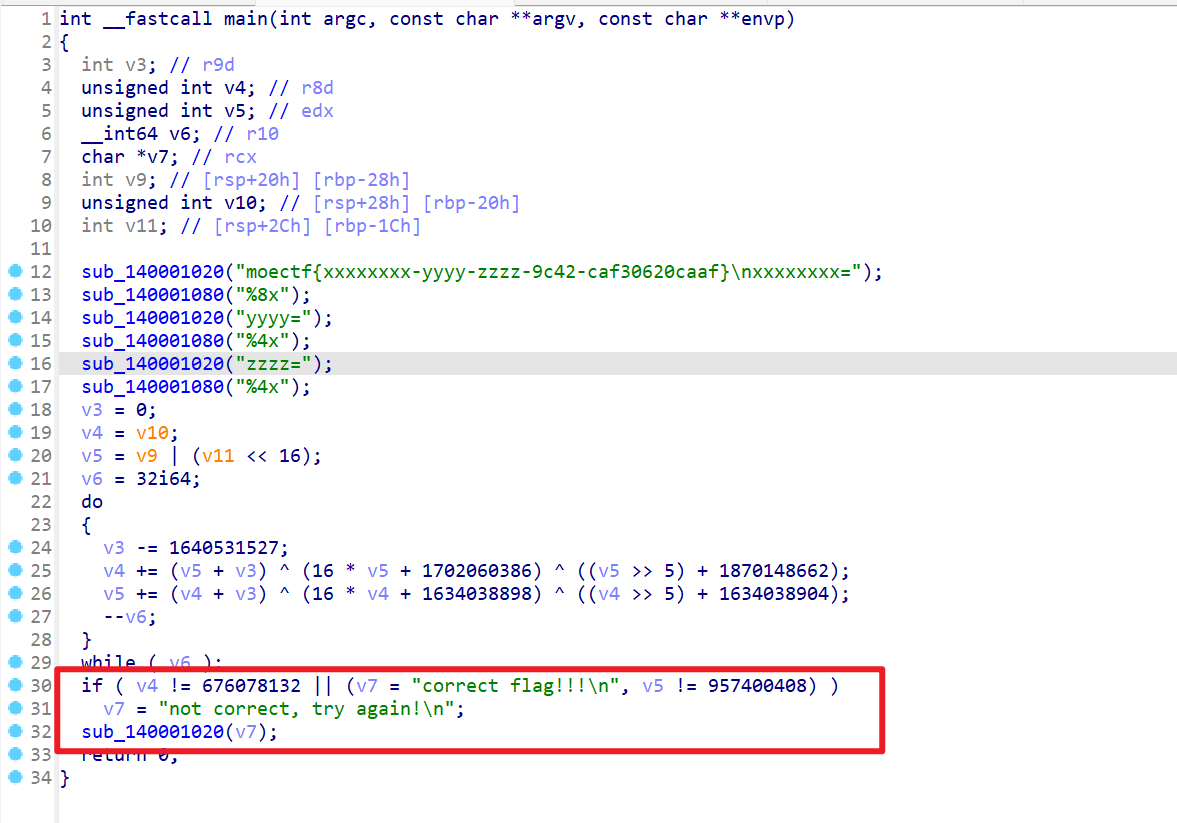
- 现在目前的重点在于分析该步骤的算法
- 由最后一步判断得知
- v4加密后最终的值为
676078132 - v5加密后最终的值为
957400408
- v4加密后最终的值为
- 由一开始
v3=0然后每次循环都有v3 -= 1640531527,可知最后一次加密时的值为v3 =-1640531527*32 - 然后是最核心的算法,这里还要注意的是可能存在溢出或者回绕,可能需要取模或者进行位运算
1 | v4 += (v5+v3)^(16*v5 + 170260386) ^ ((v5 >> 5) + 1870148662); |
- 由于v5的最后一次加密与运算后的v4有关,所以解密的时候应该是v5先进行运算
1 | v5 = 957400408 |
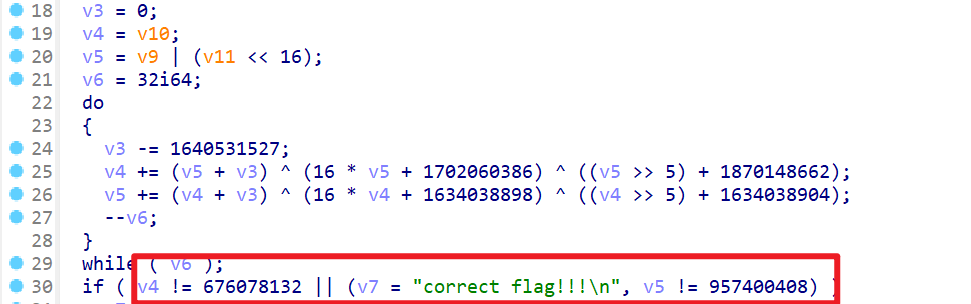
- 通过加密可以编写解密脚本,但是由于存在整数溢出和回绕的问题,为了不取模,直接编写C语言脚本进行解密。而不编写Python脚本解密
1 |
|
- Python脚本实现解密是通过位运算
1 | def decrypt(v4, v5, rounds): |
- 运行后将结果转换为16进制
1 | 0x836153a5 |
d0tN3t
-
.dll逆向,使用工具ILSpy逆向,可以直接反编译出内容,然后进行解密,主要问题就出在工具上。IDApro反编译不了.dll文件
- 下载
.exe版后解压,进入解压文件,.exe文件,然后点击进去
- 在程序内部打开附件就行
- 然后点击进入到这里,就可以看到加密逻辑了
- 加密逻辑如下图
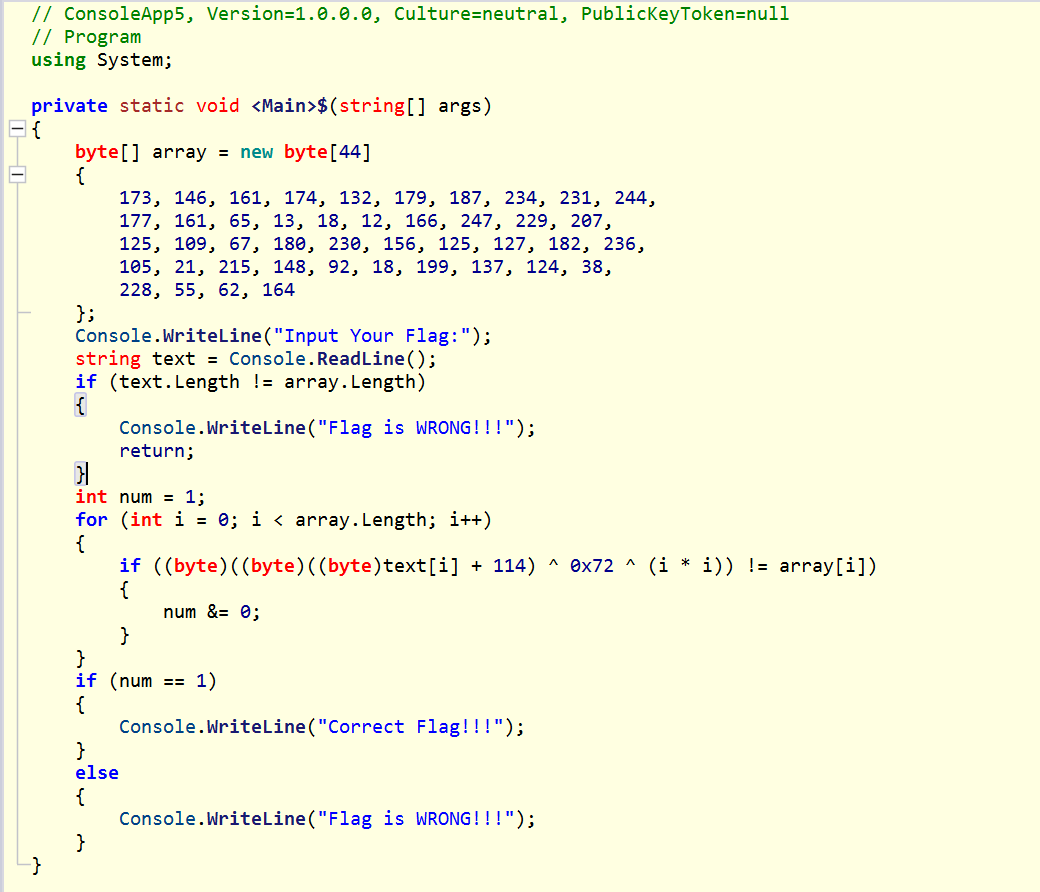
- 编写脚本一把梭,注意异或
i*i有时候会超出255,所以要异或i*i后要与一个0xFF
1 | a = [173, 146, 161, 174, 132, 179, 187, 234, 231, 244,177, 161, 65, 13, 18, 12, 166, 247, 229, 207,125, 109, 67, 180, 230, 156, 125, 127, 182, 236,105, 21, 215, 148, 92, 18, 199, 137, 124, 38,228, 55, 62, 164] |
dynamic
- 简单的动态调试题目,下载附件,使用IDA打开发现有给数据,但是给的数据是加密过后的数据,不是真正的flag
- 但是在程序运行的过程中就会调用加密(解密)函数,可以把flag给解密出来,这时就会出现flag,但是flag在栈上
- 所以我们需要动态调试取查看栈上的内容
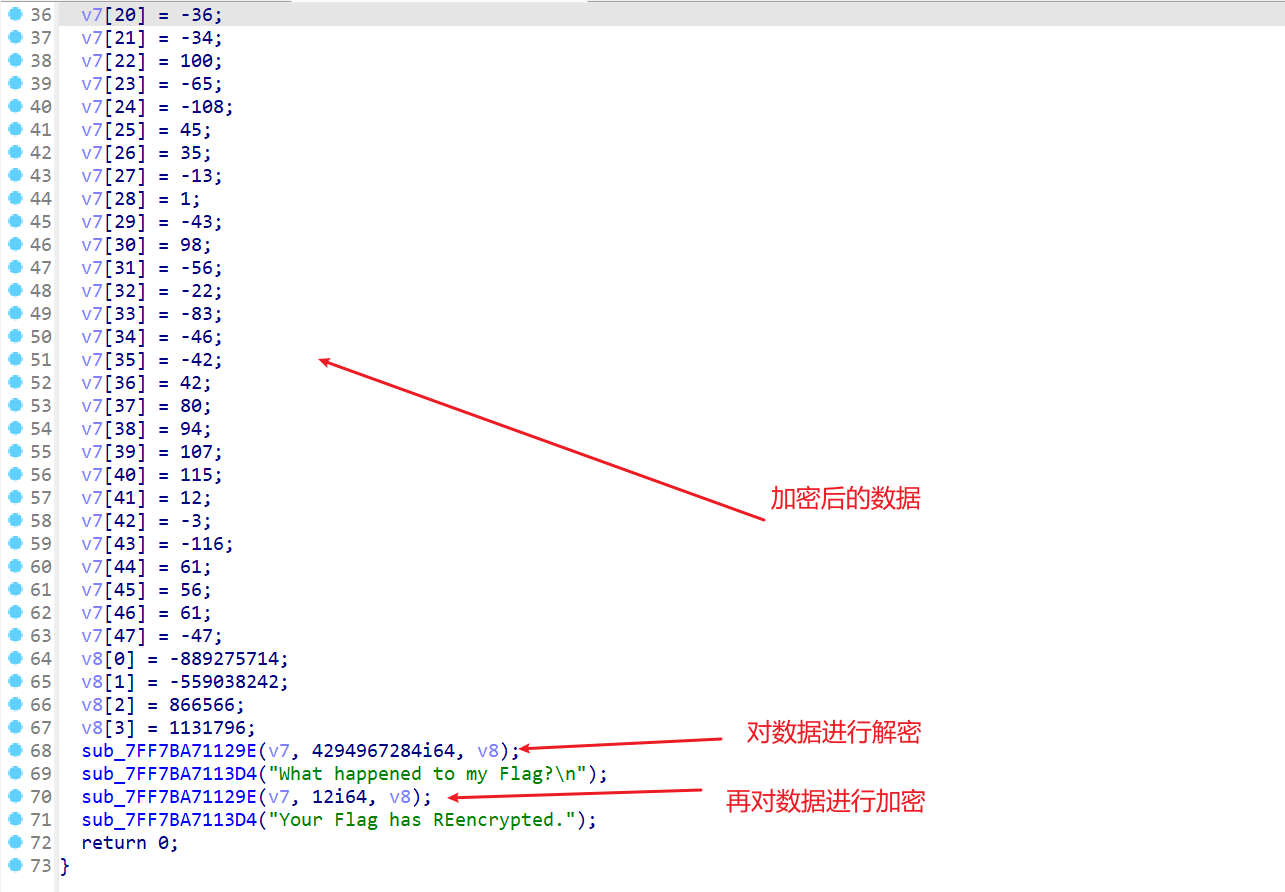
- 先在该处打下断点
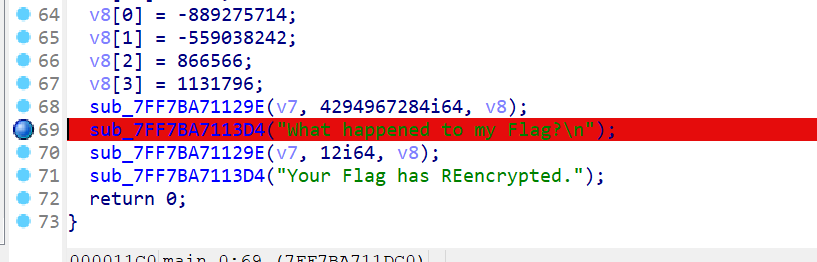
- 然后再按下
F9键,选择该选项
- 选择完后就会进入动态调试的模式,这样就在栈上可以看到flag的16进制模式
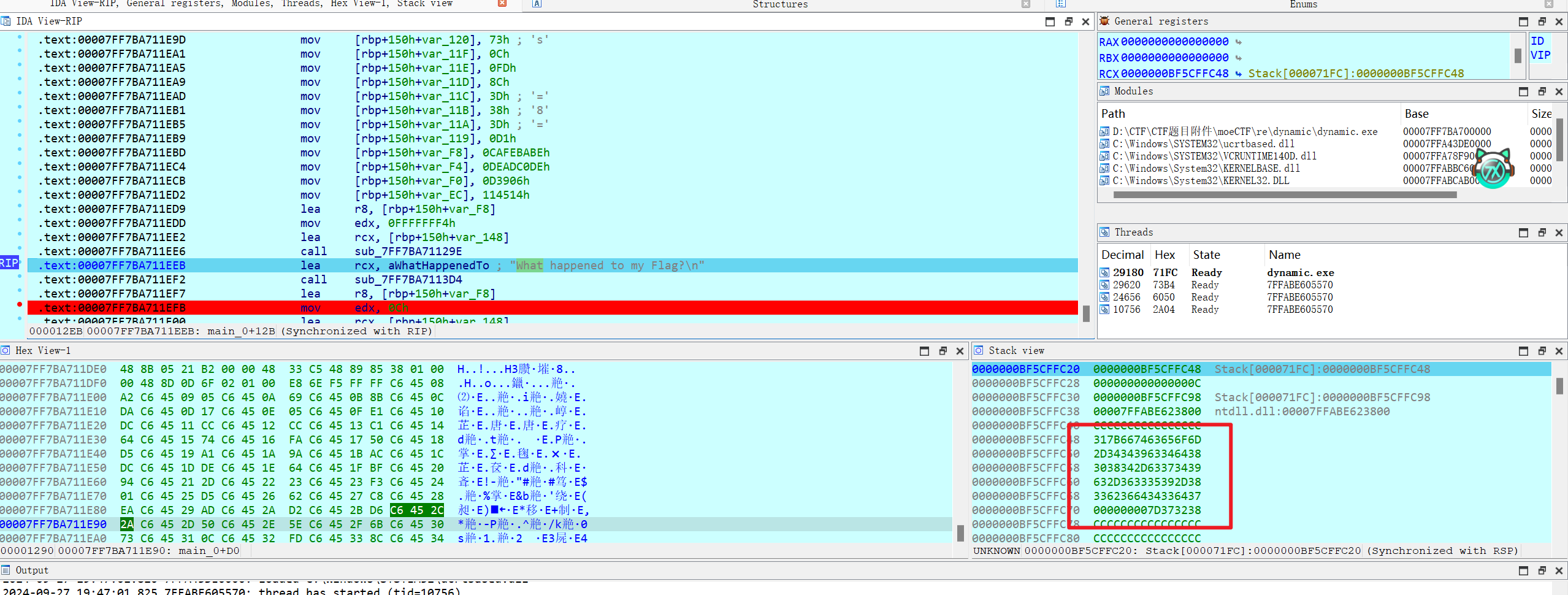
- 将这一串16进制复制下来,丢入在线16进制转字符串
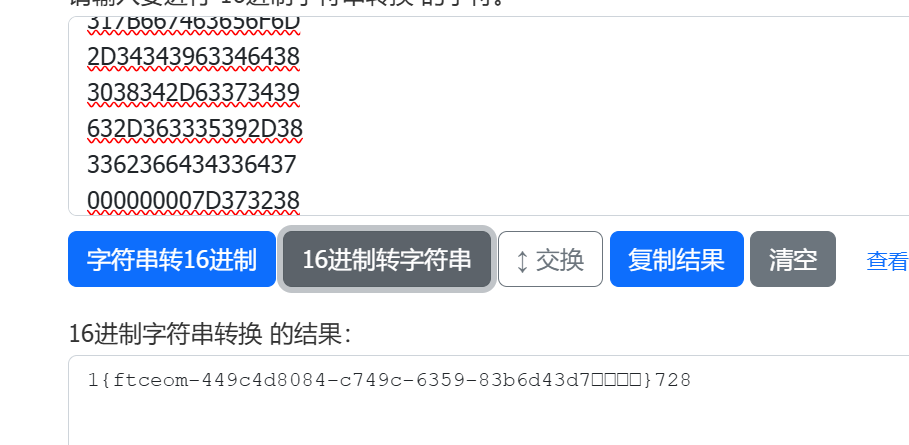
- flag其实已经得到了,但是由于是小端序的内存表示,所以我写了个Python脚本,将flag变成正常的flag
1 | a = '''317B667463656F6D |
Just-Run-It
- 下载附件,然后打开,发现给了4个程序,分别是
exe、elf、riscv.elf、apk四个文件
- 先运行一下
.exe文件,这样就会给出一个十六进制的字符串
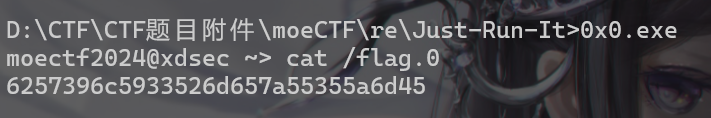
1 | 6257396c5933526d657a55355a6d45 |
- 然后转字符串后就变成
1 | bW9lY3RmezU5ZmE |
- 运行
apk文件,就直接将该文件拖入雷电模拟器中,然后运行 - 运行了一下
0x3.riscv0x64.elf,运行结果显示一串数组(十进制),将这一串数组转为字符串。
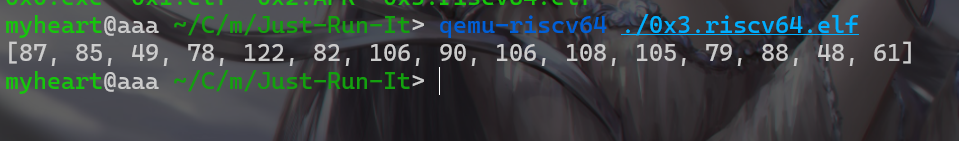
1 | WU1NzRjZjliOX0= |
逆向工程进阶之北
ezMAZE
- 此题考点算是比较综合的了,深搜和广搜,位压缩,动态调试
- 拿到附件后使用IDA进行反编译,反编译之后就会解读代码
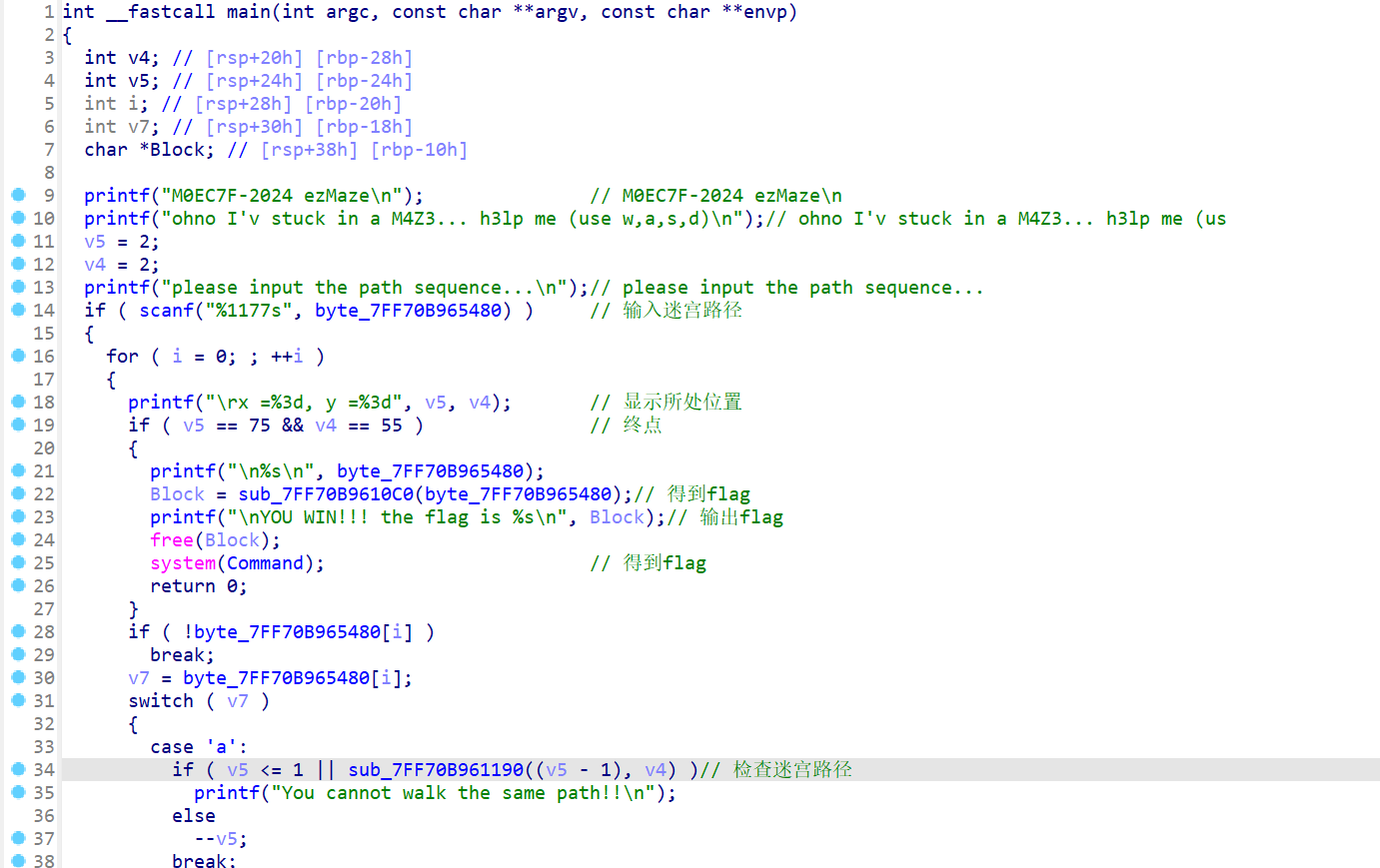
- 然后在检查迷宫路径这边有一个函数,函数名称为
sub_7FF70B961190,点击去查看,发现是检查位压缩的0、1位 - 所以
byte_7FF70B965000就是地图了
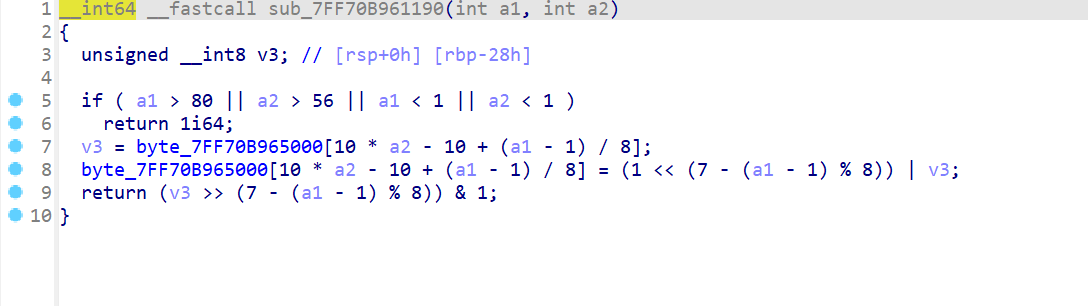
- 点击
byte_7FF70B965000查看地图,发现是一个位压缩的地图形式,1为墙,0为路
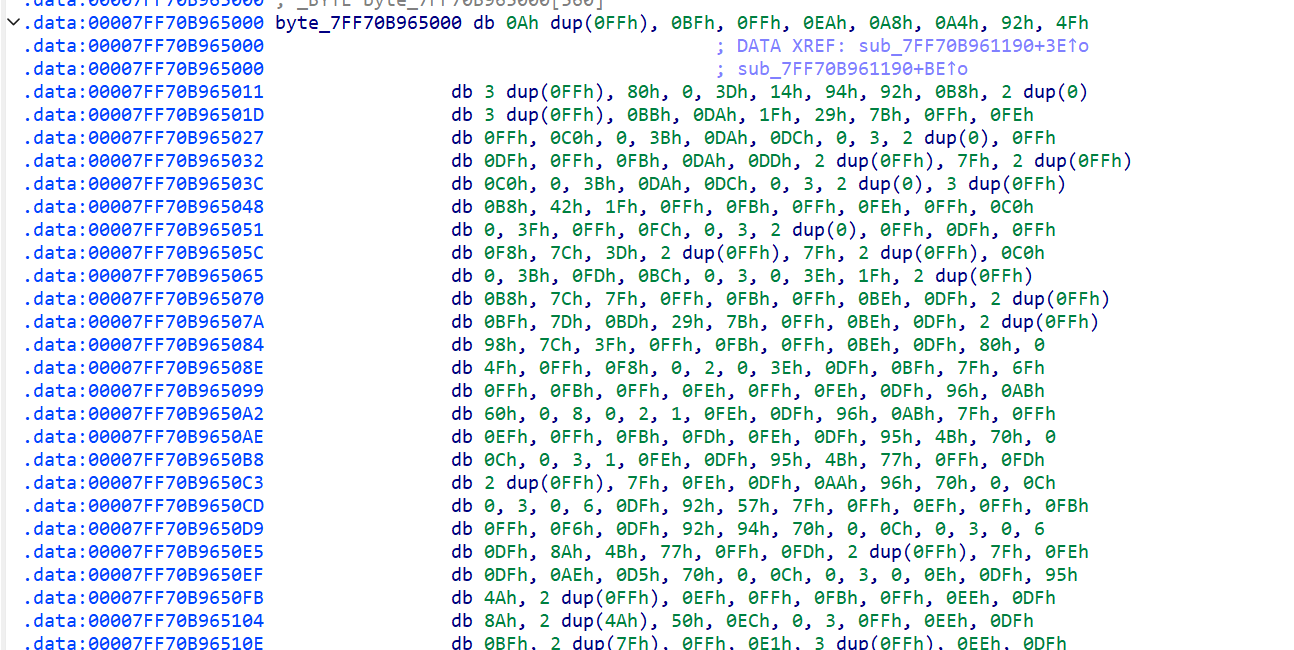
- 这样我就先在该位置打下断点
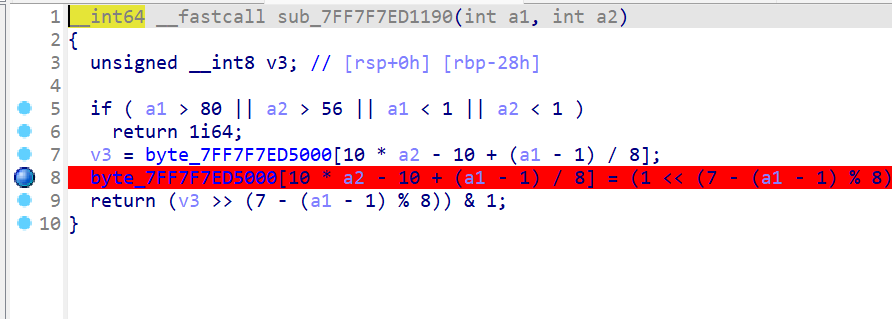
- 进行动态调试,找到迷宫存放的地址,然后将迷宫提取为二进制文件
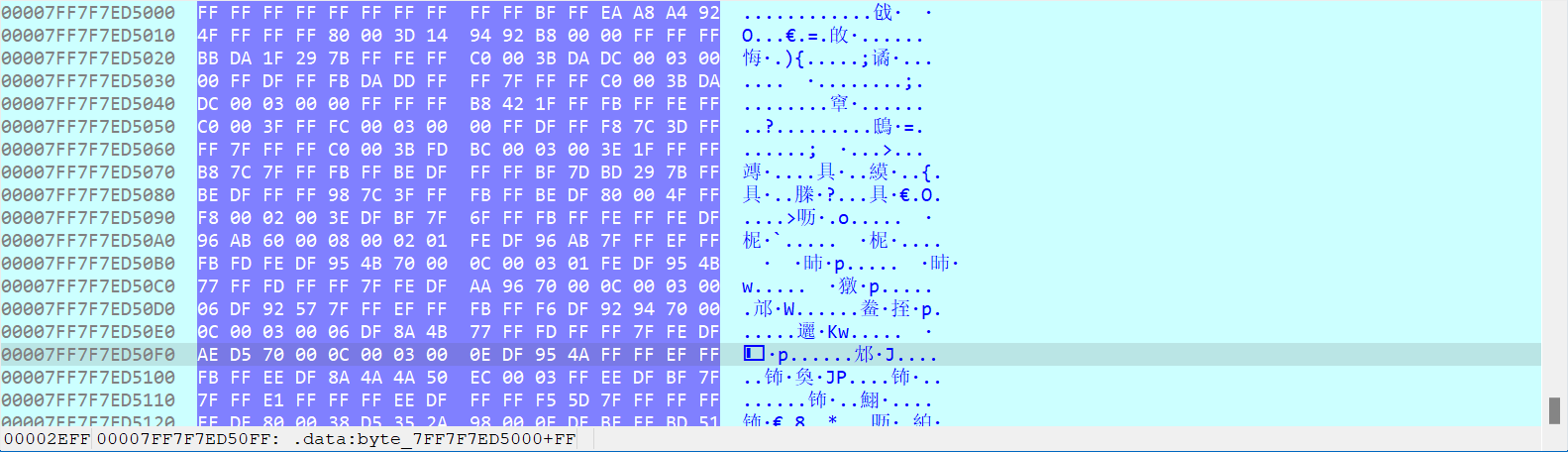
- 使用Python将其转换为0、1字符串的迷宫
1 | def extract_and_convert_to_binary_string(input_file): |
- 然后以迷宫56行,80列的形式输出
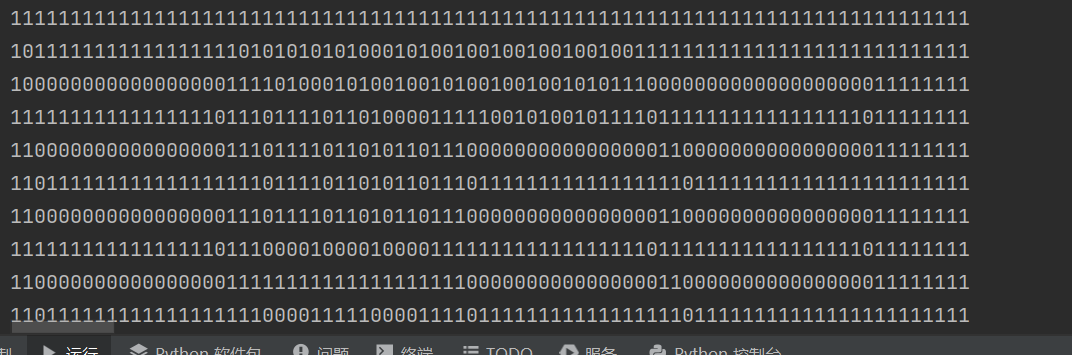
- 起点坐标为
(2,2),真实起点应该为(1,1),终点坐标为(55,75),真实的终点应该为(54,74),知道起点和终点,直接编写深度搜索和广度搜索算法寻找迷宫路径
1 | from collections import deque |
- 得到最终路径
1 | DFS最终路径: sddddddddddddddddssaaaaaaaaaaaaaaassdddddddddddddddssaaaaaaaaaaaaaaassdddddddddddddddsssdsdssddddddddddddddddssaaaaaaaaaaaaaaassdddddddddddddddssaaaaaaaaaaaaaaassdddddddddddddddsssdddwdddddddddddddddwwaaaaaaaaaaaaaaawwdddddddddddddddwwaaaaaaaaaaaaaaawwdddddddddddddddwwaaaaaaaaaaaaaaaawwddddddddddddddddwwwwaaaaaaaaaaaaaaawwdddddddddddddddwwaaaaaaaaaaaaaaawwddwdsddddwdsdddddddwwddddddddddddddddddssaaaaaaaaaaaaaaassdddddddddddddddssaaaaaaaaaaaaaaassdddddddddssssaaaaaaaaaassdddddddssaaaaaassddddddddddddssaaaaaaaaaaaassdddddddddddsssssaaaaaaaaaaaaaassaaaaaaaaaaaaaaassdddddddddddddddssaaaaaaaaaaaaaaassdddddddddddddddssssaaaaaaaaaaaaaaaassddddddddddddddddssaaaaaaaaaaaaaaassdddddddddddddddssaaaaaaaaaaaaaaassaaaaaaaaaaaaaaaaaawwdddddddddddddddwwaaaaaaaaaaaaaaawwdddddddddddddddwwaaaaaaaaaaaaaaaawwawawwwaaaaaaaaaaaaaawwddddddddddddddwwaaaaaaaaaaaaaawwddddddddddddddwwaaaaaaaaaaaaaaaasssssssssssssssssssssssssdddddwwdssddwwwdsssddwdwwdsssddwdsdddwdsdwdsddddddddddddwddddddddddddddddddwdddwwwdddddddddddddddwwaaaaaaaaaaaaaaawwddddddwwaaaaaaawwddddddddddddddssdddwwwawwwaaaaaaaaaaaaaaawwdddddddddddddddwwaaaaaaaaaaaaaaawwdddddddddddddddwwwwwwwwwwwwwwwwwwwwwdddssssssssssssssssssssssssssssssssssssssssssss |
- 最后输入最终路径,得到flag,这里只有输入
BFS最终路径才能得到flag
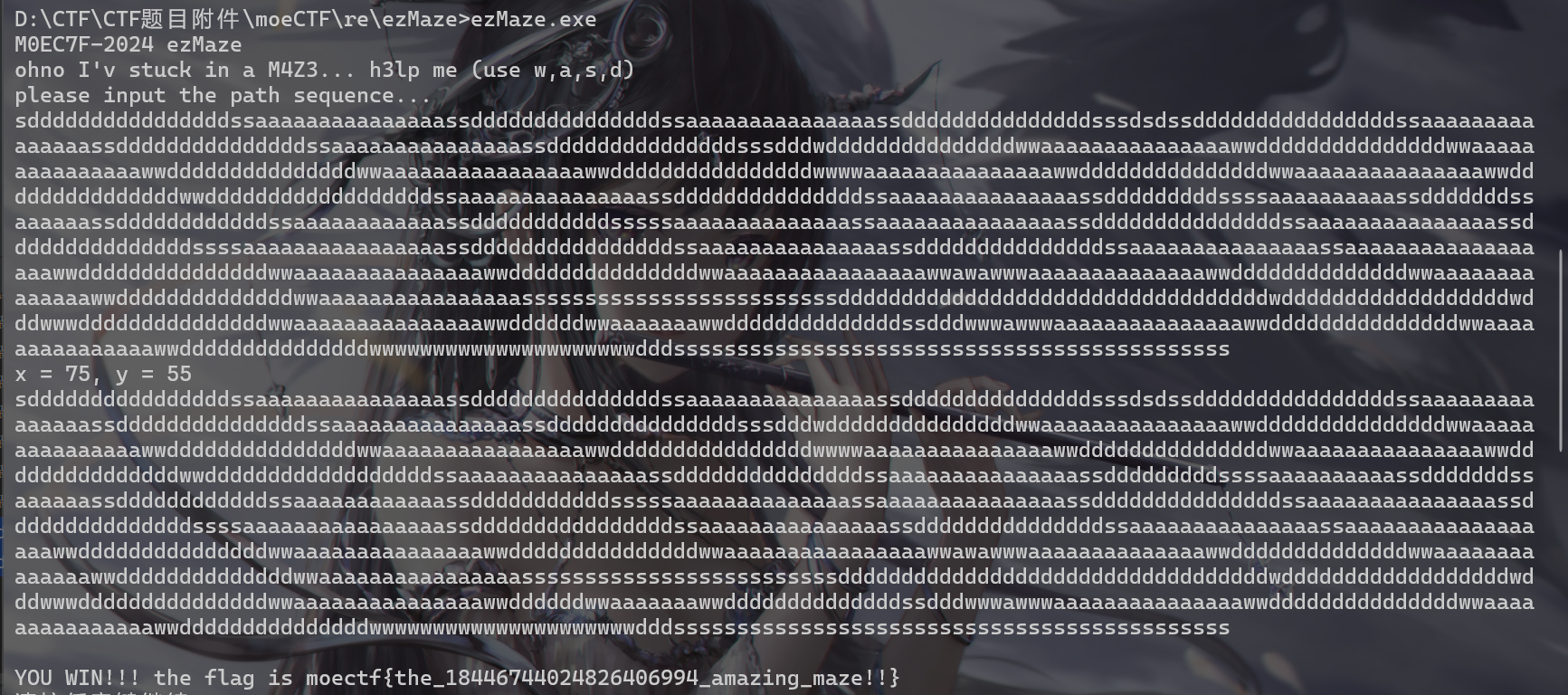
moectf{the_18446744024826406994_amazing_maze!!}
PWN
二进制漏洞审计入门指北
- 题目给了个入门指北,最好还是看一下
- 签到题,学会
nc直接就送flag
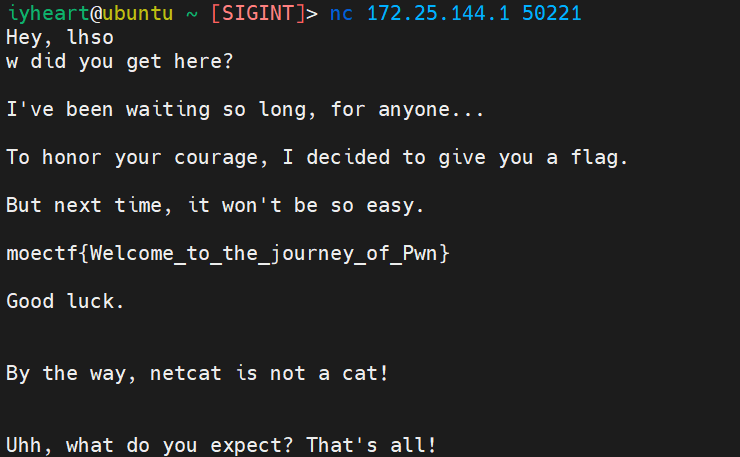
flag:moectf{Welcome_to_the_journey_of_Pwn}
NotEnoughTime
- 题目:说是检测数学能力,其实是练习接收与发送,与靶机交互。
- 这题会发送一些数学四则运算的题目,算式均为 C 语言表达式,整数除法。还有时间限制
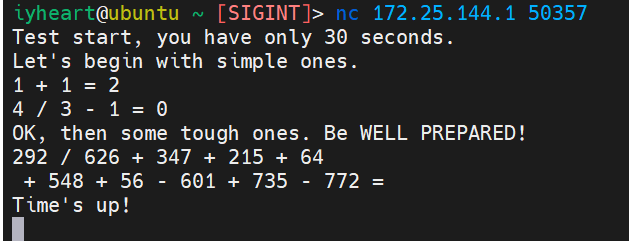
- 这种情况就需要使用Python脚本实现交互
- 先将第一个和第二个固定的算式单独做一个接收和发送
- 然后再接收一行字符串
- 接下来使用Python的
eval()函数,eval()函数执行其传递的参数内容,并返回结果 - 对接收的算式先进行处理,比如将
换行符去掉,将最后接收到的=号去掉 - 最后使用
eval()函数进行计算 - 再将计算结果发送出去,进而实现自动化计算脚本
- exp如下:
1 | from pwn import * |
no_more_gets
- 题目:
AI
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 iyheart的博客!
评论

