PWN堆house-of-roman
前置知识
- 前置知识的话基本上都学了,这边就大概书写一下。
fastbin的运行机制unsorted_bin的运行机制fastbin_attackunsorted_bin_attackmalloc_hook等hook技术
实验
- 接下来直接进行实验还是老样子,翻译源码。
源码
1 |
|
- 接下来进行翻译,翻译太长了到
200行之后就AI跑了,在翻译的时候就感觉how2heap的这个实验说明部分有点啰嗦.
1 |
|
利用与调试
- 接下来我们来进行程序的调试,并且画图来查看一下
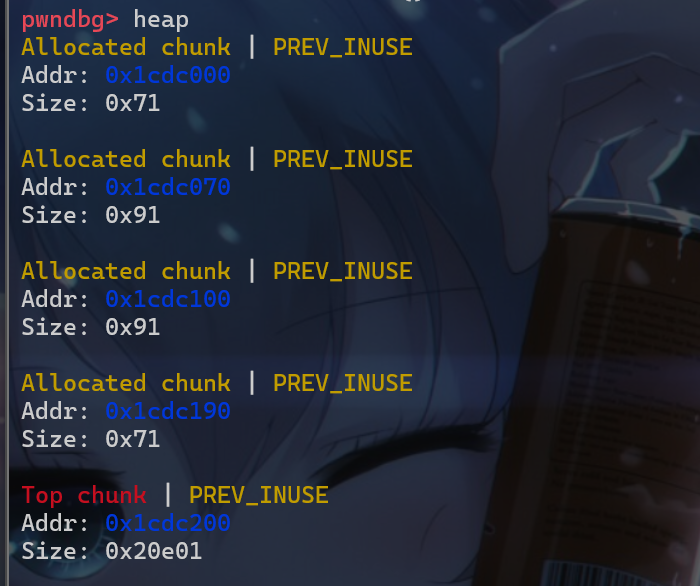
house of roman是如何进行利用的。我们这边就先简单介绍一下这四个堆块的作用- 我们申请的第一个堆块是为了进行
UAF漏洞的利用malloc(0x60) - 我们申请的第二个堆块是为了第三次申请的堆块的起始地址与
0x100对齐 - 申请第三个堆块,其被命名为
main_arena_use,这个堆块之后会被释放,释放后会被放入unsorted_bin - 申请第四个堆块,其被命名为
relative_offset_heap,这个堆块的作用就是用来写相对地址的
- 我们申请的第一个堆块是为了进行
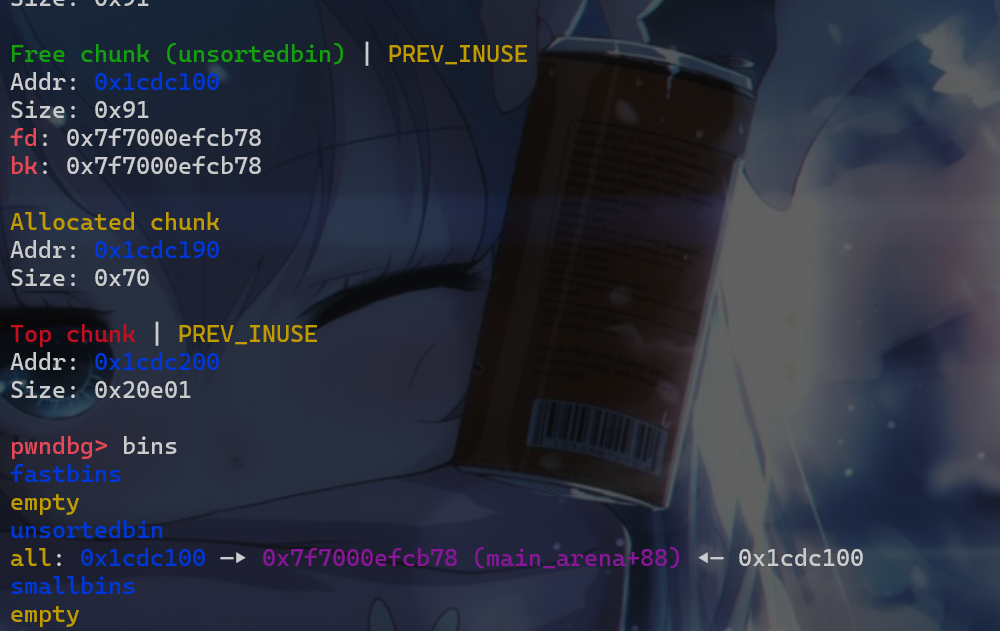
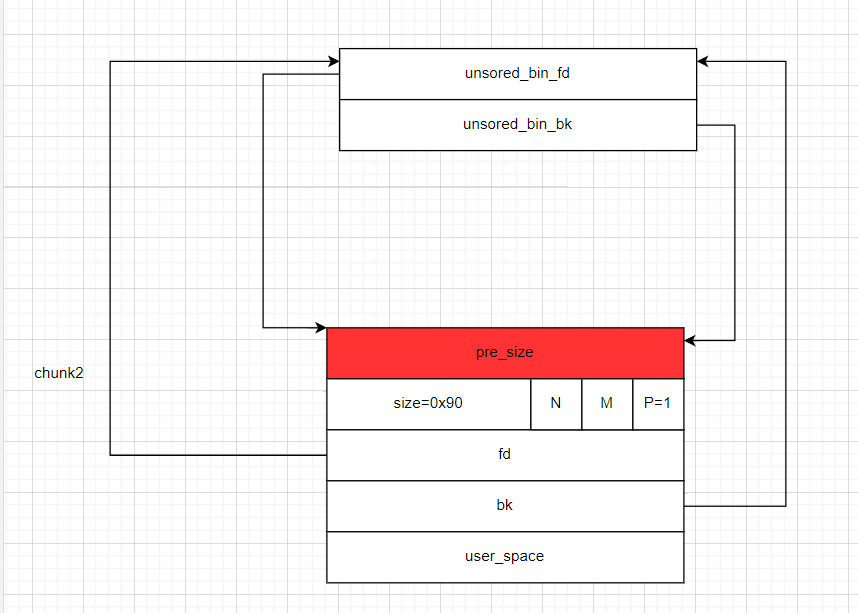
- 然后我们将我们第三次申请堆块即
main_arena_use释放掉,这样该堆块就会被放入unsortedbin中
- 在释放第三个堆块之后,我们再使用
malloc申请一个堆块,这个堆块的size位必须为0x70,这样我们才能将这个堆块通过fasbtin_attack从而申请到malloc_hook附近的堆块。
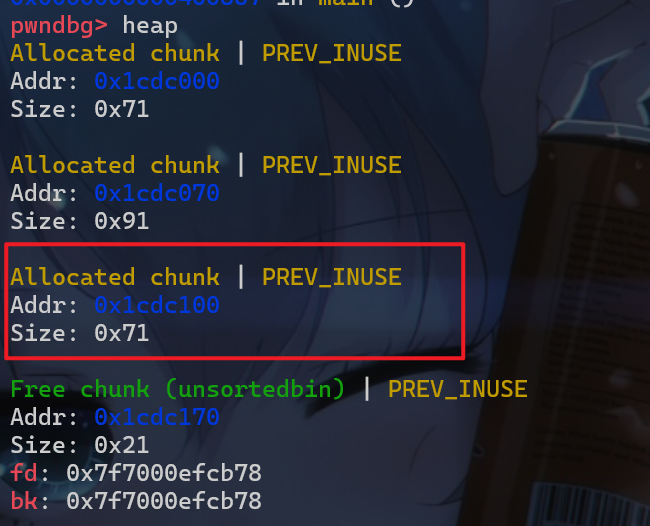
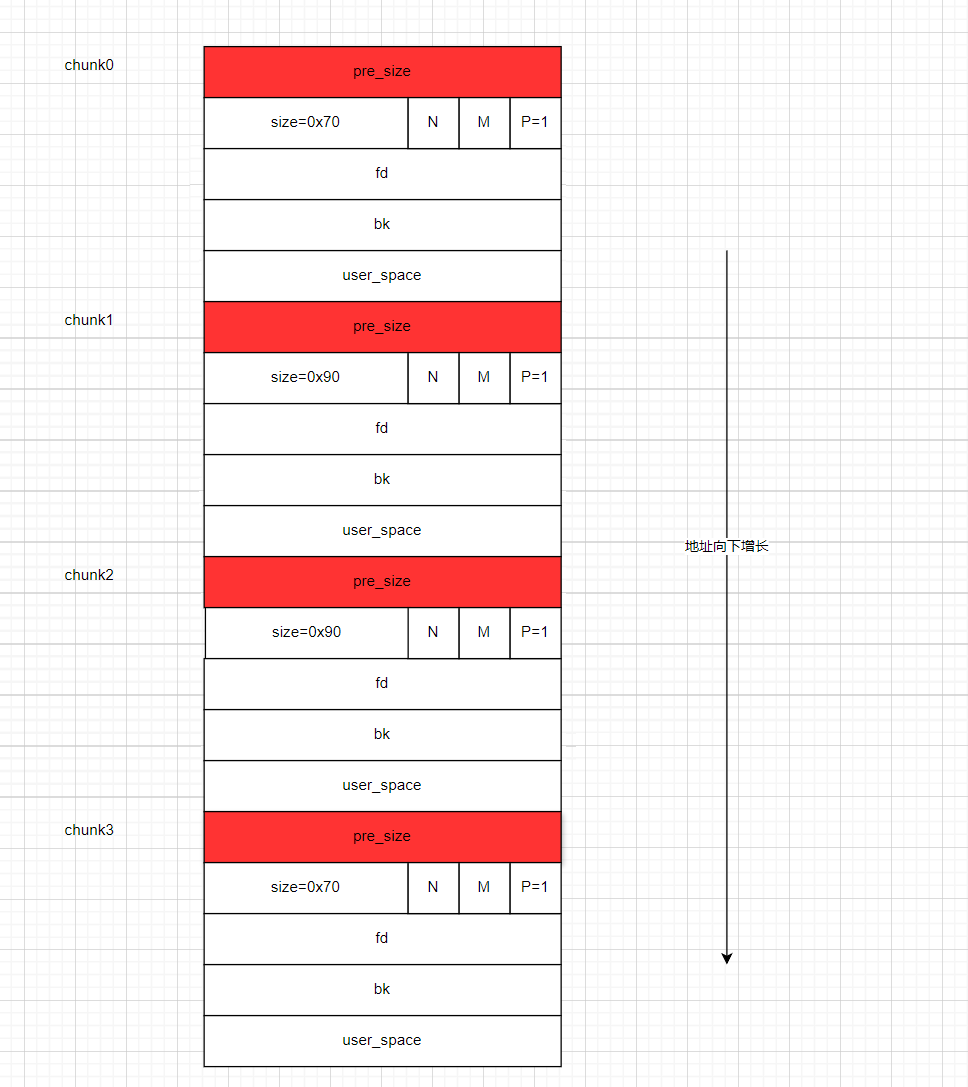
- 此时我们将
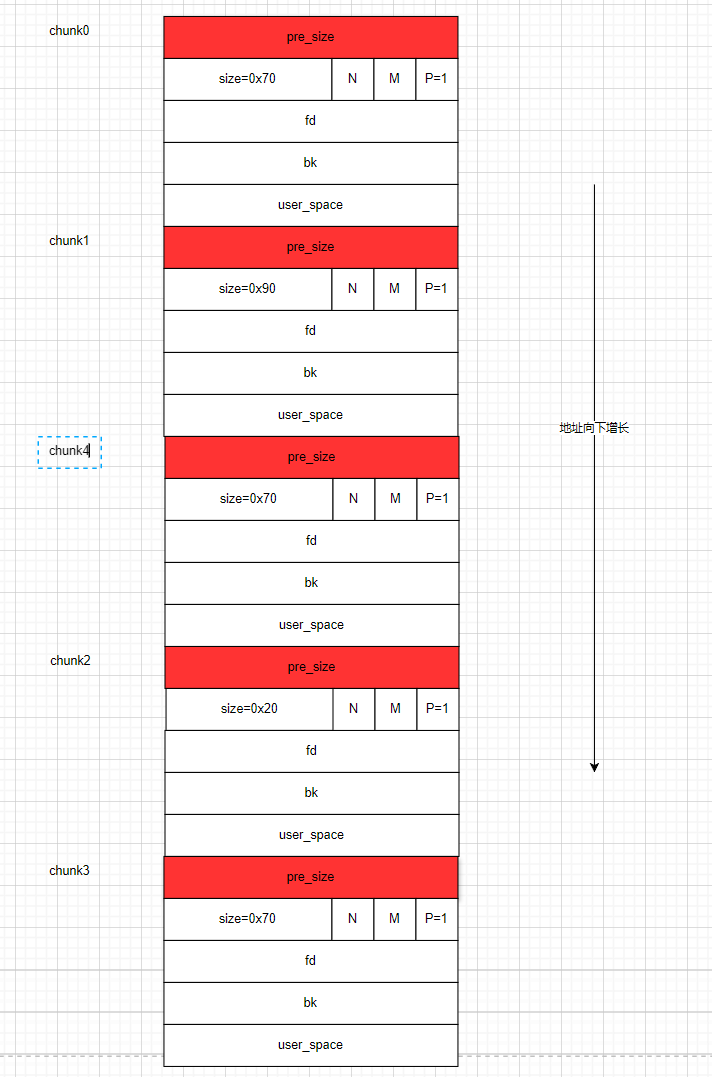
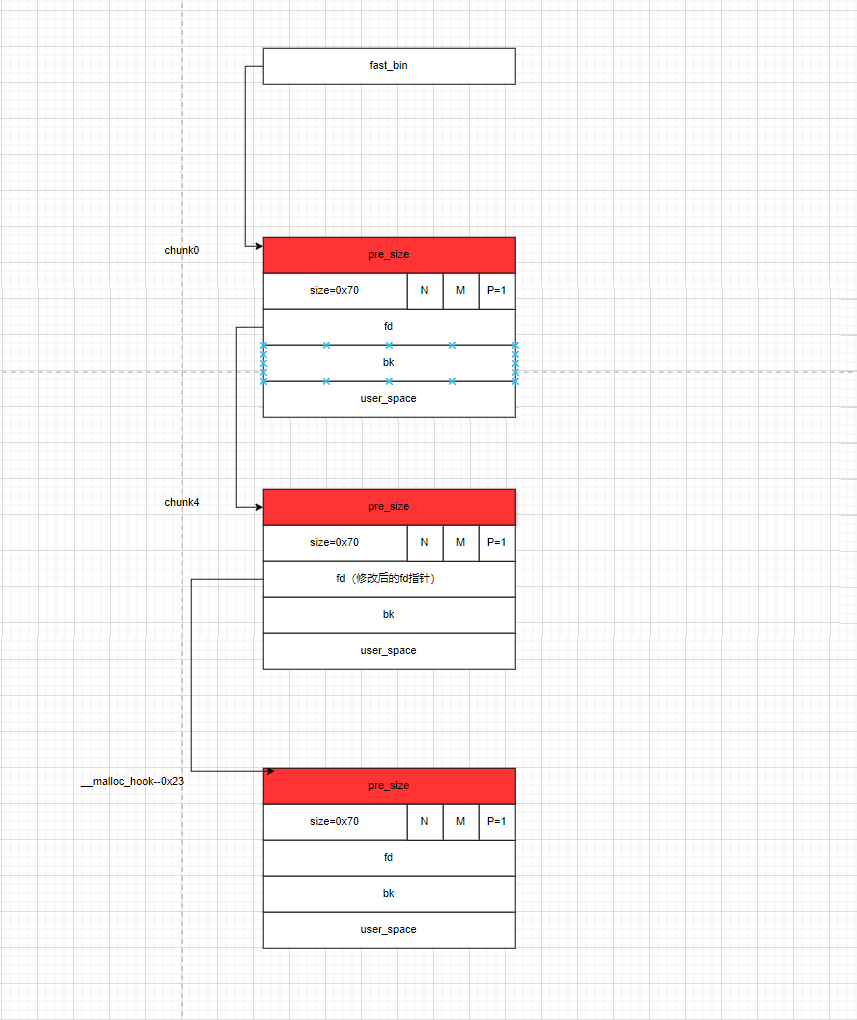
chunk3和chunk0,此时堆块的结构如下:
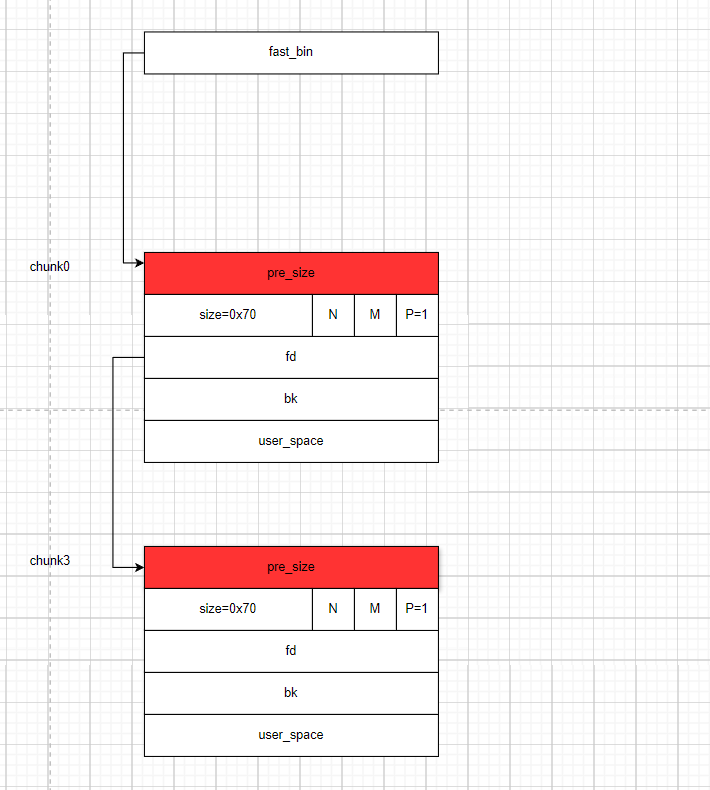
- 这时我们通过
UAF或者堆溢出的方式去修改fastbin_victim的fd指针,使其指向fake_libc_chunk而此时fake_libc_chunk这个堆块在之前我们将其申请来的时候并没有将其fd、bk指针设置为0或者填入其他垃圾数据,这样fastbin就形成了一个fastbin_victim-->fake_libc_chunk-->unsorted_bin这样的一个链表。
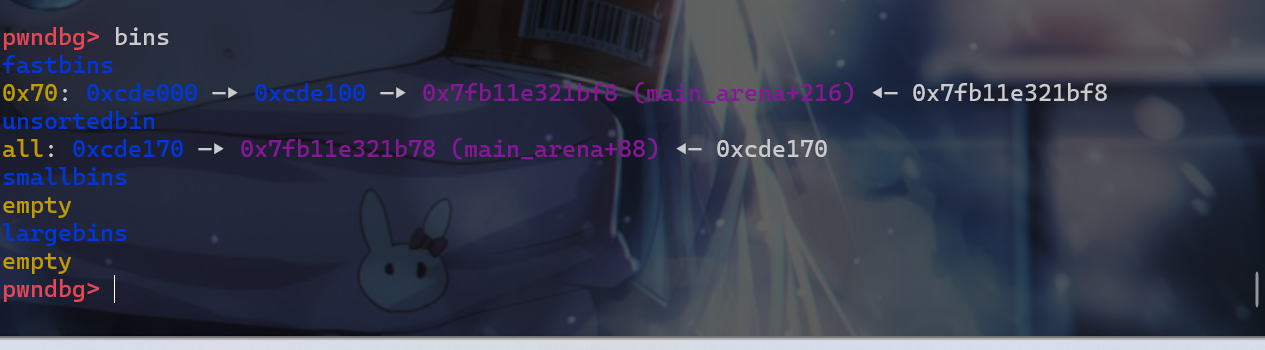
- 这时我们需要修改
fake_libc_chunk的最后16位使其指向__malloc_hook -0x23。此时由于内存分页机制,最后12位是固定的,在这里我们还需要爆破4位。在这个实验中,我们就直接修改成正确的地址。此时这边fake_chunk的size位为0x7f,这时我们在使用malloc从fastbin中将这个地址申请给用户的时候,就可以绕过对size位的检查。
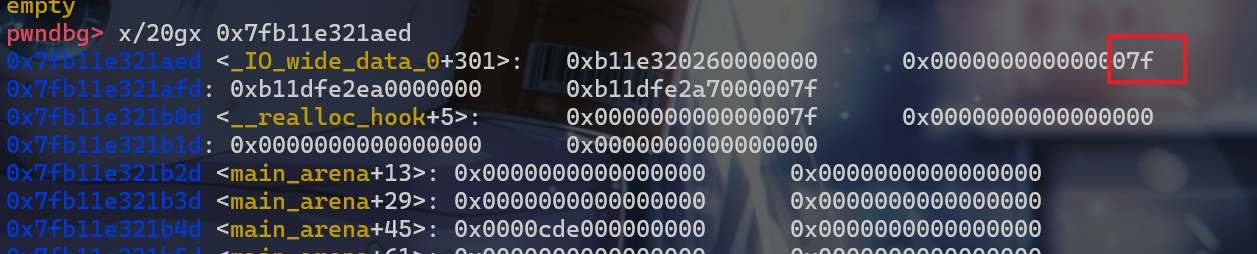
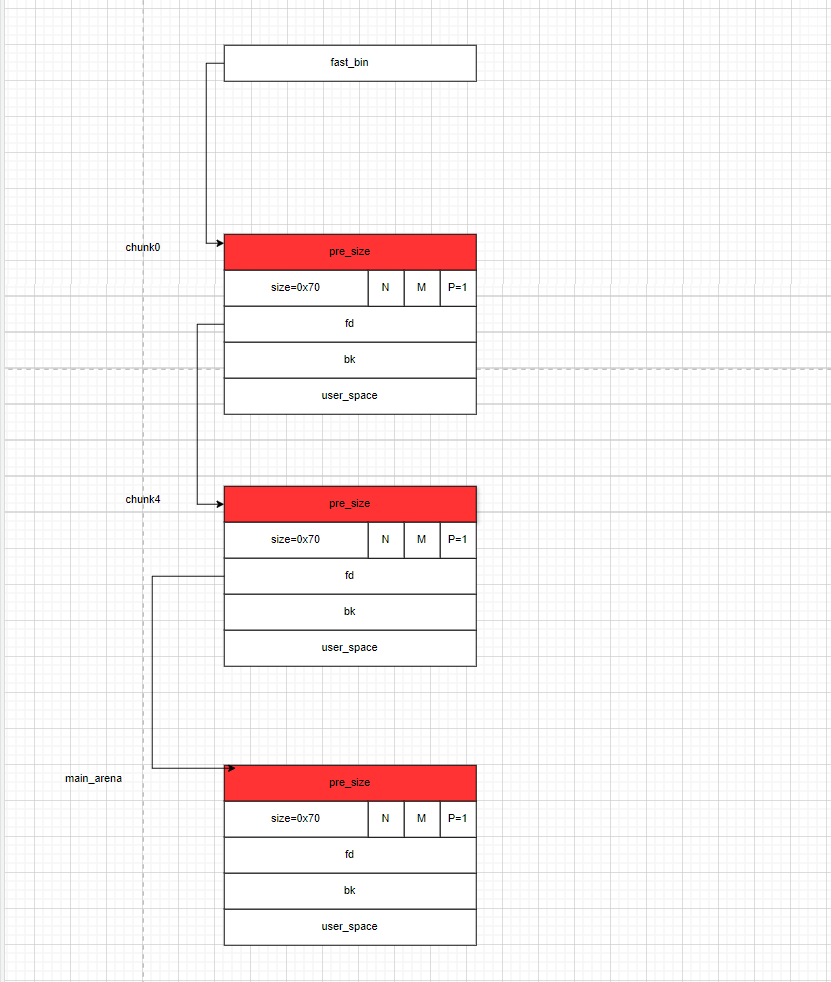
- 这样构造之后,我们再连续调用三次
malloc(0x60),在第三次调用malloc(0x60)时,其返回的地址就是在__malloc_hook附近。
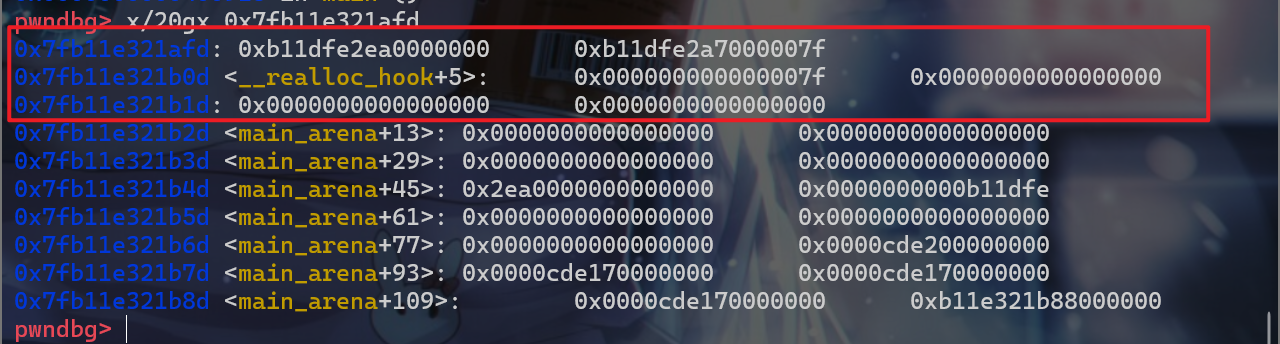
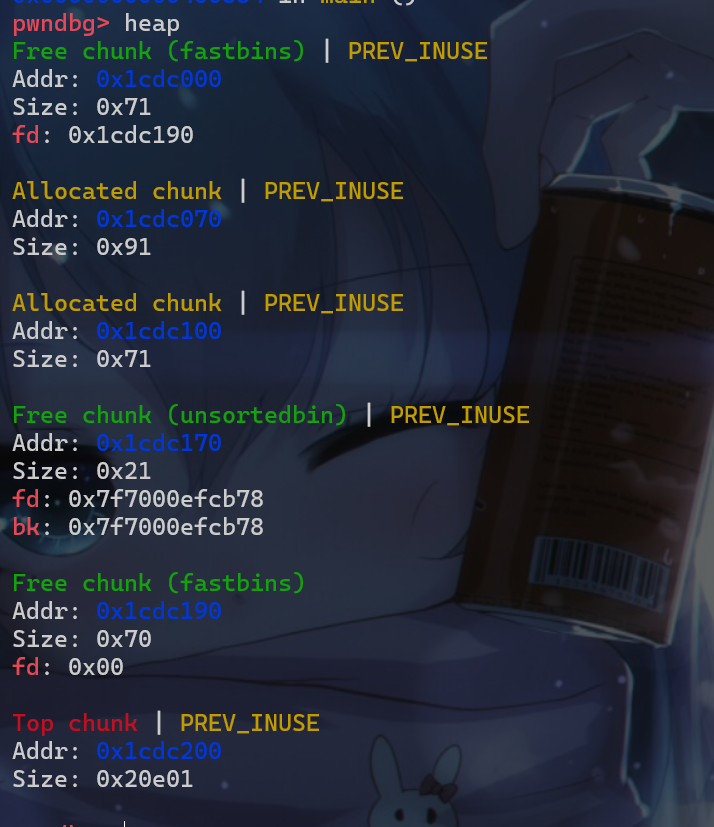
- 此时我们的堆布局是这样的
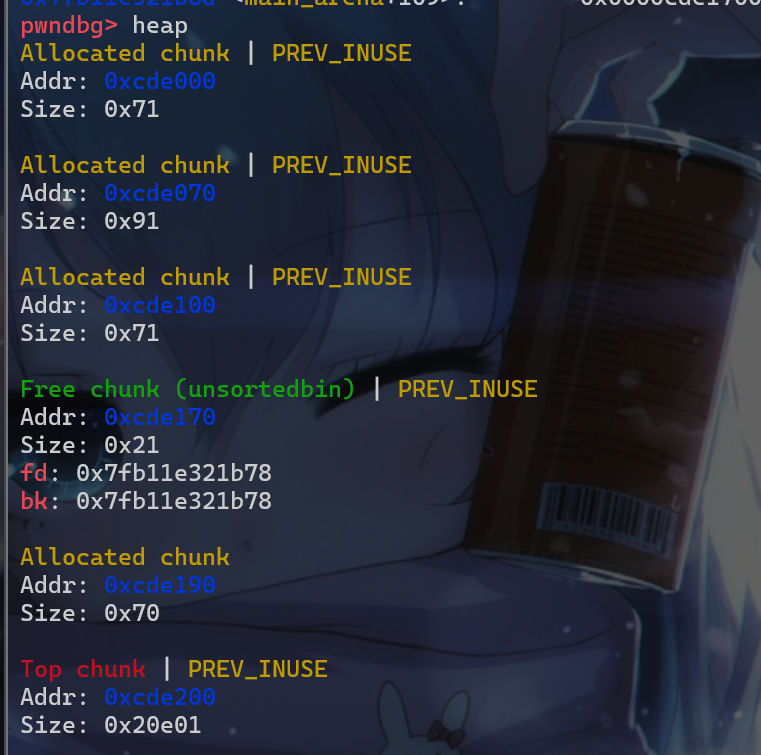
- 这时我们就可以对劫持
malloc_hook这个函数指针了,虽然我们能控制这个hook函数指针,但是我们不知道libc的地址,没办法写入system之类的地址,这时我们就需要进行第二步操作,先申请一个堆块malloc(0x80),这个堆块就用于unsorted_bin_attack的利用,此时我们还需要再申请一个堆块malloc(0x30),防止我们申请的0x80的那个堆块在释放后与top_chunk合并。 - 此时我们的堆块布局如下:
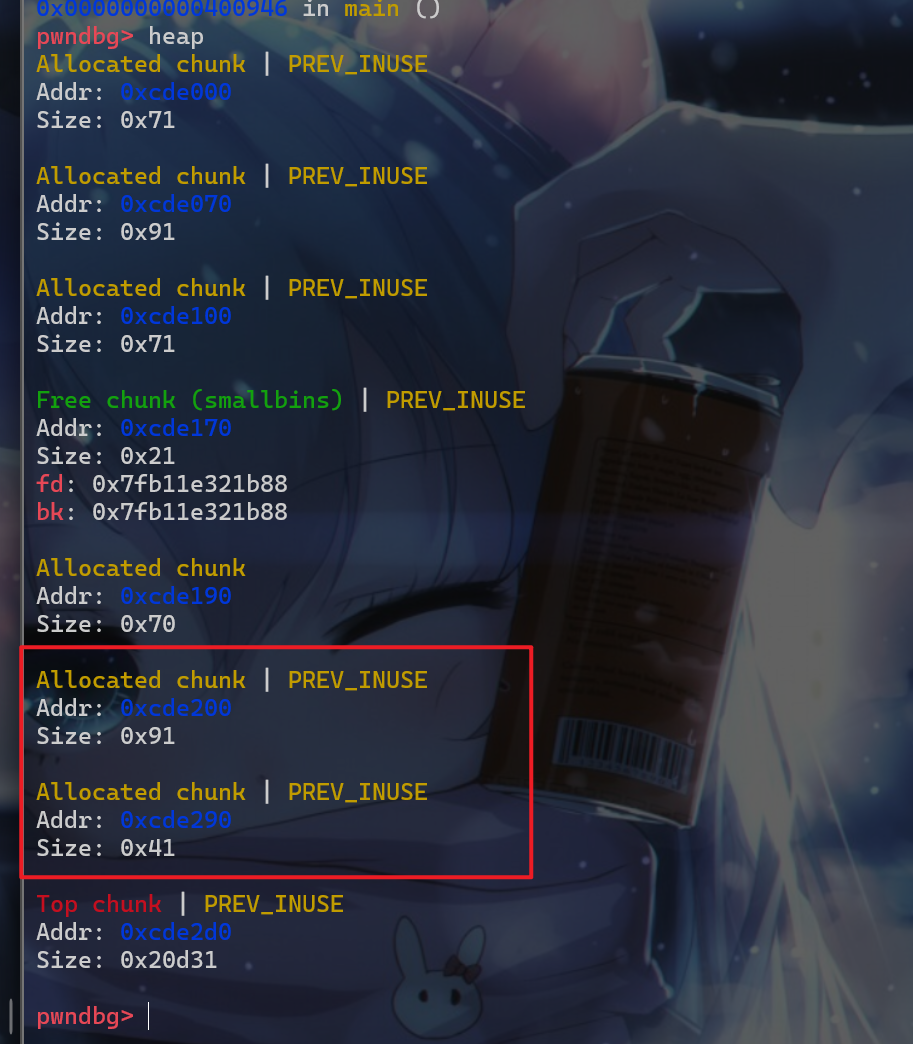
- 然后我们释放掉上图红色框部分中
size位为0x91的堆块,此时它就会被放入unsorted_bin中。
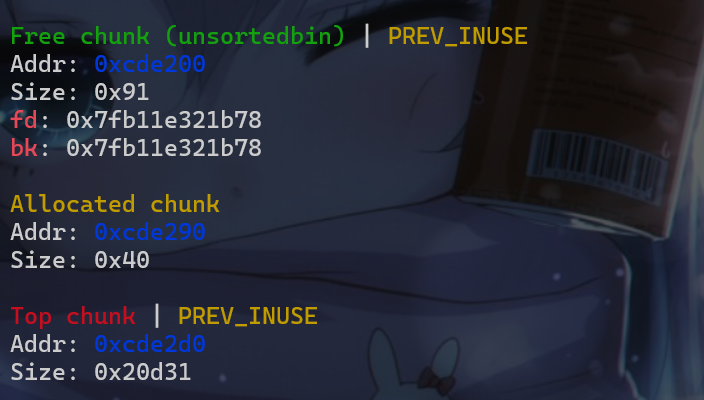
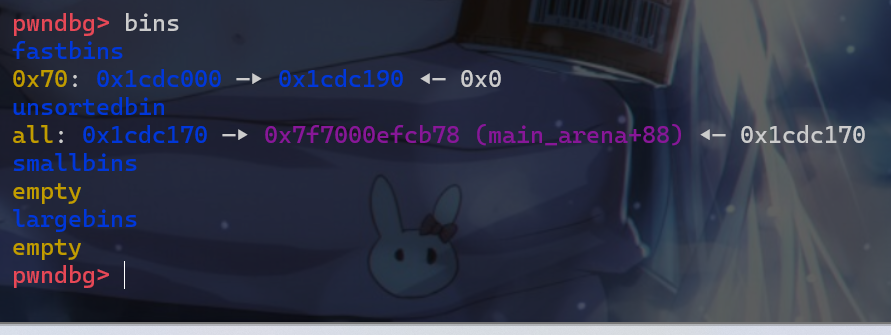
- 由于前面我们已经爆破出了
malloc_hook附件的地址,此时我们再劫持bk指针到malloc_hook附近就比较简单。此时我们修改这个堆块的bk指针
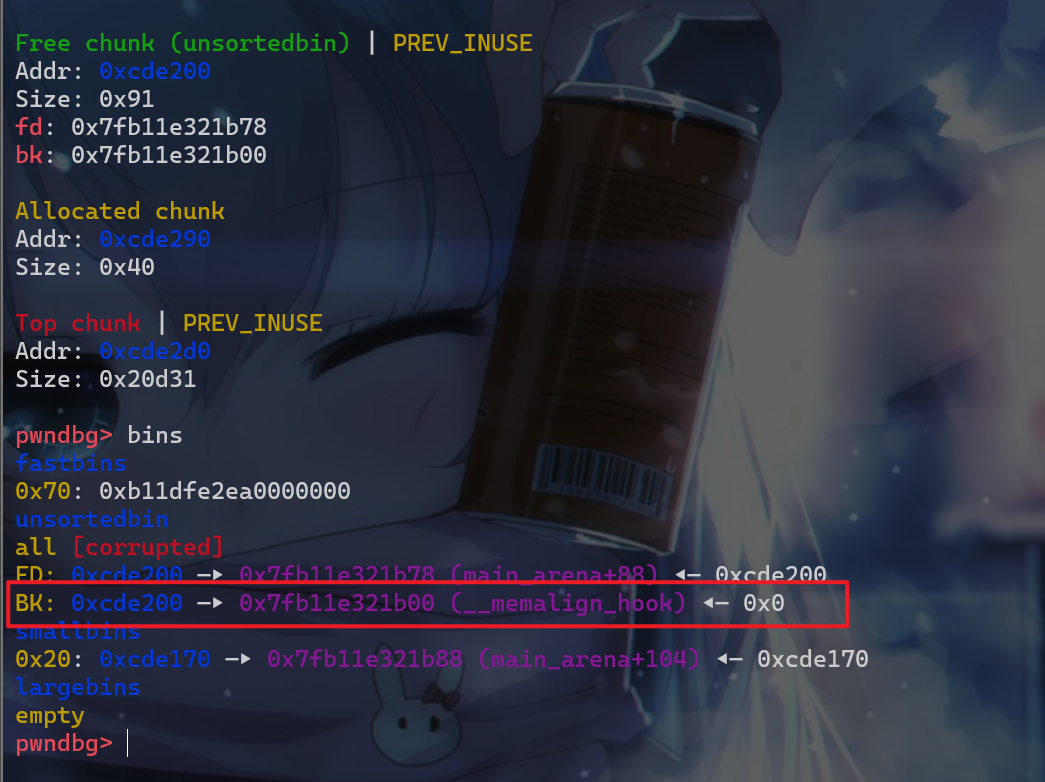
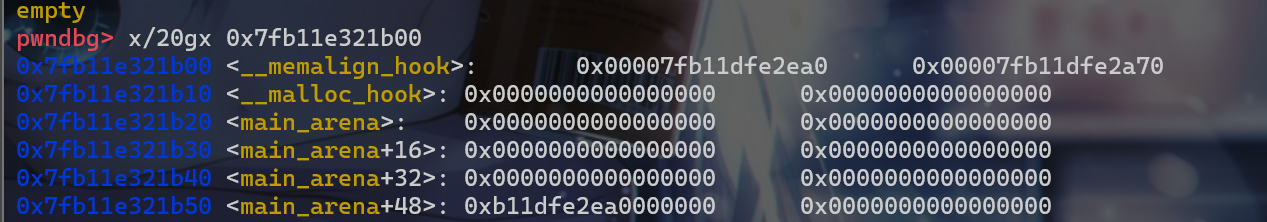
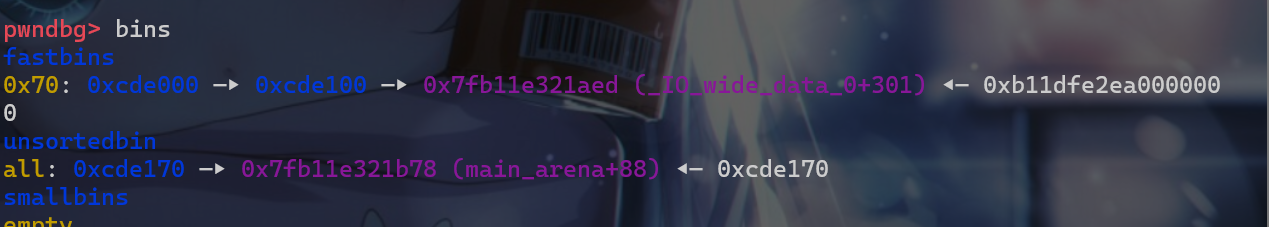
- 接下来就出发
unsorted_bin攻击,将__malloc_hook的值修改为main_arena+88这个位置
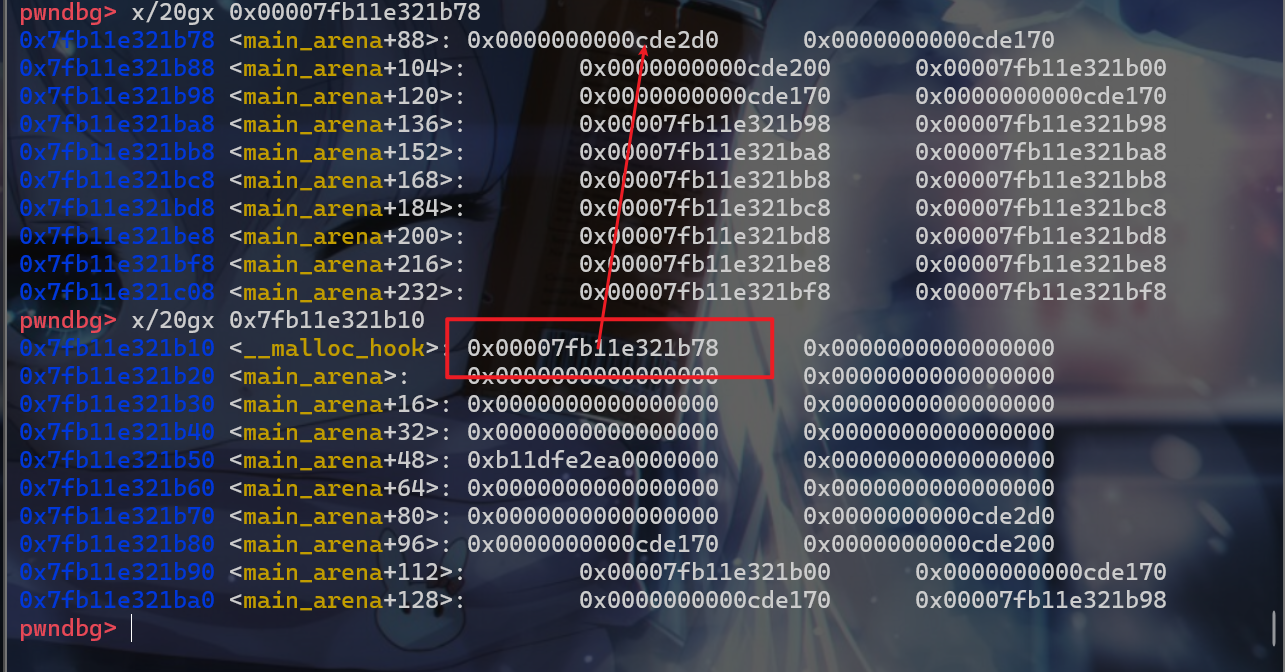
- 劫持到之后我们就需要进行爆破操作,现在先来看一看
system函数的地址将该地址与main_arena+88这个地址做比较。 - 发现
main_arena+88 = 0x00007fb11e321b78、system = 0x7fb11dfa23a0,此时system函数地址最小的12位是固定的,此时0x7fb11****XX,此时我们最后从小到大第12-16位已经在前面被爆破出来的,所以相当于已知0x7fb11***XXX,此时我们就还需要爆破12位的地址。
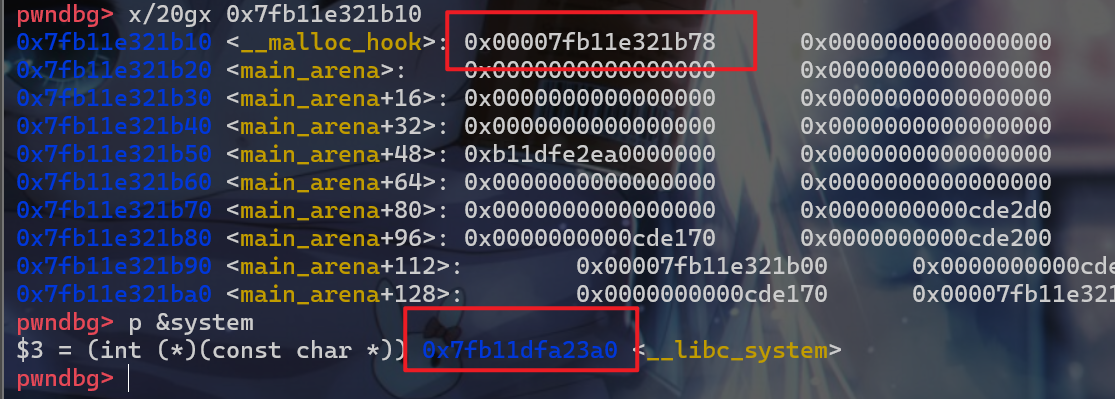
- 爆破出来后就
malloc_hook中的数据就变成如下:
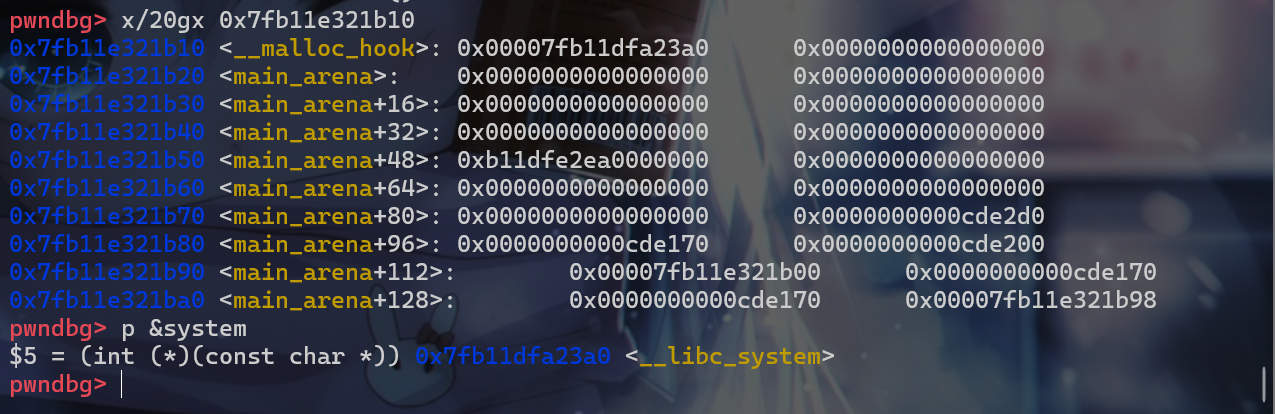
- 最后我们再申请一个
malloc(sh_addr)这样就可以执行system("/bin/sh")。最终getshell
利用方式
- 主要就是利用
fastbin attack使得我们能申请到malloc_hook附近的内存空间,从而可以对malloc_hook这个写入数据 - 之后利用
unsortedbin attack使得我们能修改malloc_hook的值为main_arena+88,之后利用fastbin attack申请到的重新写入和爆破部分位的地址,这样我们就能getshell了。
house_of_roman_level1
- 接下来我们来看一题,加深一下
house of roman这个组合技的使用。接下来我们先运行一下这个程序。首先这个程序会出现一个菜单
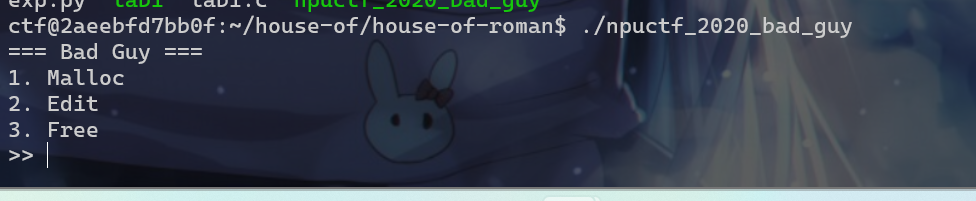
- 对于选项
1我们需要进行如下输入
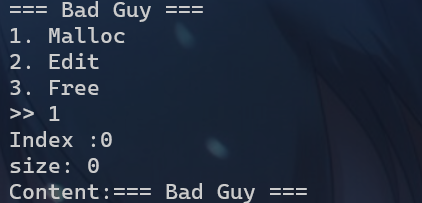
- 对于选项
2
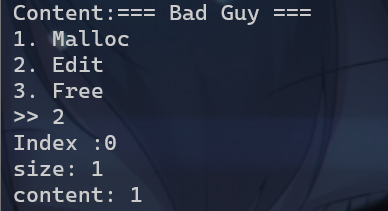
- 对于选项
3

level_1分析1
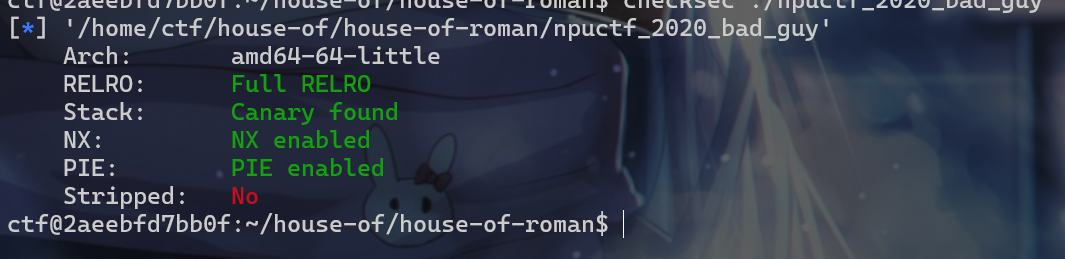
- 我们再查看一下保护机制,发现保护全开,但是符号表没有被去除。
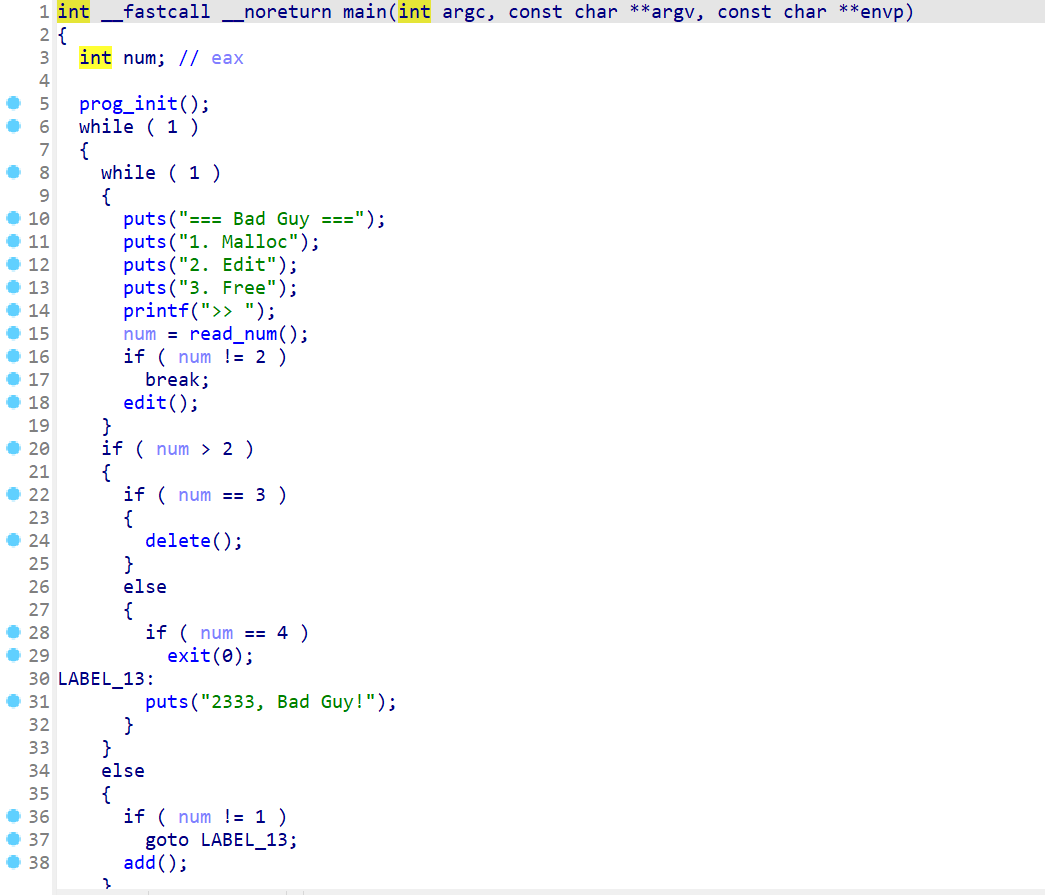
- 现在我们使用
IDA打开这个程序。查看main函数,发现main函数主要就是起到一个菜单的作用
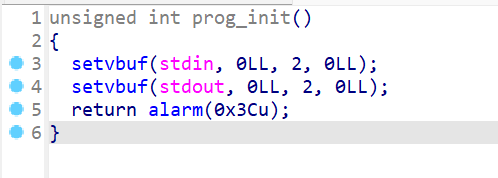
- 查看一下
prog_init这个函数,这个函数主要就是执行输入输出初始化,然后我们还会发现alarm(0x3C)
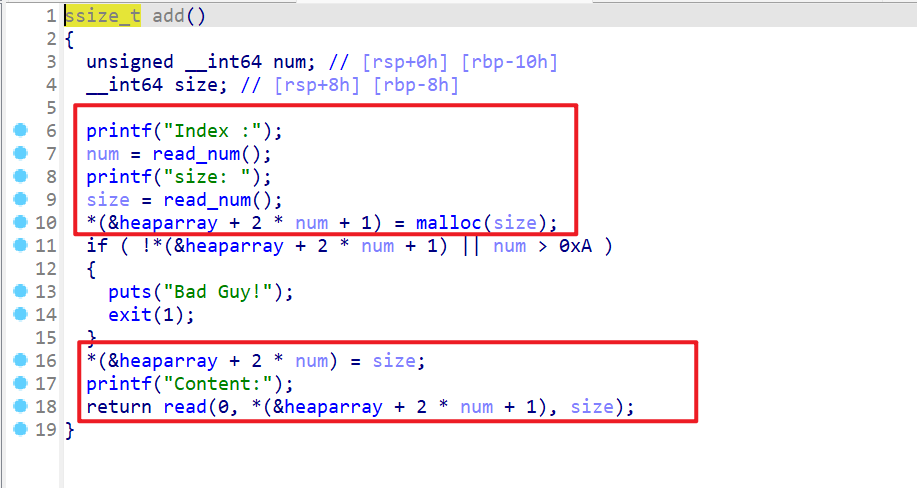
- 现在按照
增、删、改的顺序查看程序运行逻辑。- 发现该程序会申请用户指定大小的堆块,指定
heaparray这个位置的索引处 - 并且把堆块的大小存储在
heaparray[2*num]这个位置,将heaparray[2*num+1]这个位置存储着malloc()返回的地址。
- 发现该程序会申请用户指定大小的堆块,指定
- 这个函数会释放用户指定索引的堆块,并且释放堆块后会将堆块设置为
0
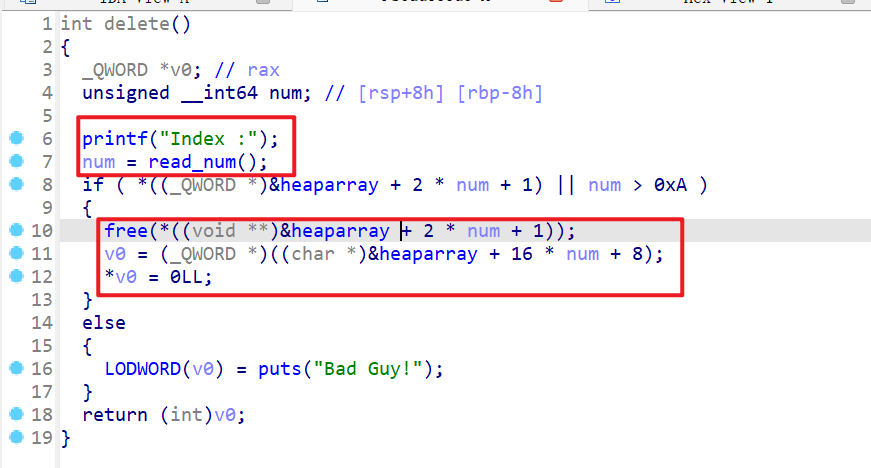
- 查看
edit()函数:- 发现该函数能修改用户指定堆块,指定修改大小这里存在堆溢出的漏洞
- 这时我们就还会
count这个变量会限制我们修改的次数。
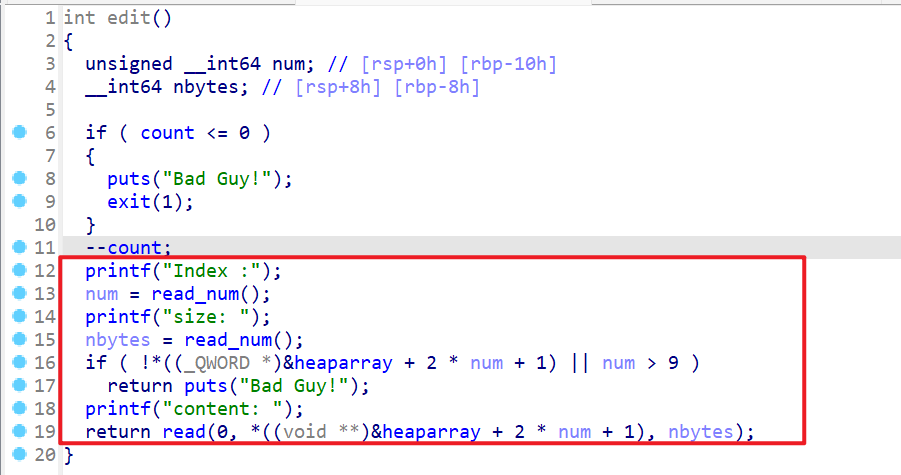
- 我们现在来查看一下全局变量,发现全句变量就只有
heaparray。
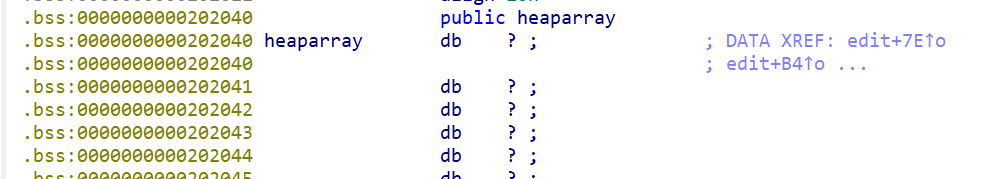
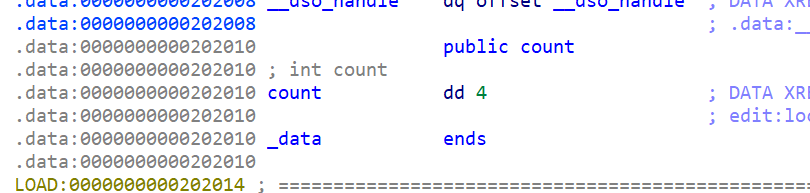
- 并且发现
count这个变量为4
level_1分析2
- 接下来我们先写一下
exp的交互部分。
1 | from pwn import * |
level_1分析3
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 iyheart的博客!

