GPNCTF2025复现
碎碎念
对于写WP个人的见解:
对于一些比赛,虽然有写wp,但是其实本人是想着一个方向或者多个方向复现完再发的,但是这比较困难,因为每个比赛的每个方向题目都是有简单、有困难的。简单的题目还好,可能一下子就复现完了,但是剩下的比较困难的题目就很难受了可能会因为知识储备不足而无法自己独立做出。虽然说是有wp可以看,但是看wp的目的是能学到东西,而不是利用脚本一把梭一下。
所以在复现比赛题目的时候往往对自己要求比较高,而遇到难的短时间复现不了,时间一长好像就把题目鸽了(老毛病了)QAQ。这就导致我写的wp感觉还是比较少的。并且一些比赛题目是用AI一把梭的(AI一把梭的根本学不到东西),对于这种情况我是更希望复现完了再发wp的。
对于CTF中使用AI的一些碎碎念:
高中物理老师说过,考试是考试,考试要有考试的技巧;平时刷题就要踏踏实实的刷题;考试过后对于试卷的题目也是需要踏踏实实的。
而CTF比赛其实某种程度上也相当于考试吧,而大部分CTF比赛都允许使用AI的,这就导致在比赛中使用AI就相当于一个考试的技巧,黑猫白猫抓到老鼠的都是好猫——能解出题目的AI就是好AI(哈哈哈哈)。这就导致了大部分人遇到题目就会直接把题目附件之类的直接丢给AI一把梭(包括我自己)。
所以这个暑假就期间就已经开始反思了,就觉得AI一把梭是真学不到东西,赛后也是一鸽再鸽,所以干脆在平时的CTF比赛中减少AI一把梭的次数,并且拿到题目附件的时候并不是第一时间丢给AI,而是认认真真的看懂代码,对于代码中不明白的部分再去询问AI(这样总比直接复制粘贴丢给AI能学到东西),只有实在没思路的题目还是需要AI一把梭的(毕竟CTF是个竞赛,还是个团队协作的比赛,都能用AI一把梭的但是你不会,也只能先使用AI一把梭把flag梭出来再说了)。
Crypto
hinting
- 题目附件如下:
1 | import secrets |
- 这题其实也是类似于
p异或q的题型,都是通过剪枝搜索,但是应该如何搜索,应该从多项式乘法入手。目前已知p、q的七进制位,将它们俩个用多项式表示如下:
- 这时展开来可以发现:
- 此时我们可以发现,由
a_0*b_0其实就可以确定n的最低1位,而已知a_0、b_0、a_1、b_1就可以已知最低的2位,以此类推知道多少位就能已知多少位一直到最高位。这其实就类似于p^q的低位搜索,只不过将二进制换成了七进制。所以正常DFS剪枝搜索即可。(猜想:可能可以从高位和低位进行中间相遇)
1 | import libnum |
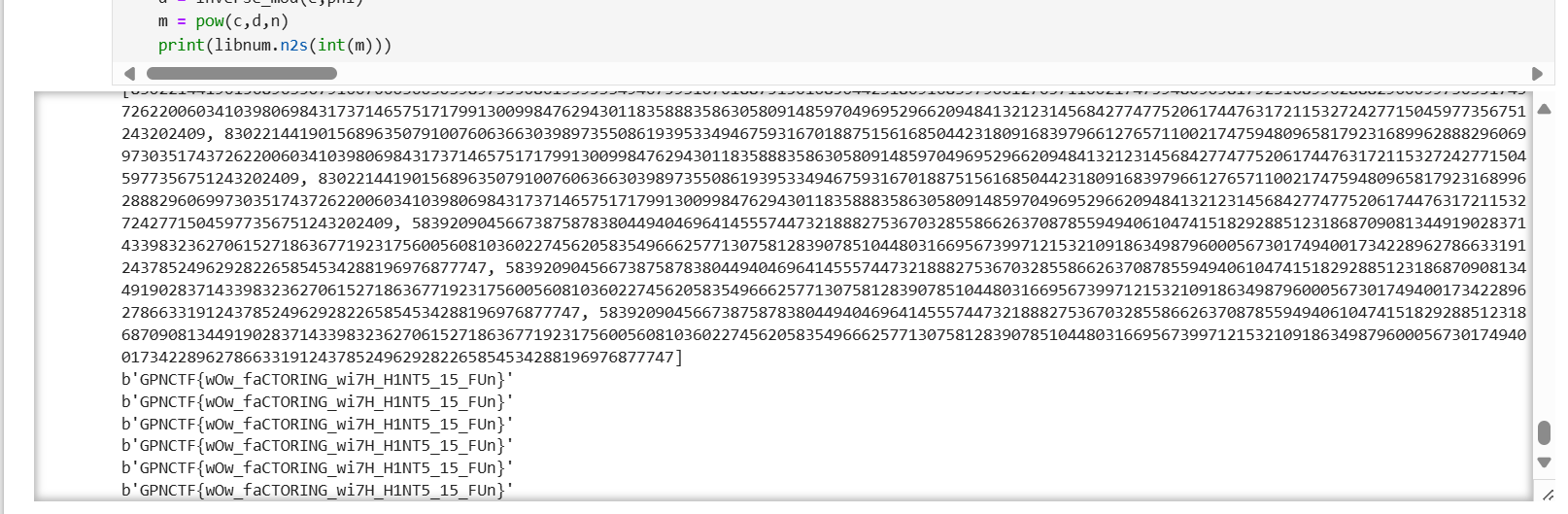
restricted oracle
- 从这题了解到了
CBC块加密模式有一个攻击为padding Oracle攻击,稍微改了一下这题的代码,使得爆破次数没有限制,从而学习了一下padding Oracle攻击。基本版的padding Oracle攻击的学习过程写在了这篇博客中:块加密工作模式 | iyheart的博客 - 题目附件如下:
1 | from Crypto.Cipher import AES |
- 首先需要接收消息,并从消息中分离数
vi和密文
1 | from pwn import * |
- 之后就是爆破出
padding的个数
1 | padding = 0 |
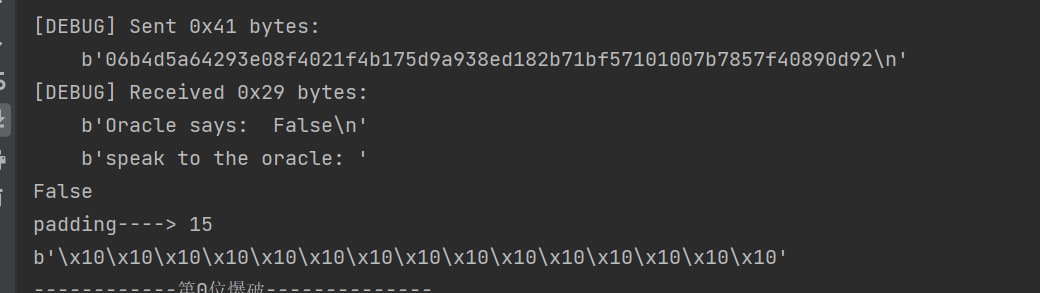
- 尝试爆破最后一块剩余没有被
padding填充的部分,会发现爆破出来的,字母目前只有大写字母和小写字母。
1 | # 破解尾块的数据 |
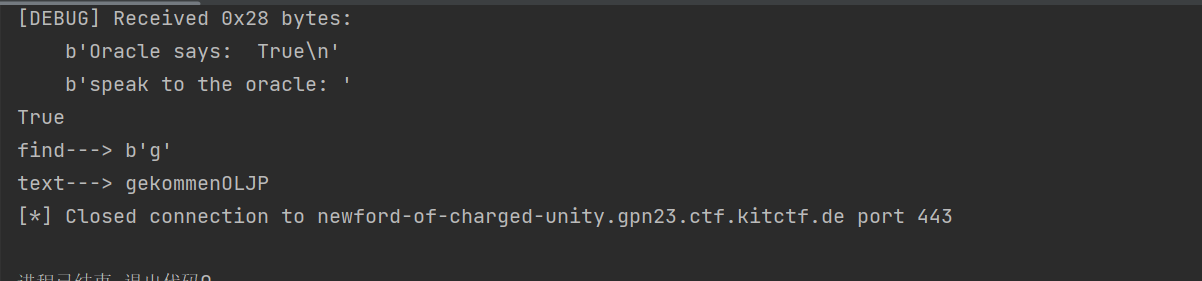
- 但是由于有限制次数,而题目中又给了
key是大小写字母,所以我们可以构造如下列表,用于减少爆破次数
1 | # 建立一个列表,用于爆破使用,爆破只选择对应对应索引与字母的异或值,从而减少爆破次数 |
- 减少次数后就可以在有限次数绕过爆破出
key,在爆破的时候还需要考虑一下时间问题,明文非常长,但是靶机只有30分钟的限制。但是在爆破的过程中会发现明文是德国新闻的一些句子。
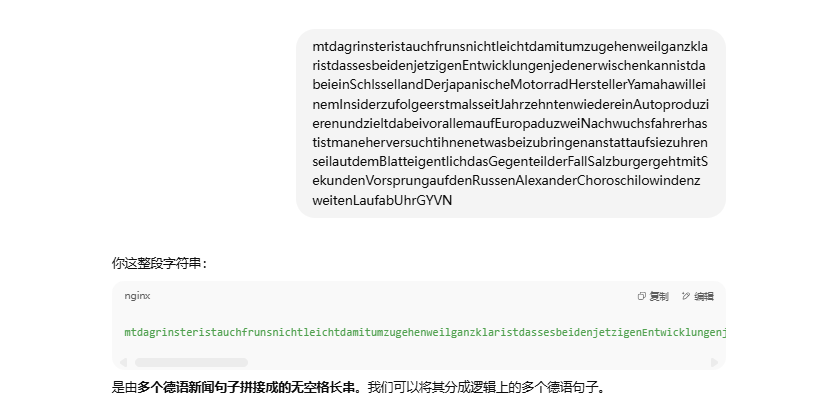
- 这就需要对单词进行词频分析,从而减少爆破的时间,并且还发现,每次连接发送过来的块长度不一样,有的块长度到达了
60多,有的才30多或者40多,所以我们应该选择40多、30多块的来进行爆破,这样也能节省时间。这样能使得平均每块爆破时间降低到38.07秒
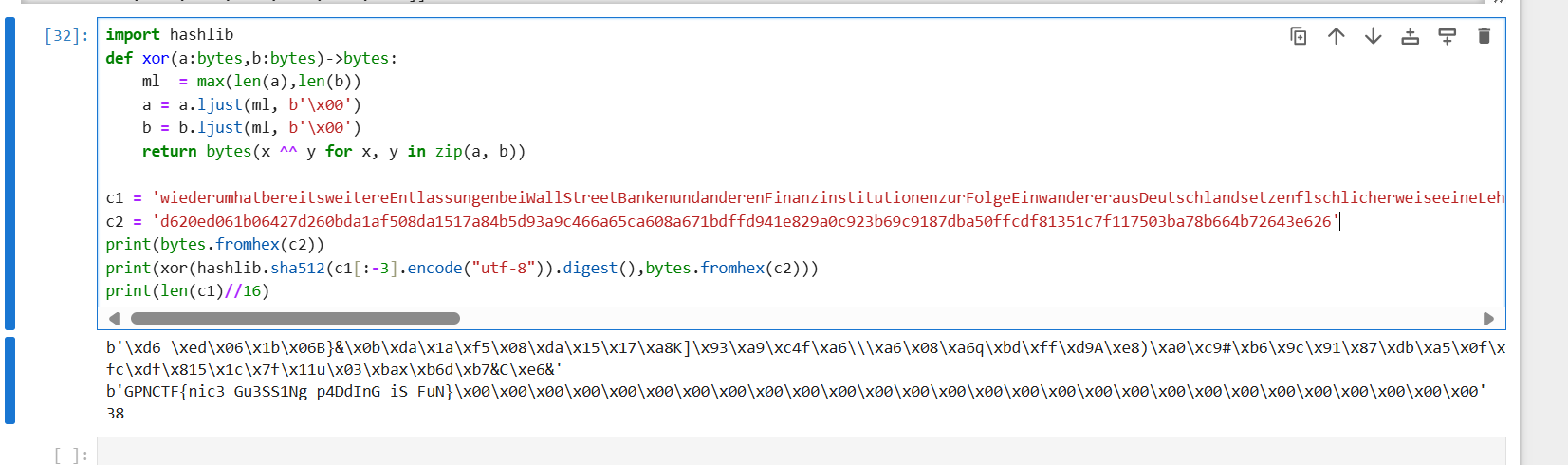
- 爆破出来
text后再去掉最后的大写字母,即可得到结果
1 | import hashlib |
- exp如下:
1 | from pwn import * |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 iyheart的博客!

